Detecting (Malicious) OneNote Files
We are starting to see malicious OneNote documents (cfr. Xavier's diary entry "A First Malicious OneNote Document").
OneNote files have their own binary fileformat: [MS-ONESTORE].
A OneNote file starts with GUID {7B5C52E4-D88C-4DA7-AEB1-5378D02996D3}.
Files contained in a OneNote file start with a header (FileDataStoreObject) followed by the embedded file itself. This header also starts with a GUID: {BDE316E7-2665-4511-A4C4-8D4D0B7A9EAC}.
Hence, to detect OneNote files with embedded files, look for files that start with byte sequence E4 52 5C 7B 8C D8 A7 4D AE B1 53 78 D0 29 96 D3 (that's GUID {7B5C52E4-D88C-4DA7-AEB1-5378D02996D3}) and contain one ore more instances of byte sequence E7 16 E3 BD 65 26 11 45 A4 C4 8D 4D 0B 7A 9E AC (that's GUID {BDE316E7-2665-4511-A4C4-8D4D0B7A9EAC}).
This allows you to detect OneNote files with embedded files. Which are not necessarily malicious ... Because an embedded file can just be a picture, for example.
I have a bit more detail on the analysis of this format, in my blog post "Analyzing Malicious OneNote Documents".
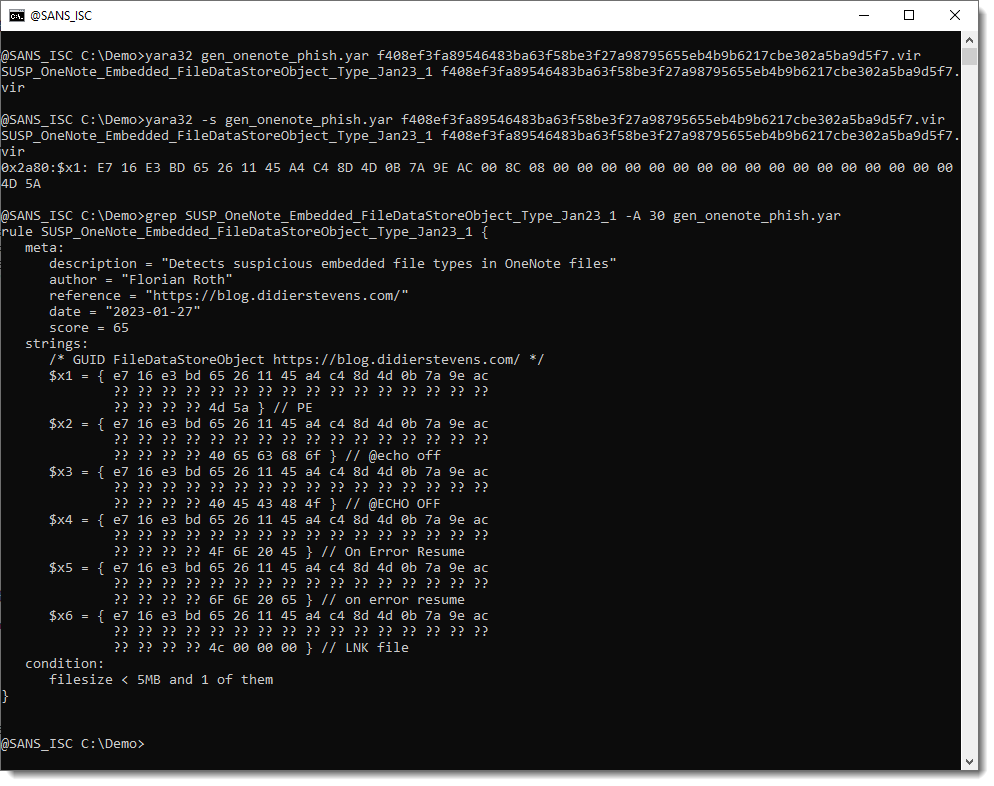
Florian Roth developed YARA rules that look for these GUIDs, together with some typical malicious payloads: PE files, BAT files, VBS files, LNK files.
The trick is to look at the beginning of the embedded file, which can be found 36 bytes after the start of structure FileDataStoreObject (hence 36 bytes after each {BDE316E7-2665-4511-A4C4-8D4D0B7A9EAC} guid).
If an embedded file starts with MZ, it's most likely an embedded Windows executable (but it could also be a text file that starts with MZ). If it starts with 4C 00 00 00, it's most likely an LNK file.
BAT and VBS files are harder to recognize, as they have no magic header: they can start with any byte sequence. Florian's rule uses a little heuristic: it identifies files that start with "@ECH" as BAT files (@ECHO OFF) and files that start with "on e" as VBS files (on error resume). Of course, this will not detect all malicious OneNote files, but we can never have perfect detection ...
Here is one of Florian's rules that detects a OneNote file with an embedded PE file ($x1):
Mostly as an exercise for myself, I created Suricata rules for onenote files. You can find them here, in my beta GitHub repository.
Caveat: these rules have not been tested in production, and the first rules detect any onenote file, with or without benign/malicious payload.
I'll provide more details on these Suricata rules in an upcoming blog post.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments