Exploit kits (still) pushing Teslacrypt ransomware
Teslacrypt is a form of ransomware that was first noted in January of this year [1]. This malware apparently targets video game-related files [2, 3, 4]. I've seen Teslacrypt dropped by the Sweet Orange exploit kit (EK) [5], and it's also been dropped by Nuclear EK [6]. McAfee saw it dropped by Angler EK last month [2].
I saw it again on Wednesday 2015-04-15 from Nuclear EK. Let's take a look at the traffic. The image below from Wireshark shows Nuclear EK traffic being generated from a compromised Wordpress site. Nuclear is hosted on a myftp.org domain. You can also see some of the traffic generated by the user interacting with the ransomware.
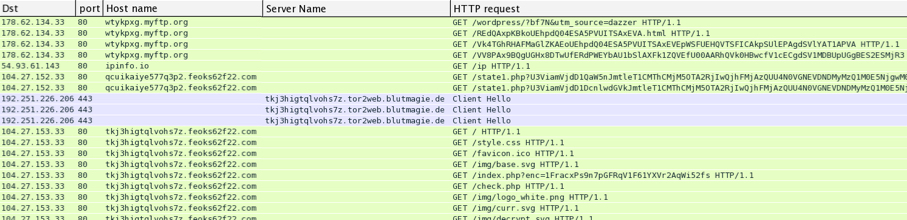
Shown above: Wireshark display on some of this infection traffic. Click on the image above for a larger image.
A pcap of the above traffic is available at: http://www.malware-traffic-analysis.net/2015/04/15/2015-04-15-Nuclear-EK-sends-Teslacrypt.pcap
Nuclear hasn't changed dramatically from the last time we looked into it in December 2014 [7]. The traffic patterns are very similar. The image below shows the beginning of the landing page for this infection traffic:
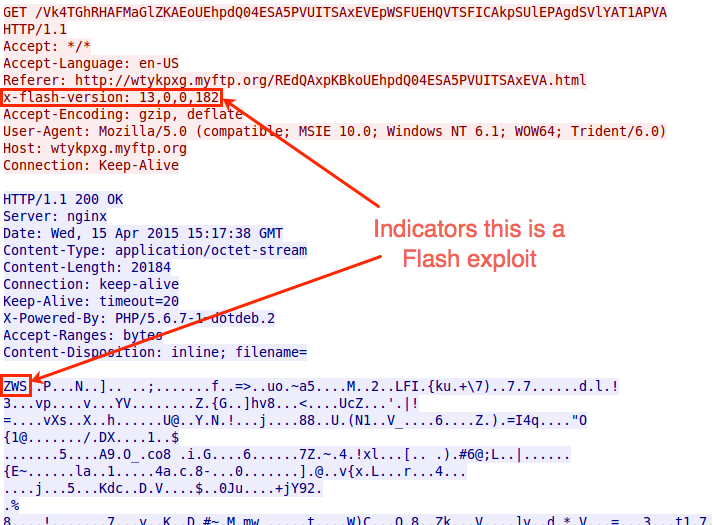
Next, Nuclear EK sent a Flash exploit. The image below, taken from a TCP stream in Wireshark, shows the vulnerable host was running an out-of-date version of Flash player, 13.0.0.182.
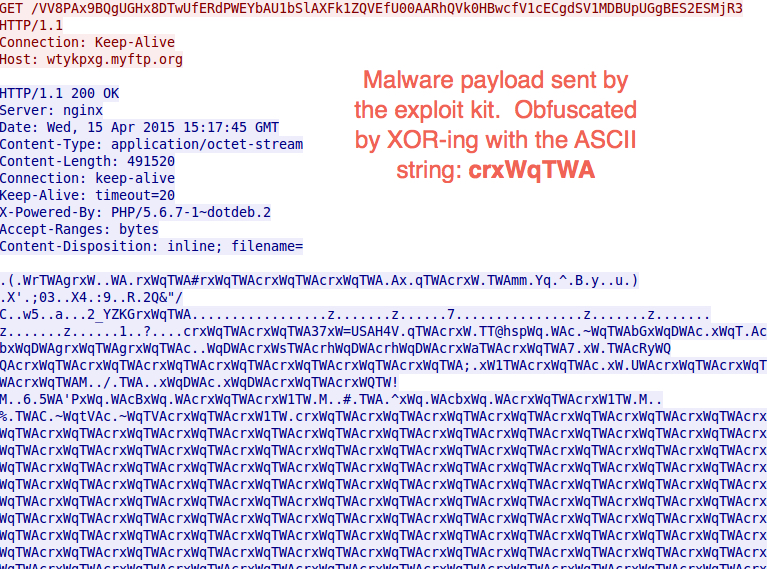
Finally, Nuclear EK sent the malware payload. Like last time, Nuclear EK obfuscated the payload by XOR-ing the binary with an ASCII string. In this case, the ASCII string is crxWqTWA
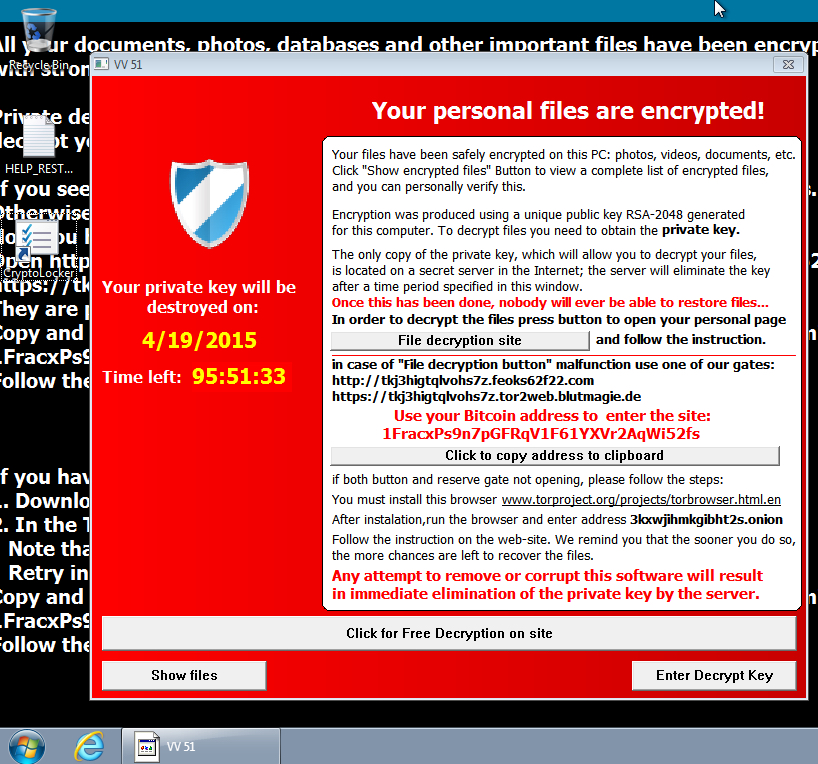
Here's what the desktop of the infected host looked like:
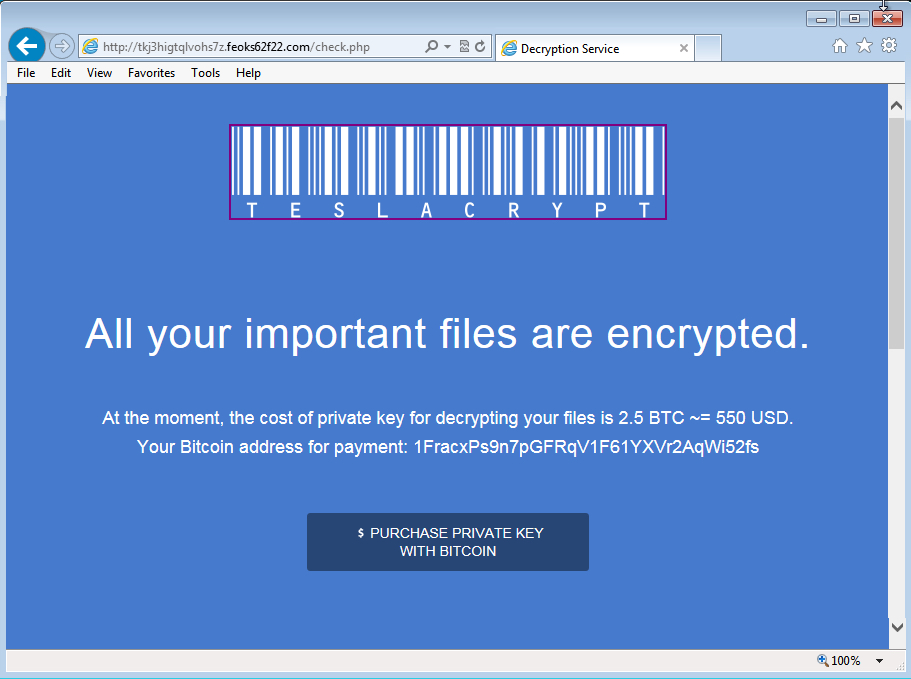
And here's the browser window that appeared when the user looked into making a ransom payment:
The bitcoin address for the ransom payment is: 1FracxPs9n7pGFRqV1F61YXVr2AqWi52fs
When I first checked, no transactions had been made to that bitcoin address. Don't know if that's still the case, but anyone can check here: https://blockchain.info/address/1FracxPs9n7pGFRqV1F61YXVr2AqWi52fs
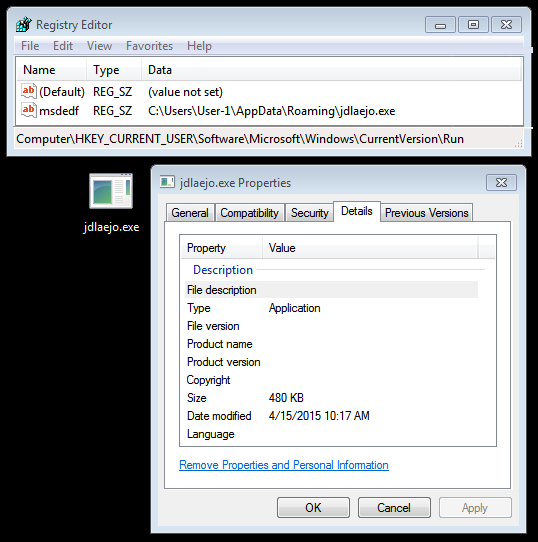
The image below shows where the malware payload copies itself. It also the registry key updated to keep the malware persistent on the system. This malware is available on malwr.com at the following link: https://malwr.com/analysis/ZTQ2NDc1NWY2ZjRmNDkwNDgyMjFlZDNhZGY0ZWJhMjA/
Snort signatures (Cisco/Talos) that triggered on the Teslacrypt traffic:
- [1:33893:1] MALWARE-CNC Win.Trojan.TeslaCrypt outbound communication
EmergingThreats and ETPRO signatures that triggered on the Teslacrypt traffic:
- ET TROJAN Win32/Teslacrypt Ransomware HTTP CnC Beacon M1 (sid:2020717)
- ET TROJAN Win32/Teslacrypt Ransomware HTTP CnC Beacon M2 (sid:2020718)
- ETPRO TROJAN Win32/Teslacrypt Ransomware HTTP CnC Beacon Response (sid:2810074)
If your computer becomes infected with Teslacrypt, what should you do? Those files may be lost if you don't have a backup. Even if you pay the ransom, there's no guarantee you'll receive the decryption key.
As always, your best defense is regularly backing up your data. If not, you could find yourself at the mercy of this (or other) ransomware.
---
Brad Duncan, Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://nakedsecurity.sophos.com/2015/03/16/teslacrypt-ransomware-attacks-gamers-all-your-files-are-belong-to-us/
[2] https://blogs.mcafee.com/mcafee-labs/teslacrypt-joins-ransomware-field
[3] http://www.bleepingcomputer.com/forums/t/568525/new-teslacrypt-ransomware-sets-its-scope-on-video-gamers/
[4] http://labs.bromium.com/2015/03/12/achievement-locked-new-crypto-ransomware-pwns-video-gamers/
[5] http://threatglass.com/malicious_urls/bg-mamma-com
[6] http://malware-traffic-analysis.net/2015/04/03/index.html
[7] https://isc.sans.edu/diary/Exploit+Kit+Evolution+During+2014+-+Nuclear+Pack/19081



Comments