Analysis from March 2021 Traffic Analysis Quiz
Introduction
Yesterday's diary provided a packet capture (pcap) of approximately 20 and 1/2 hours of traffic from an infected Windows host, which included the initial infection. It also provided malware and artifacts recovered from the infected computer. That was presented as a traffic analysis quiz, and today's diary provides analysis of the activity.
This infection was from the recently updated version of IcedID (Bokbot) we started seeing in March 2021. These types of infection are usually caused by malicious macros dressed in a Microsoft Office document like an Excel or Word file, such as this example from Friday 2021-03-19.

Shown above: These documents are often as convincing as Spiderman is here.
Incident Report
Executive Summary:
On Tuesday 2021-03-16 at approximately 19:03 UTC, a Windows computer used by Maynard Constantino was infected With IcedID (Bokbot) malware.
Victim Details:
- IP address: 172.16.4.213
- MAC address: 34:64:a9:0e:b6:15
- Host name: DESKTOP-BZQ15T8
- User account name: maynard.constantino
Indicators of Compromise (IOCs):
Infection traffic:
- 188.127.235[.]244 port 80 - 188.127.235[.]244 - GET /44271.7938611111.dat
- 185.82.217[.]213 port 80 - 185.82.217[.]213 - GET /44271.7938611111.dat
- port 443 (HTTPS traffic) - aws.amazon.com - GET / (not inherently malicious)
- 178.128.243.14 port 80 - 630mordorebiter[.]website - GET /
- 165.227.28[.]47 port 443 - iporumuski[.]fun - HTTPS traffic
- 165.227.28[.]47 port 443 - agitopinaholop[.]uno - HTTPS traffic
- 165.227.28[.]47 port 443 - dedupomoshi[.]space - HTTPS traffic
- 178.128.156[.]142 port 443 - mazaksaedr23[.]space - HTTPS traffic
- 178.128.156[.]142 port 443 - kledoapkd[.]website - HTTPS traffic
- 178.128.156[.]142 port 443 - lapoedjkeo[.]top - HTTPS traffic
- 178.128.156[.]142 port 443 - kawepotriv[.]space - HTTPS traffic
List of files recovered from the infected user's home directory:
- Kiod.hod
- Kiod.hod2
- AppData/Local/{10D90F27-F2E2-6218-7102-7745CA868DA0}/Embiteci.dll
- AppData/Local/Temp/warfare_32.tmp
- AppData/Roaming/CoverReplace/license.dat
Scheduled task recovered from infected Windows host:
rundll32.exe "C:\Users\maynard.constantino\AppData\Local\{10D90F27-F2E2-6218-7102-7745CA868DA0}\Embiteci.dll",update /i:"CoverReplace\license.dat"
Details on files extracted from the pcap:
SHA256 hash: 4f667f4267b2a1e90029ec3e66de84f0131e573087d4a0f50e4c9b5b9e0a8173
- File size: 44,544 bytes
- File location: hxxp://188.127.235[.]244/44271.7938611111.dat
- File location: hxxp://185.82.217[.]213/44271.7938611111.dat
- File location: C:\Users\maynard.constantino\Kiod.hod
- File location: C:\Users\maynard.constantino\Kiod.hod2
- File type: PE32+ executable (DLL) (GUI) x86-64, for MS Windows
SHA256 hash: 91cf231431ef2cc4defc4f1ad3d149c665acc317c4a89e0188f32df259b63cef
- File size: 377,579 bytes
- File location: hxxp://630mordorebiter[.]website
- File type: gzip compressed data, was "update_2533051401.msi", from FAT filesystem (MS-DOS, OS/2, NT), original size modulo 2^32 1397480
- Note: This is an encrypted binary masquerading as a gzip file. It's not malicious on its own.
Details on files recovered from the infected Windows host:
SHA256 hash: 523bbb839a8c0524c0f372680e6abad3b9158fafa68865381fbd1380b7b934b9
- File size: 36,352 bytes
- File location: File location: C:\Users\maynard.constantino\AppData\local\Temp\warfare_32.tmp
- File type: PE32+ executable (DLL) (GUI) x86-64, for MS Windows
- Run method: rundll32.exe [filename],update /i:"CoverReplace\license.dat
SHA256 hash: 47d084aab92ee591fe180613fda9ffd132b15db9b09be41ab046260cda311dc0
- File size: 36,352 bytes
- File location: C:\Users\maynard.constantino\AppData\local\{10D90F27-F2E2-6218-7102-7745CA868DA0}\Embiteci.dll
- File type: PE32+ executable (DLL) (GUI) x86-64, for MS Windows
- Run method: rundll32.exe [filename],update /i:"CoverReplace\license.dat
SHA256 hash: 45b6349ee9d53278f350b59d4a2a28890bbe9f9de6565453db4c085bb5875865
- File size: 341,002 bytes
- File location: C:\Users\maynard.constantino\AppData\Roaming\CoverReplace\license.dat
- File type: data
- Note: This data binary is used by the above two DLL files
Analysis
The image below shows traffic from the pcap filtered in Wireshark to focus on the initial infection and C2 traffic.
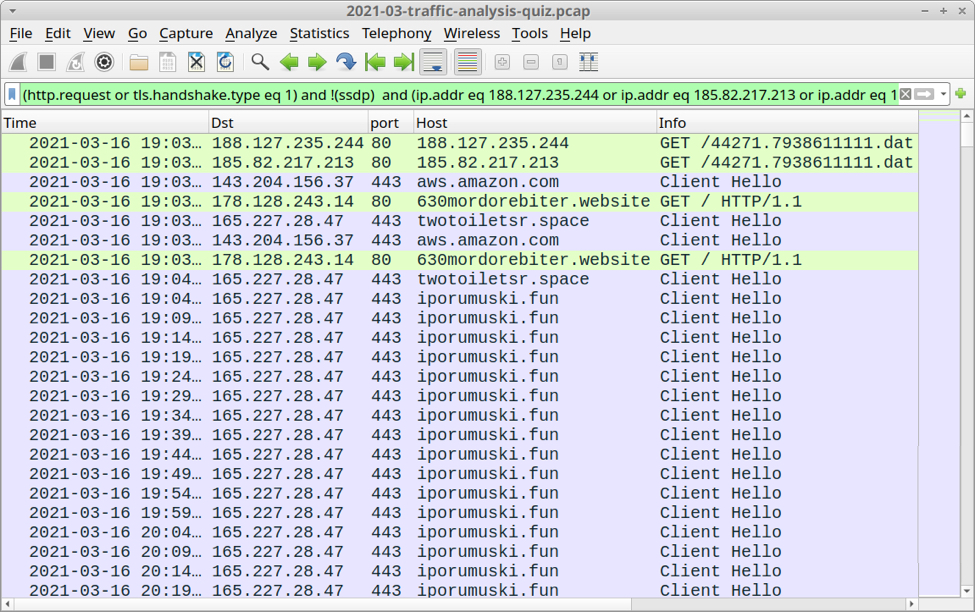
Shown above: Traffic from the infection filtered in Wireshark (part 1 of 2).
Of note, several hours after the infection, we started seeing different domains and IP addresses for the IcedID command and control (C2) traffic as shown below.
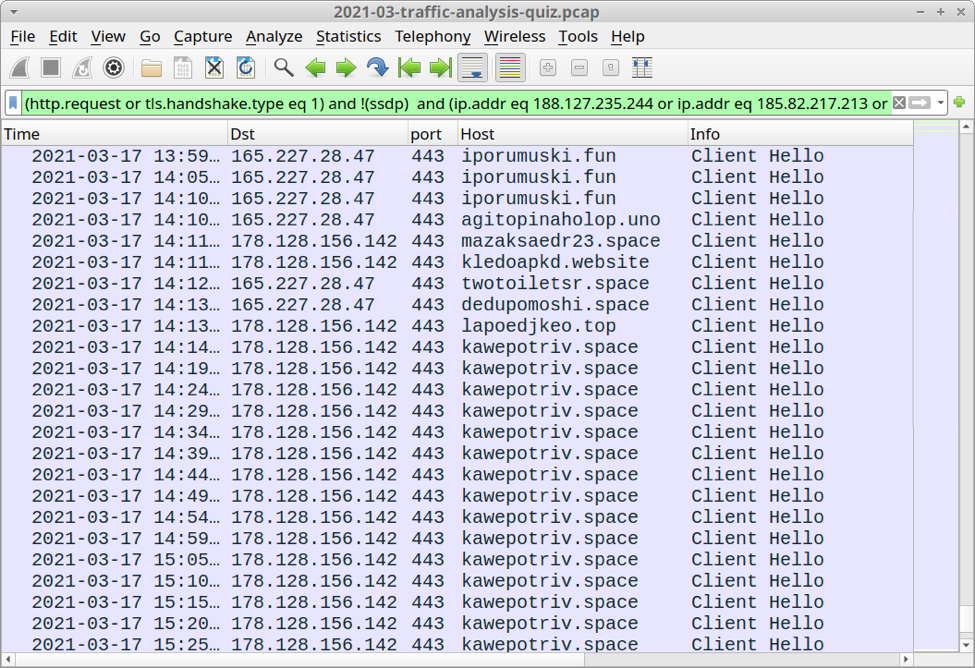
Shown above: C2 domains and IP address for the IcedID infection change near the end of the pcap.
Using WIreshark's Export HTTP Objects function, you can export the initial malware DLL and the fake gzip file used for IcedID's new "gziploader" technique to infect the host. There are two copies of each file in the pcap. See the image below for details.
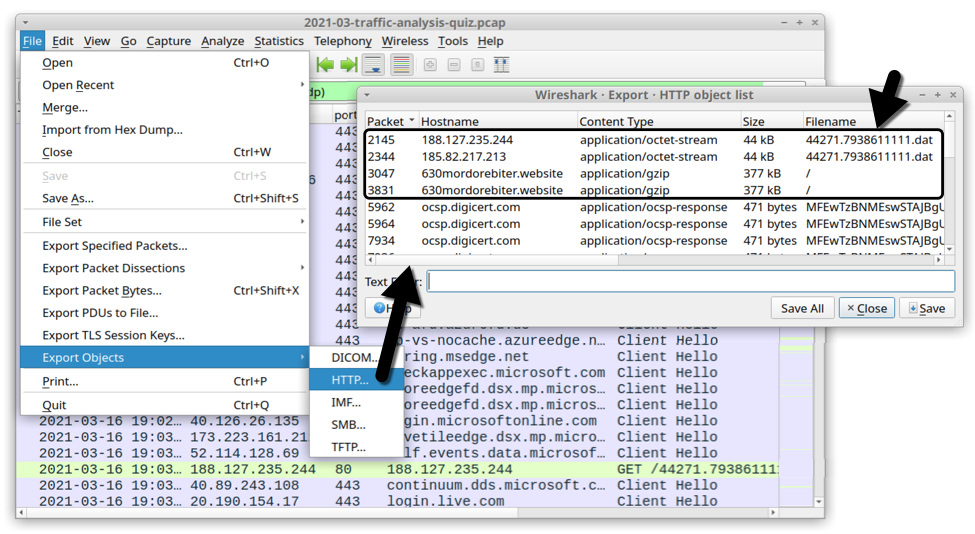
Shown above: Exporting initial DLL and fake gzip file from the pcap.
Perhaps the most easily identifiable characteristic of recent IcedID infections is the license.dat file referenced in the scheduled task. This binary data file is used by the initial and persistent IcedID DLL to infect and keep the infection persistent.
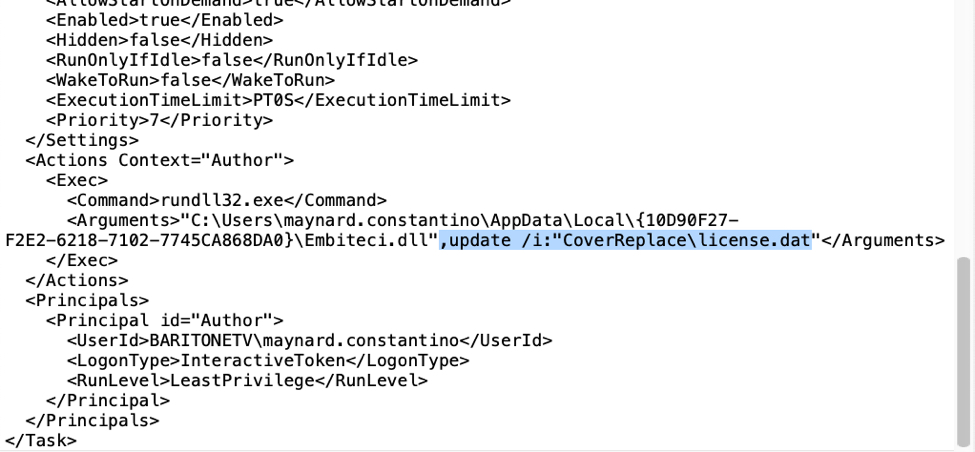
Shown above: Action from the scheduled task, where rundll32.exe uses license.dat when running the persistent IcedID DLL.
Final Words
This "gziploader" technique used by IcedID is fairly new, so some people in the infosec community might not be fully aware of it yet. However, post-infection activity remains noticeably similar to what we've seen with IcedID malware in the past few months before the update.
A zip archive with a pcap of the infection traffic is available in this Github repository, which also contains malware and artifacts from the infected computer.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments