Do you have your network perimeter secured against downloading malicious content?
by Manuel Humberto Santander Pelaez (Version: 1)
Information security professionals take very seriously the network perimeter and tend to put in place several devices to enforce access control to network resources like firewalls, IPS, content filtering devices including antimalware functionality and network access control. But there are two specific variables that can increase a lot the risk of external compromises:
- Administrative privileges in desktop computers: Many types of business software do not have implemented the principle of requiring the least privileges. That us why now a significant percentage of companies grant Administrator privileges to users, where their use is not monitored in detail.
- USB device control: Many companies subject to compliance regulations does not allow usage of USB ports at all. However, those companies are a small percent of the total universe and the remaining ones are not willing to implement unpopular measures.
Consider the following scenario: companies with PC accessing through the official Internet access and corporate laptops with 4G access:
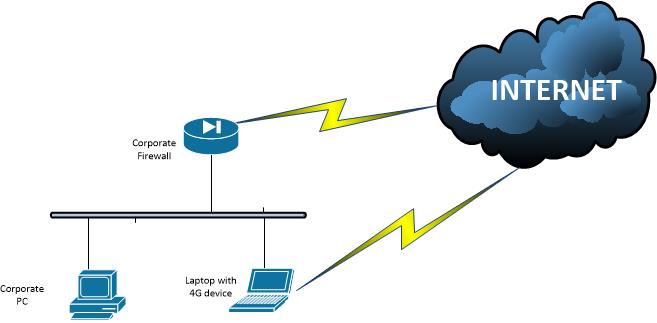
There are some circumstances where the CISO might be really unpopular, like the day where the official country's soccer team is playing a decisive match. Of course, the official internet access won't allow the access to the stream and so, people will find "alternate ways" to access it. Since not too many people knows the concept of default gateway and how to change it in the computer without causing themselves a self-inflicted denial of service, There is a very interesting program called delegate, which is a multipurpose proxy and will fit for the need of bypassing the internet access. Since there is a very detailed usage examples page, people can start using it without further difficulty.
Most people in corporate networks are aware that the "proxy parameter" exist, so it is very easy for them to change it and enjoy the "benefits" of free-of-restriction internet.
How can you tell if you have "free proxies" inside your network that use the illustrated scenario? nmap has a plugin that is able to check for open proxies. If you want to check for open proxies inside network 192.168.0.0/24, you can issue the command nmap --script http-open-proxy.nse 192.168.0.0/24. The following figure shows an example result for the discussed scenario:
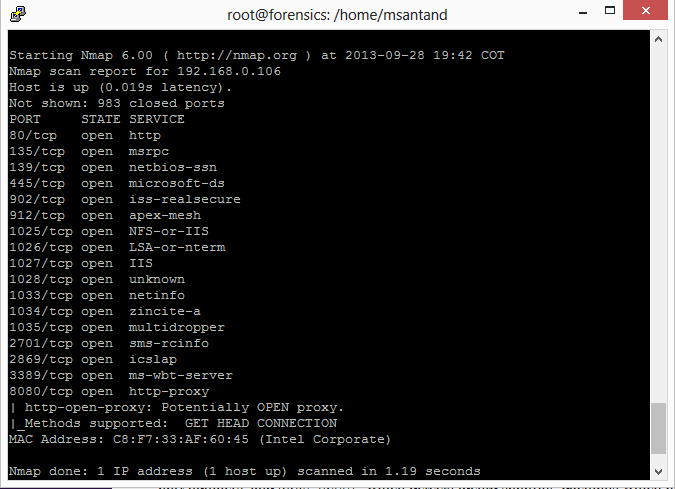
You should definitely segregate administrator privileges for your users and also disallow usage of 3G an 4G devices when plugged into the corporate network. If you don't have tools for this, you should monitor the usage for the administrator privileges given to your users.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org



Comments
Anonymous
Sep 30th 2013
1 decade ago
2.) Turn on mandatory VPN for clients connecting from outside network (Palo Alto networks offers this, not sure about Cisco and Juniper).
3.) Turn on exception for streaming of key events (March Madness, etc.)
Doing these three things above have allowed us drop our FWA and infection rates to <0%
Anonymous
Sep 30th 2013
1 decade ago
It might, but with this restriction: at least the 4G network cannot be used as a covert channel for providing interactive remote access or interactive exploit attempts.
Also, it prevents direct exfiltration --- any significant amount of data data to be stolen has to be temporary cached on the phone first, So by ensuring 4G and local USB cannot ever simultaneously be available;
You've potentially helped ensure that any exploitation of the mobile device creates (at least temporarily), more evidence, while it is in progress
Anonymous
Sep 30th 2013
1 decade ago