CRA Maldoc Analysis
I took a look at Guy's diary entry from yesterday. This malicious document contains macros that launch a PowerShell command.
Like it is often the case with such documents, the PowerShell command will download and execute an executable: MD5 e2d5d1bf5d69a942d99c8ea45fe28ac2.
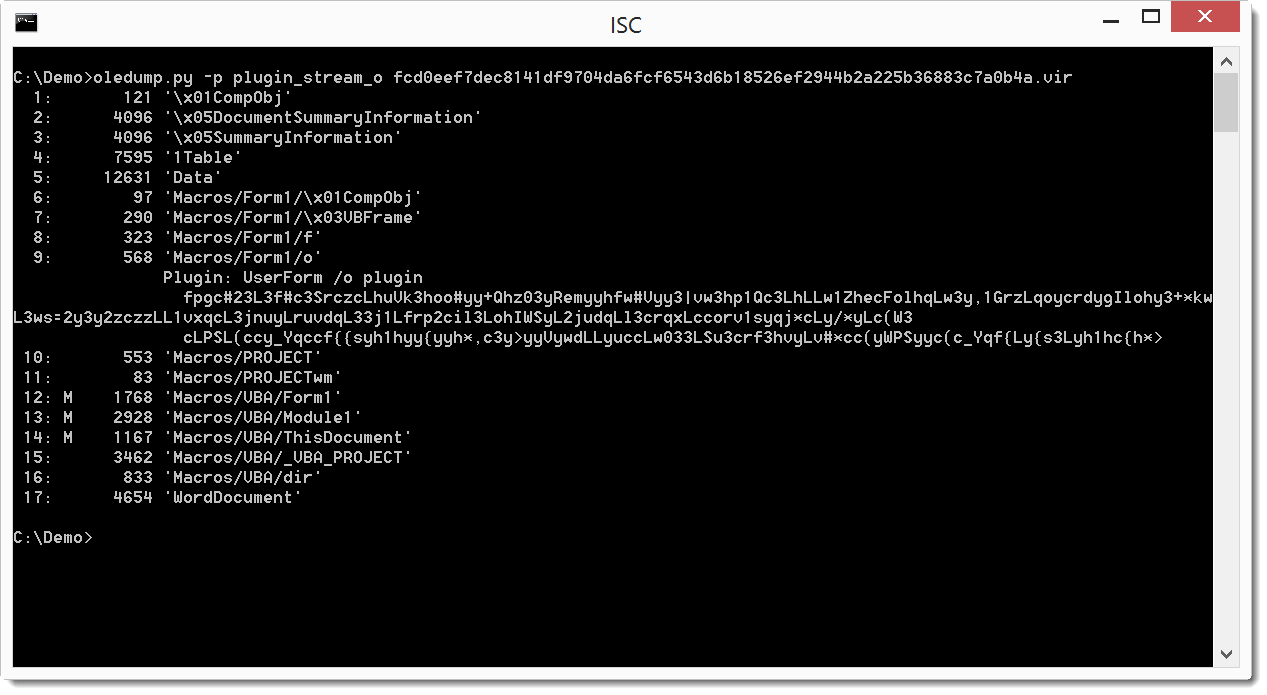
The PowerShell command is encoded and stored in Form1 objects:
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
Keywords: maldoc
0 comment(s)
×
![modal content]()
Diary Archives



Comments