Ad Blocking With Pi Hole
Network-wide ad blocking via your own Linux hardware
Pi-hole® is a DNS sinkhole that protects your devices from unwanted content, without installing any client-side software.
From the Pi-hole Overview:
Easy-to-install: versatile installer, takes less than ten minutes
Resolute: content is blocked in non-browser locations, such as ad-laden mobile apps and smart TVs
Responsive: speeds up browsing by caching DNS queries
Lightweight: runs smoothly with minimal hardware and software requirements
Robust: command line interface quality assured for interoperability
Insightful: responsive Web Interface dashboard to view and control Pi-hole
Versatile: optionally functions as DHCP server, ensuring all your devices are protected automatically
Scalable: capable of handling hundreds of millions of queries when installed on server-grade hardware
Modern: blocks ads over both IPv4 and IPv6
Free: open source software
Of Note
* Cited from docs.pi-hole.net.
The Pi-hole setup offers 8 options for an upstream DNS Provider during the initial setup.
Utilize the Pi-hole command line interface with ease.
Pi-hole includes a caching and forwarding DNS server, now known as FTLDNS.
After applying the blocking lists, it forwards requests made by the clients to configured upstream DNS server(s).
Updating is as simple as running the following command: pihole -up
Pi-hole Installation
I installed Pi-hole on a Raspberry Pi 2 Model B running Raspbian Stretch (November 2018, 4.14 kernel).

Figure 1: Pi-hole on Raspberry Pi 2 Model B
There a one step automated installation method for those who want to get started quickly and conveniently, using the following command:
curl -sSL https://install.pi-hole.net | bash
There are alternative installation methods if you’re not comfortable piping to bash.
Piloting Pi-hole
Once you’ve completed installation, browse to the IP addess you established during setup. After running Pi-hole for even a few hours, it will begin to serve you as designed, and well at that.
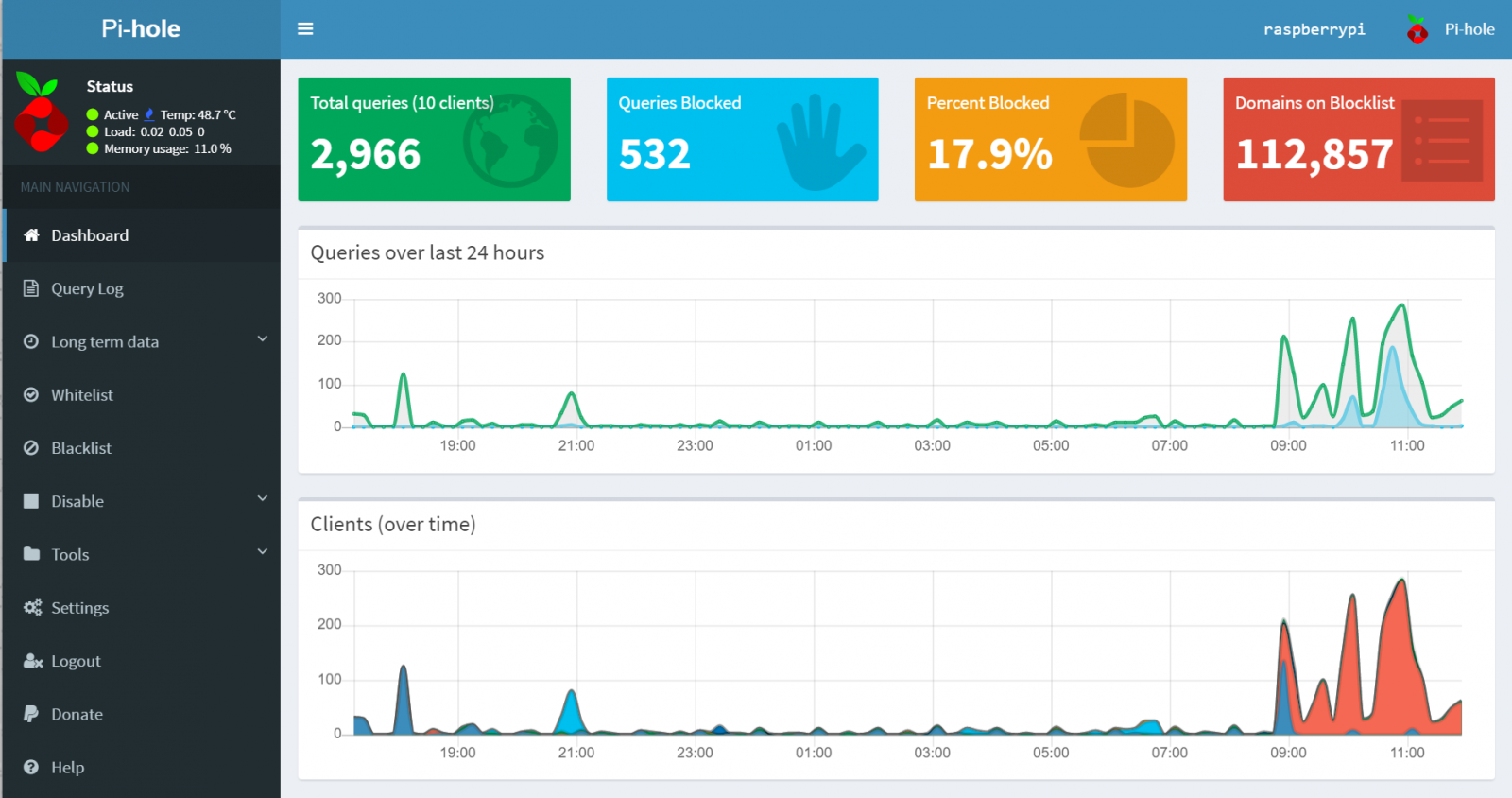
Figure 2: Pi-hole at work
Take note of the fact that 17.9% of traffic and 532 specific queries. Pi-hole’s Gravity script is key here: “Gravity is one of the most important scripts of Pi-hole. Its main purpose is to retrieve blocklists, and then consolidate them into one unique list for the built-in DNS server to use, but it also serves to complete the process of manual whitelisting, blocklisting and wildcard update. It is run automatically each week, but it can be invoked manually at any time.”
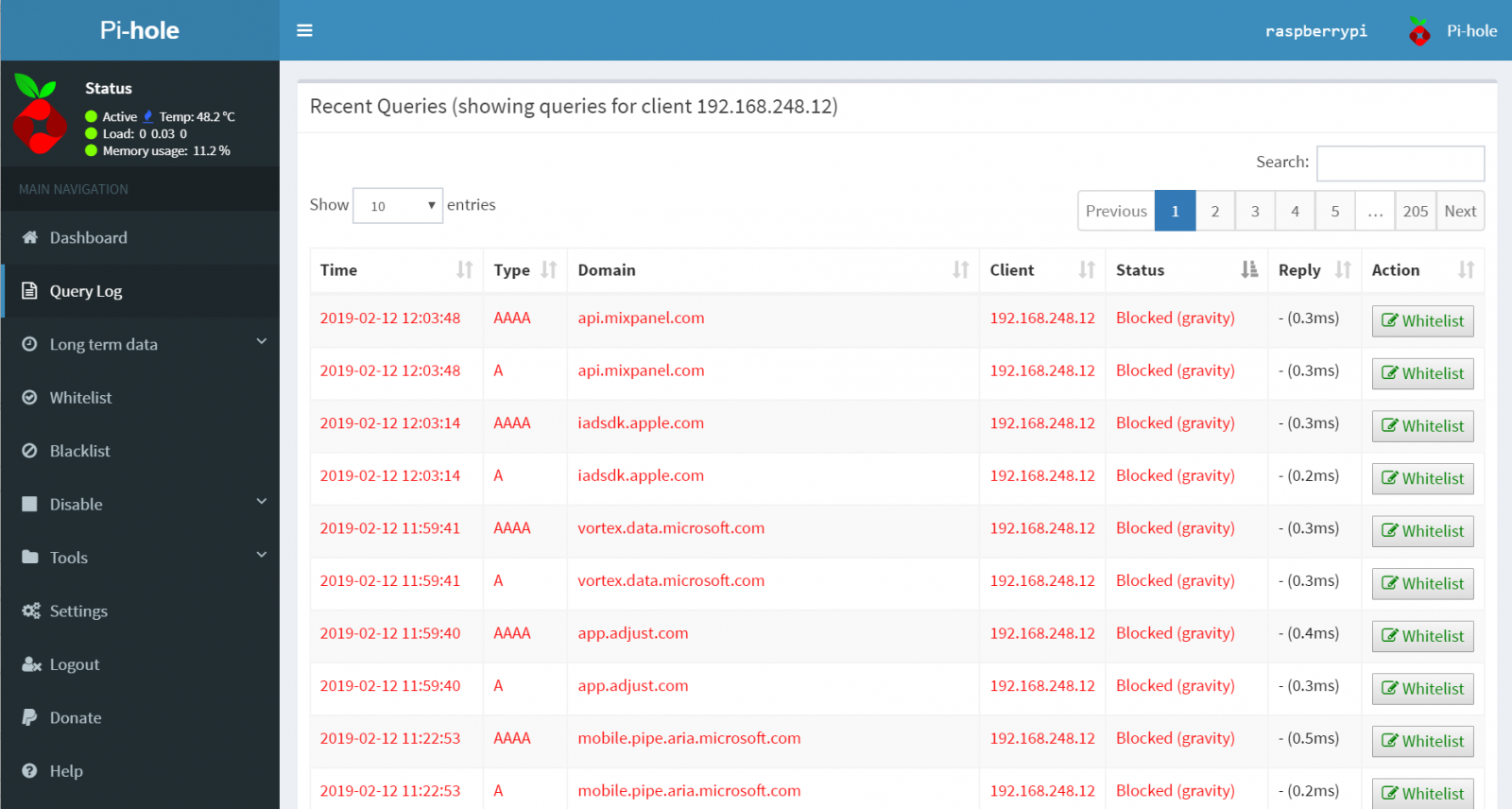
As seen in Figure 3, Pi-hole takes exception to a number of offending domains.
Figure 3: Pi-hole blocks
192.168.248.12 is my iPhone on my local network. You can see that between Apple, Microsoft, and other domains, there’s more than a bit of content in their ad streams that is flagged as less than desirable via Pi-hole’s Block Lists.
Enjoy the use and benefits of Pi-hole, I’d really like to hear about your success stories, and how you’re running Pi-hole (what hardware platforms?).

Comments
Anonymous
Feb 26th 2019
5 years ago
Anonymous
Feb 26th 2019
5 years ago
Worth pointing it to SANS own suspicious domain feeds, which are in a compatible format to help add another layer of defence against malicious activity.
Link:https://isc.sans.edu/suspicious_domains.html
Anonymous
Feb 26th 2019
5 years ago
You need to be conscious that while you are browsing there may be some legitimate content blocked. This usually presents itself as a blank or non-responsive page. In that case you will need to whitelist the domain so that Pihole admits the content.
Anonymous
Feb 26th 2019
5 years ago
I run a VPN client on all my clients for increased privacy & security...and when that VPN client is working correctly (i.e. not leaking DNS requests), all DNS requests go to their resolvers not the local Pi-hole so you're back to getting ads again.
It seems you have a choice. Use a VPN with all the advantages it provides and get bombarded with ads again or disable the VPN, lose the advantages it provides but have a better ad-free experience.
Not sure if anyone has any ideas on this conundrum
Anonymous
Feb 26th 2019
5 years ago
Anonymous
Feb 26th 2019
5 years ago
Anonymous
Feb 26th 2019
5 years ago
Anonymous
Feb 26th 2019
5 years ago
Anonymous
Feb 26th 2019
5 years ago
Anonymous
Feb 26th 2019
5 years ago