Example of Cobalt Strike from Emotet infection
Introduction
Update, 2022-02-09 at 17:09 UTC: I've posted traffic and malware samples from the Emotet infections I generated to get traffic and malware samples when preparing for this diary. The files are located here.
Since early December 2021, we have seen reports of Emotet infections dropping Cobalt Strike malware (link). I've seen it occasionally since then, and I reported an example last week. Today's diary reviews another Cobalt Strike sample dropped by an Emotet infection on Tuesday 2022-02-08.
Details
This was an infection from the epoch 5 botnet, and approximately 5 hours after the initial infection, Cobalt Strike traffic started on 2022-02-08 at 19:54 UTC. The Cobalt Strike binary was sent over HTTPS Emotet C2 traffic, so there were no indicators over the network for Cobalt Strike until the Cobalt Strike traffic started.
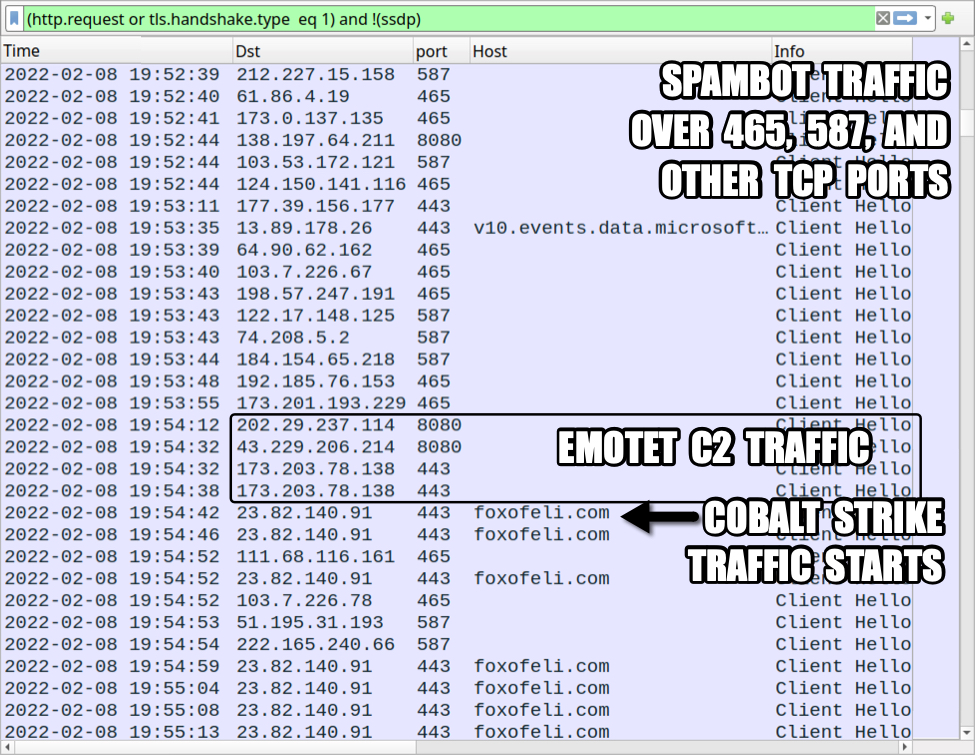
Shown above: Emotet infection traffic with the start of Cobalt Strike activity.
The first domain was foxofeli[.]com, and approximately 15 minutes later another domain for Cobalt Strike named diyabip[.]com as shown in the image below.
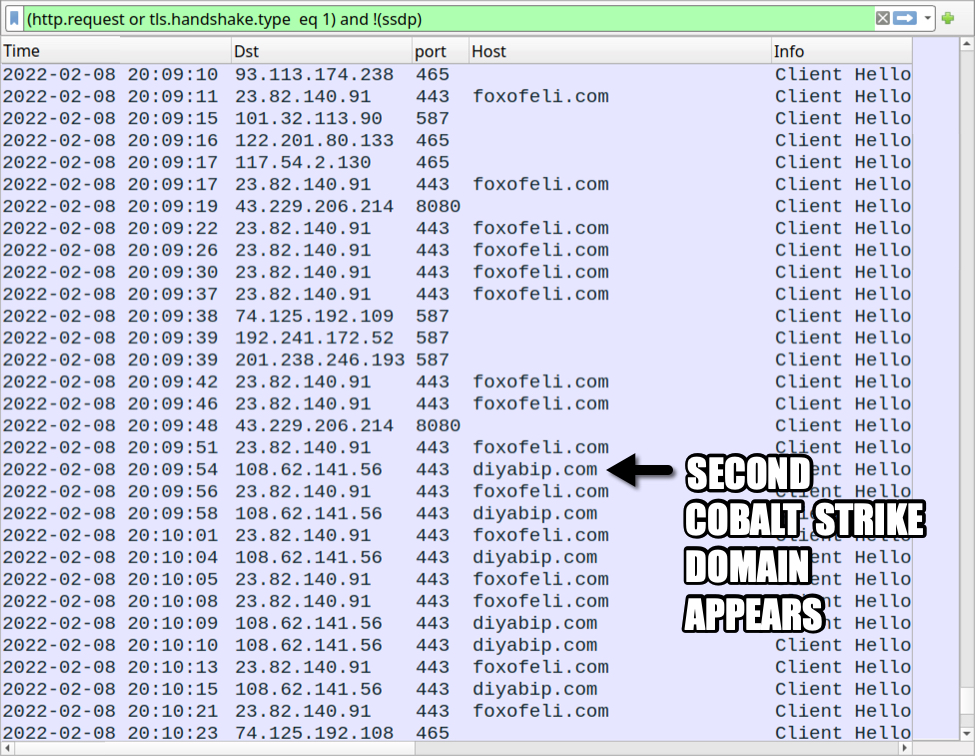
Shown above: Second Cobalt Strike domain appears during the infection.
The Cobalt Strike binary is a 64-bit DLL that was saved to the same directory as the Emotet DLL.
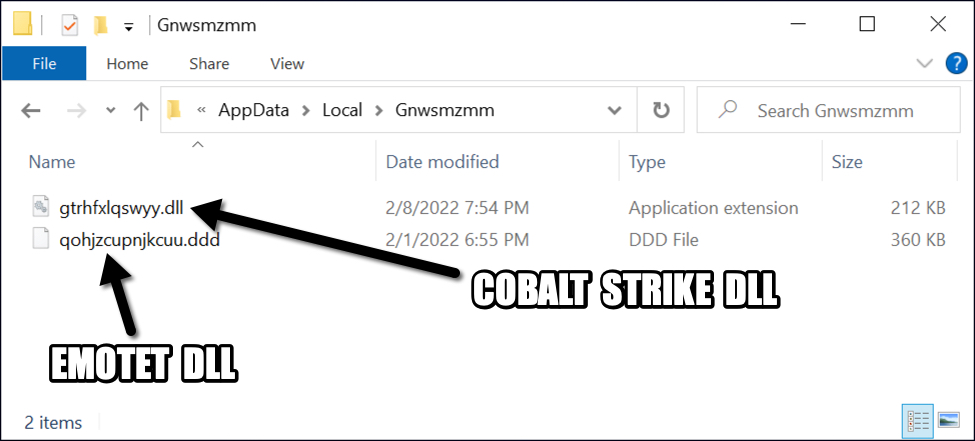
Shown above: Cobalt Strike DLL saved to the same directory as the Emotet DLL.
Indicators of Compromise (IOCs)
Cobalt Strike binary dropped during Emotet epoch 5 infection:
SHA256 hash: b6262f4aa06d0bf045d95e3fcbc142f1d1d98f053da5714e3570482f0cf93b65
- File size: 216,576 bytes
- File location: C:\Users\[username]\AppData\Local\[Emotet directory]\gtrhfxlqswyy.dll
- File type: PE32+ executable (DLL) (GUI) x86-64, for MS Windows
- Run method: regsvr32.exe /s [filename]
- Note 1: [username] is specific to the Windows user account name of the infected victim.
- Note 2: [Emotet directory] name and the DLL file name are different for each infection.
Analysis links for the Cobalt Strike binary:
Cobalt Strike traffic:
- 23.82.140[.]91 port 443 - foxofeli[.]com - HTTPS traffic
- 108.62.141[.]56 port 443 - diyabip[.]com - HTTPS traffic
Final words
During real-world incidents, investigations have occasionally revealed use of Cobalt Strike before a threat actor drops ransomware (here is one example, and here is another). I haven't yet seen ransomware sent through Emotet to Cobalt Strike infections in my lab environment, but we should remain aware of the threat posed by this malware combo.
Traffic, malware samples, and associated IOCs from the Emotet infections that I generated for today's diary are located here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments