Failed Malspam: Recovering The Password
Jan's diary entry "One way to fail at malspam - give recipients the wrong password for an encrypted attachment" got my attention: it's an opportunity for me to do some password cracking :-) I asked Jan for the sample.
Just like Jan noticed, I saw that the sample is not actually a 7zip file, but a ZIP file. This could be a mistake by the malware authors, or it could be deliberate: 7zip is able to decompress a ZIP file with extension 7z.
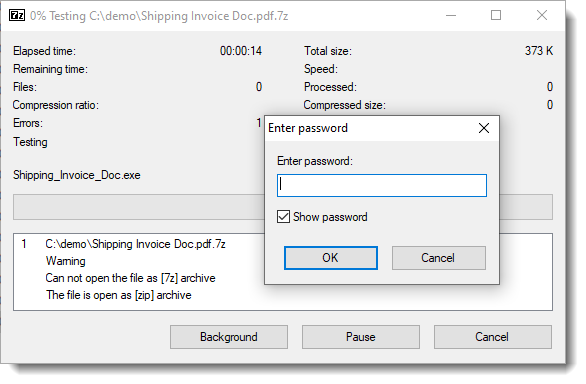
And I confirm that AWB3604 is not the password.
Since it's a ZIP file, I first used my zipdump.py tool: it has a leightweight password cracking feature.
But that did not help:
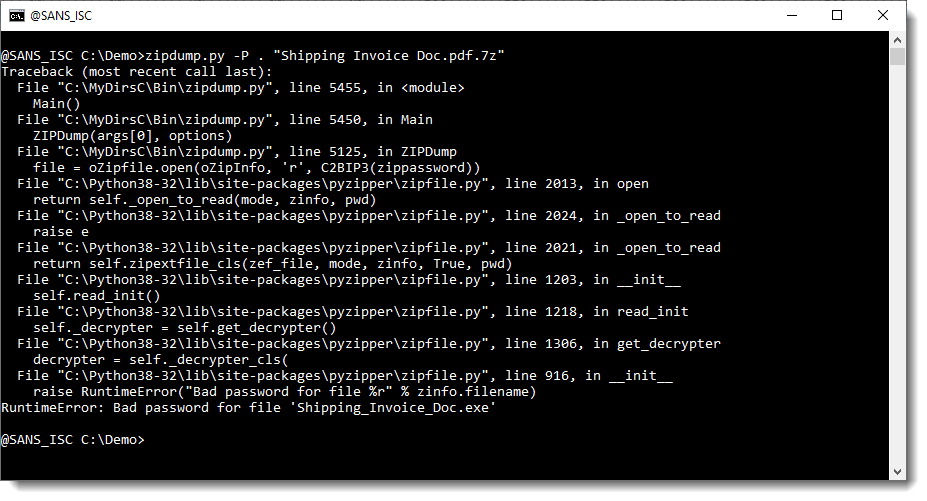
Then I turned to John the Ripper. I used zip2john to create a hash for the sample, and created a password list file with a single line: AWB3604. And then I let JtR use all of its built-in rules on this "dictionary":
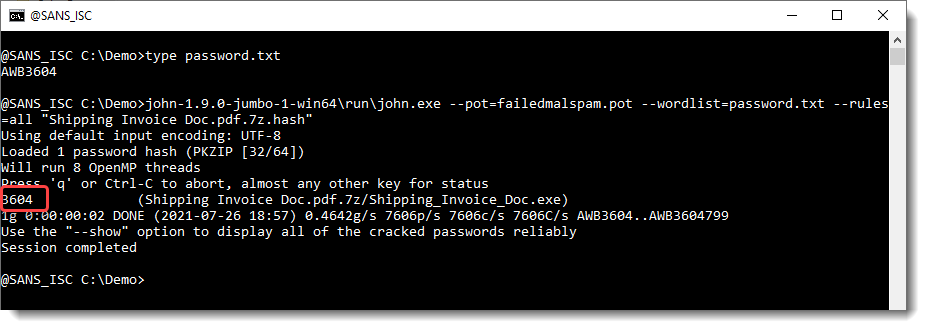
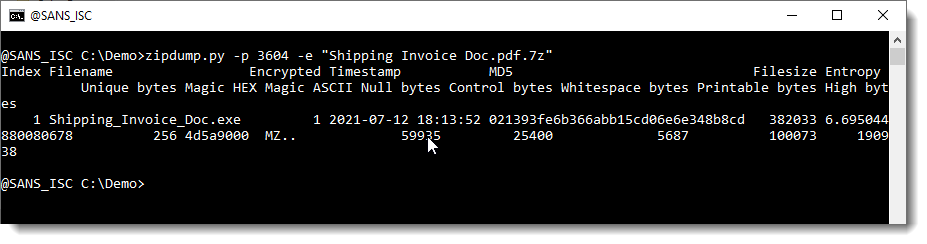
One of JtR's rules transformed the presumed password AWB3604 into 3604, and that turned out to be the actual password.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com

Comments