A recent example of Emotet malspam
Shown below is an example of malicious spam (malspam) pushing Emotet malware. It has an attached Word document with macros designed to install Emotet on a vulnerable Windows host.
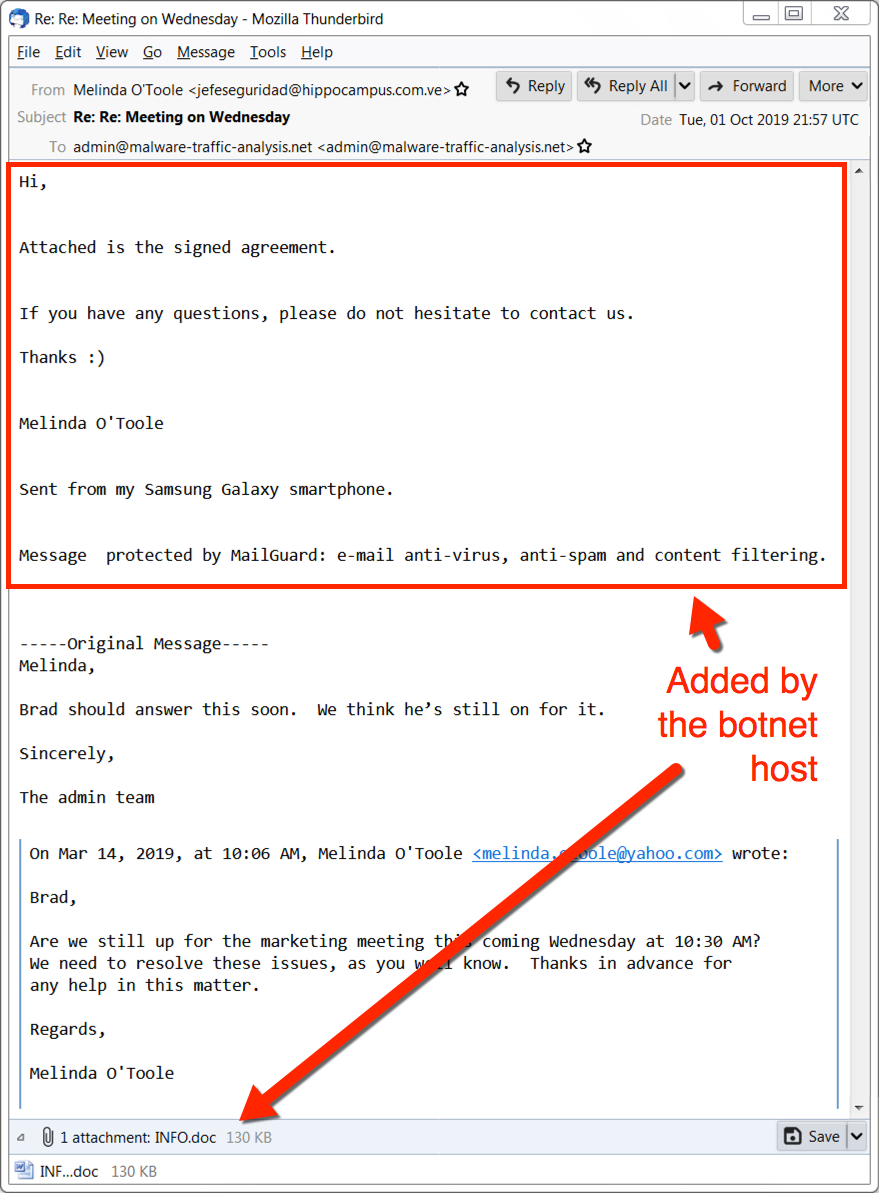
Shown above: Emotet malspam from Tuesday 2019-10-01.
Of note, this malspam is based on a message from the inbox of a lab host I infected with Emotet back in March 2019. This information was kept for over 6 months before a host from the Emotet botnet added the additional text and attachment, sending it back to my blog's email address.
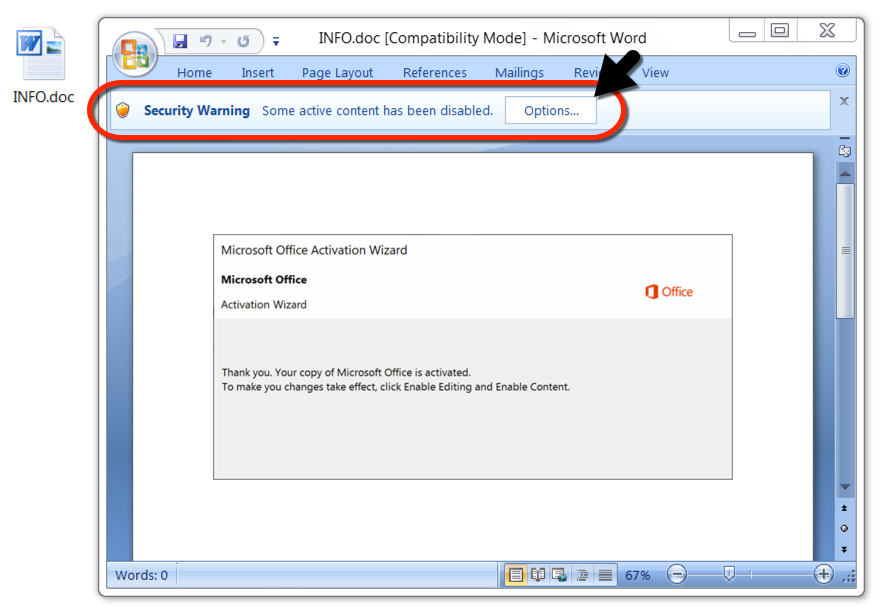
Shown above: The attached Word document with macros for Emotet.
I used a sandbox to open the Word document in a vulnerable environment and enable macros. This led to the expected Emotet traffic and artifacts on the infected host.
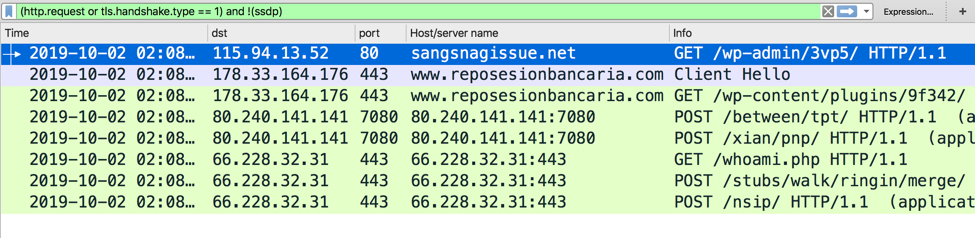
Shown above: Traffic from the infection filtered in Wireshark.
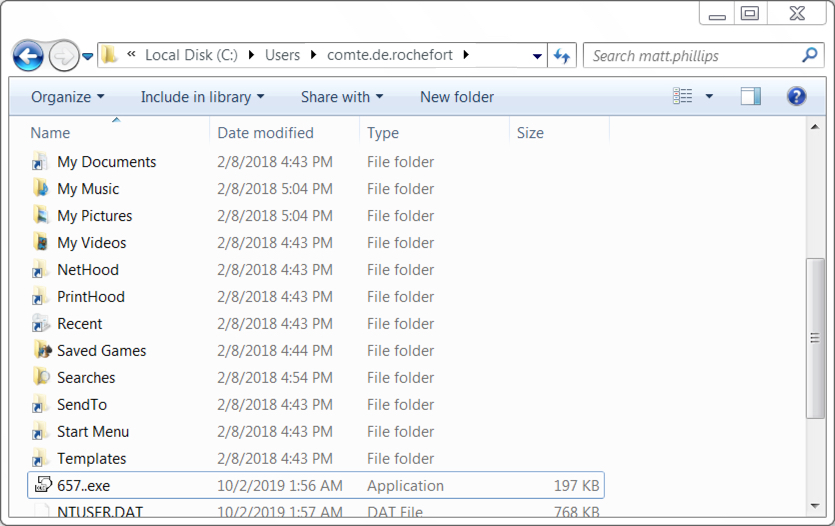
Shown above: The initial Emotet executable file (657.exe) temporarily saved under the user's profile directory.
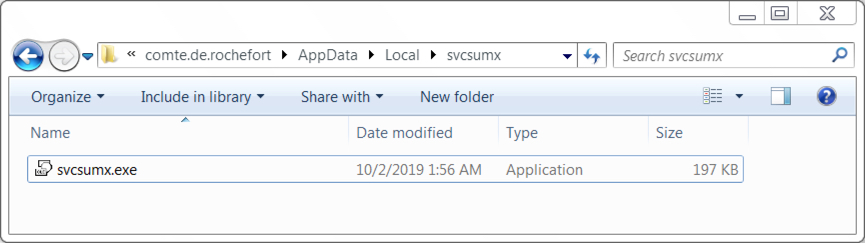
Shown above: The Emotet executable where it remained persistent on the infected host.
Final words
I expect we'll keep seeing malspam pushing Emotet in the foreseeable future. Of course, properly-administered Windows hosts that follow best security practices are rarely, if ever, vulnerable to these attacks. However, enough vulnerable hosts exist, and apparently enough infections occur to make this activity worthwhile for the criminals.
Sandbox analysis of the Word doc with macros for Emotet can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments