Critical Cisco ASA IKEv1/v2 Vulnerability. Active Scanning Detected
Cisco released an advisory revealing a critical vulnerability in Cisco's ASA software. Devices are vulnerable if they are configured to terminate IKEv1 or IKEv2 VPN sessions. (CVE-2016-1287)
[Update] Also see this writeup with LOTS of details https://blog.exodusintel.com/2016/02/10/firewall-hacking/
The vulnerability can lead to a complete compromise of the system. A single UDP packet may suffice to exploit the vulnerability, but no details about the nature of the vulnerability have been made public yet, but it is recommended to patch SOON. The exploit would likely arrive over UDP port 500 or possibly 4500.
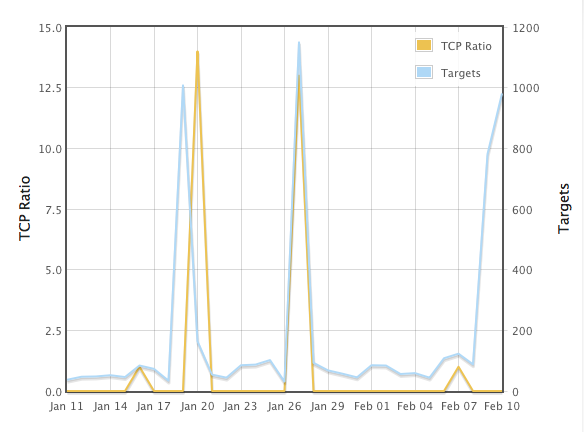
We are seeing a LARGE INCREASE in port 500/UDP traffic (see https://isc.sans.edu/port.html?port=500 and select TCP Ratio for the left Y axis. earlier spikes affecting this port were mostly TCP)
To test if your device is vulnerable, check the running crypto maps:
ciscoasa# show running-config crypto map | include interface
A product is vulnerable if a crypto map is returned.
There is no workaround, but Cisco has released patched firmware for affected devices.
[1] https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160210-asa-ike

Comments
Anonymous
Feb 10th 2016
8 years ago
Anonymous
Feb 10th 2016
8 years ago
Anonymous
Feb 11th 2016
8 years ago
"To test if your device is vulnerable, check the running crypto maps:
ciscoasa# show running-config crypto map | include interface
A product is vulnerable if a crypto map is returned."
Is slightly misleading. The Advisory indicates that an IKE1 or 2 termination point is potentially vulnerable. However issuing that command simply identify if you have an IKE1 or 2 crypto map.
After patching to 9.1(7) the test above will still return a crypto map because it is still an IKE1 or 2 termination point.
The advisory is indicating this vulnerability affects only ASA's using this method.
Anonymous
Feb 11th 2016
8 years ago
Impact
By sending specially crafted UDP packets directly to affected devices, a remote, unauthenticated attacker may be able to execute arbitrary code and gain full control of affected systems.
Note that Cisco ASA versions 7.2, 8.2, 8.3, and 8.6 are affected but no longer supported by the vendor. Users of these versions should strongly consider migrating to a supported solution.
Anonymous
Feb 11th 2016
8 years ago
•Cisco ASA 5500 Series Adaptive Security Appliances
•Cisco ASA 5500-X Series Next-Generation Firewalls
•Cisco ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
•Cisco ASA 1000V Cloud Firewall
•Cisco Adaptive Security Virtual Appliance (ASAv)
•Cisco Firepower 9300 ASA Security Module
•Cisco ISA 3000 Industrial Security Appliance
I wonder if all of those Pix's are also vulnerable.
Anonymous
Feb 11th 2016
8 years ago
Wouldn't disabling VPN be a work-around?
Anonymous
Feb 11th 2016
8 years ago
Anonymous
Feb 11th 2016
8 years ago
Anonymous
Feb 11th 2016
8 years ago
"Then how do we have remote access for employees? I thought that AnyConnect thing was a VPN."
Anonymous
Feb 11th 2016
8 years ago