LinkedIn Breach Data Used For Malicious E-Mails
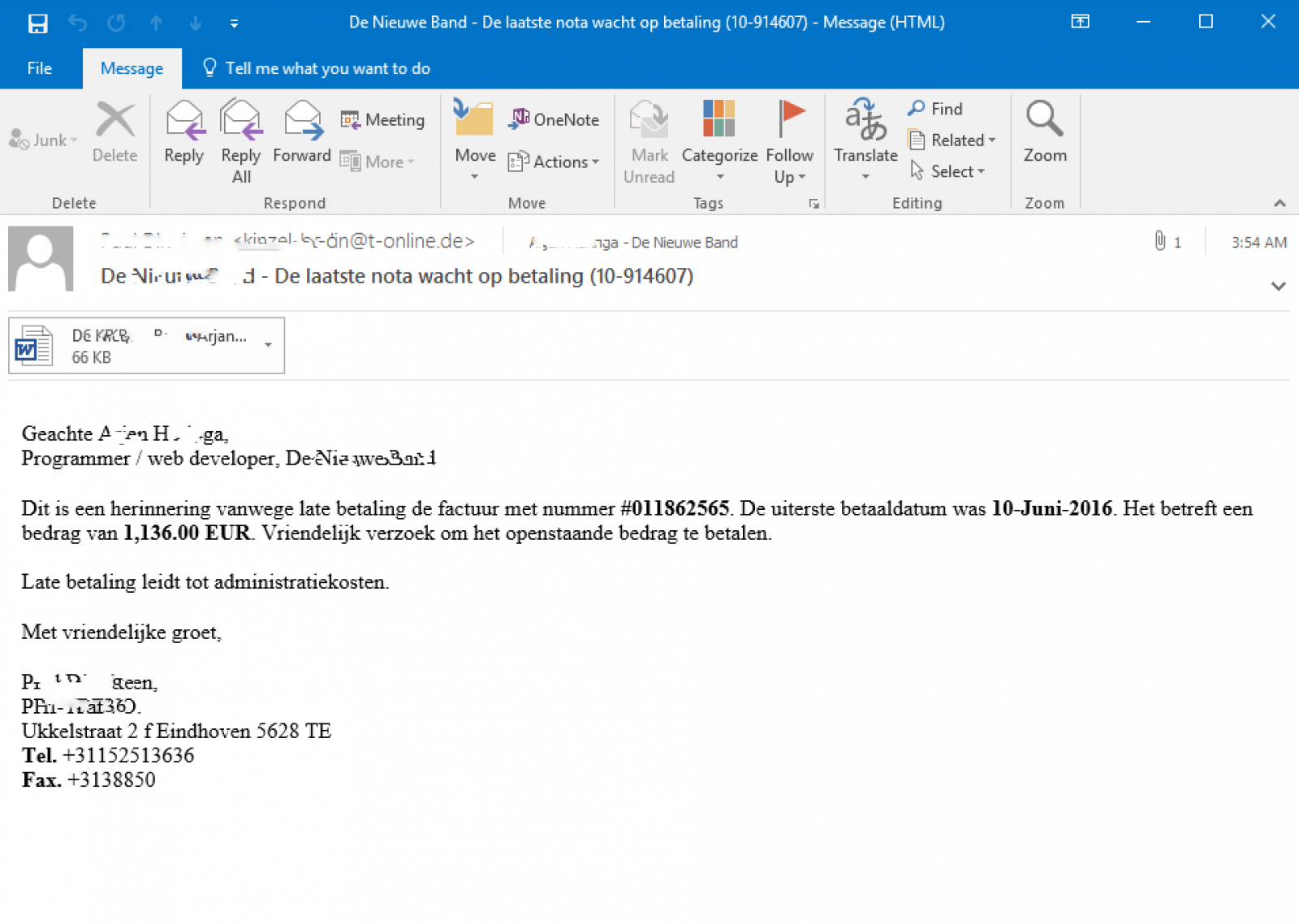
Yesterday, the German federal CERT (CERT-BUND) warned of phishing e-mails that are more plausible by using data that appears to originate from the recently leaked LinkedIn data set. The e-mail address the recipient by full name and job title. Typically, the attachments claim to contain an invoice.
We have since received a couple of users who reported receiving e-mails that match the pattern. For example:
(Thanks to our reader Arjan for the sample)
The e-mails arrive in different languages. They address the recipient by full name, job title and company name, to make the e-mail more plausible.
This is similar to the way social media was used in the past to create more convincing phishing e-mails. For example, see this old article from 3 years ago about how Facebook data is used in this way. With the LinkedIn leak, data has become available that wasn't reachable by simple screen scrapers (or API users) in the past.
| Application Security: Securing Web Apps, APIs, and Microservices | Las Vegas | Sep 22nd - Sep 27th 2025 |



Comments