Snipping Leaks
ISC reader Phil asked a great question earlier today: "I'm wondering if there are data leakage concerns with screenshot tools such as MS Snipping Tool, if such tools have metadata in any of the formats they support".
Well, yes, they do.
Screenshots taken with the MS Snipping Tool and saved in JPG format contain both an EXIF and XMP header. You can look at what's in there for example with Phil Harvey's excellent ExifTool (http://www.sno.phy.queensu.ca/~phil/exiftool/)
The leakage is nowhere near as extensive as what is often found in MS Office documents, but it is definitely present. Among lots of information that describe the geometry of the screenshot taken, the more interesting fields include the name of the user who created the "snip", as well as the time stamp. The name is the full user name as configured for the respective windows account. If you want to surreptitiously post an image somewhere under a pseudonym, that's definitely a point to keep in mind ;).
EXIF and XMP tags can be readily removed - again using ExifTool, a simple "exiftool -ALL= image.jpg" will remove all meta tags from the image. Exiftool is friendly enough to create a backup named image.jpg_original, in the rare case something goes wrong in the process.
If you use other screen capture tools and have information on the meta data that gets stored together with the capture, please comment below or via our contact form.
ISC Feature of the Week: SSH Scan Reports
Overview
Our feature this week introduces Dr. Ullrich's newest system addition addressing wide spread reports of SSH scans. This system collects logs you submit via a special API URL. We keep receiving reports from readers about wide spread ssh scans. This system was setup to get a better handle on these scans. http://isc.sans.edu/sshreports.html Reporting will be released as soon as there is enough information collected.
Features
- Reports are "POST"ed to https://isc.sans.edu/api/sshreports
- Parameters are userid, authkey, data(tab-delimited log data)
-
XML status OK returned on successful submission
- This only accepts data. Validation and processing are done at a later time
There is currently a PERL script to collect data from the "kippo" honeypot available at https://isc.sans.edu/kipposcript.pl
Post suggestions or comments in the section below or send us any questions or comments in the contact form on https://isc.sans.edu/contact.html#contact-form
--
Adam Swanger, Web Developer (GWEB, GWAPT)
Internet Storm Center https://isc.sans.edu
2 Comments
McAfee releases extraDAT for W32/Autorun.worm.aaeb-h
McAfee released an extra dat this morning https://kc.mcafee.com/corporate/index?page=content&id=KB76807 for W32/Autorun.worm.aaeb-h
We've received a few emails relating to this, mainly because the formatting on some of the emails wasn't quite what people were expecting. As far as I can tell it is legit. I haven't found any evilness in the PDF linked to from the KB (at least there wasn't anything to find when I checked).
The KB also has an updated stinger file to remove the worm from the machine.
If you have the issue at the moment you may want to apply the DAT, but otherwise you may wish to wait untill it rolls out as part of the normal update cycle. In the mean time have a read of the KB and associated info and that will give you some info on determining if you have the issue in your network .
If you have been infected the malware guys and gals always enjoy plucking things apart so upload it via the contact form (zip file with a password of infected please).
Mark
5 Comments
Can users' phish emails be a security admin's catch of the day?
Blocking phishing emails is part and parcel of now commonplace technology controls, supplied by a wide range of vendors and, depending on your viewpoint (or how many angry user phone calls received daily), they do a great, resonable or bad job of blocking this type of unsolicited email. Despite the technologies deployed, ultimately the human factor is at play [1]. If someone in your company is going to click a link, open an attachment or click on a link to download a password protected file, then go to another site to get the password to open the file and have to install an old version of Java to see the Christmas Chickens dancing Gangnan style, then our reliance on user awareness training and constant reminders is the final safety net.
The ones that get through the technical controls are the ones that cause pain, either from afore mentioned angry users or, more seriously, possibly having to spin up some form of incident response. The question should be can these phishing email that evade our front line defenses be of more use other than to be forwarded to the filtering vendor with a pithy comment along the lines “another one gets through – again”?
Something to think on before you tell the user to “just delete that, it ‘s a stupidly obvious phishing email” have a read of some of the Anti Phishing Workgroup’s reports [2]. Phishing attacks clearly works and is still on the increase, so ignoring this problem is doing a disservice to your company and the staff.
Here is one way to get a bit more insight to the impact those nasty phishing emails to your network, then appy some defense and awareness in one fell swoop. I’m going to focus on the most common type of phishing email, one that contains an obfuscated URL leading to a malicious site.
Once you have a phishing email, a quick look at the source html will clearly show the link to https: // mylovelybank.com is actually pointing to http: // muhaha-I’m-an-evil-scammer.org. This tells us we have a real phish on our hands to deal with.
With that single URL, it enables you to search firewall, proxy and DNS logs[3] to see if anyone on your network has followed that link. And with that you now know the current impact of that one phish email to your organization.
Add it to the firewall/proxy block and alert rule, or better still, to a redirect rule that sends the next hapless phishing victim to a user awareness internal page educating them on what a phishing email is. This provides a list of people to receive the next batch of user awareness training and again shows the scale of how effective this phish was after the block was added.
“Ah-ha!” I hear you cry “How do I get the phishing email in the first place, if my users don’t know they been phished in the first place!”
Well, that’s a fair point, but you can use the natural, local resources of every IT/Security admin: The helpdesk/support team, well known unused email addresses directed to one mailbox ( e.g. administrator@, webmaster@, abuse@ etc), the entire user population and “Bob”, the guy that seems to always get spam and phishing emails first. Either you already know who the “Bob” in your company is or the support staff most definitely will.
Have them forward known or suspected phishing emails to your special mailbox to investigate. Those that are real phishing email can be added to URL defenses and can be also added into your newly created Phishing scam blog/wiki/intranet site with recognition being given to the person that reported it. This provides a great teaching and reference material for not only staff but they can use it to warn their friends and families as phishing targets anyone with an email address.
To make some security graphics for those all important weekly/months reports, create them from the numbers of URLs the added phishing blocks, number of staff that clicked on the before and after the blocks were place and the number of phishing email reported by staff. That should keep management happy and provide historical charting of the amount of reported phishing events to help frame the overall security awareness health of the staff.
You’ve now gone from a one lone skirmisher to an army against the menace of phishing emails. Getting the staff working for you to protect the company is one step closer to improving the over all security posture (and possibly being able to go home on time).
As ever, feel free to pitch in any thoughts or comments.
[1] Top tips to help the human element http://www.securingthehuman.org/blog/
[2] http://www.antiphishing.org/resources/apwg-reports/
[3] Some great tips on fun security stuff to do with DNS https://blog.damballa.com/archives/1834
Chris Mohan --- Internet Storm Center Handler on Duty
2 Comments
Online Shopping for the Holidays? Tips, News and a Fair Warning
'Tis the season of online shopping with more of your shopping online than ever before. As the old saying goes, "On the Internet, nobody knows you're a dog" (*), how do your users know that they are buying from a safe vendor? In timely news, the US Federal Government shut down 132 "fake online shopping sites" for selling counterfeit goods. Our own Dr. Johannes wrote this piece in Forbes today with 7 safe steps to stay safe shopping online today:
- Stick to Sellers you Know
- Don't Trust Customer Reviews Blindly
- Be Careful with "Phishing"
- Watch Your Credit Card Statement Carefully
- Be a Cautious Seller
- Be Careful When and How to Meet a Craigslist Seller
- Don't Buy Stolen Property
Read the whole thing for more explicit details and share with your users. Some things for the more technically inclined to be aware of. Many fake online shopping sites come with malware, particularly those that arrive via spam. And, of course, with SEO, blind google searches could land you on a bad site instead of a good one. Is there something we missed? Use the contact form and chime in!
--
John Bambenek
bambenek \at\ gmail /dot/ com
Bambenek Consulting
* -
3 Comments
What's in Your Change Control Form?
It's surprising how many organizations don't plan well for change. Change Control is a well known process, one that is well defined in many different frameworks (ITIL and the ISO 27000 Series and NIST for starters). Yet many organizations plan changes over coffee and a napkin (or a visio on a good day). This almost always results in figuring out problems during the change (I don't know about you, but the less 1am thinking I need to do, the better off I am!), conflicting changes, or changes that just plain don't work, and need to be backed out in a panic.
IT is supposed to be a support group for the larger organization, so we should be striving for planned changes. From the point of view of the larger business, we want system maintenance and upgrades to be as close to a non-event as we can possibly make it.
So, how do most IT organizations make this happen? In most cases, with a formal change control process.
The Change Control Form:
The Change Control Form highlights a lot of the things that need to be done for a formal change control process.
- You need a plan for each change. This should include the steps along the way to implement the change, and how long they might take. For network changes, often I'll include the actual CLI changes I'll be making on the router or switch for example. Doing a good job in this section can really streamline the change when the time comes - many of my changes are all cut/paste operations. The last thing I need to do in a 1am Change Window is figure stuff out, the less thinking the better !
- Who is the the change owner? Every change needs to be "hung around someone's neck", so that if there's a resulting problem, the helpdesk or management knows who they should call the next day.
- You need to indicate that you (or someone) has tested this change
- A good estimate on how long the change will take is almost always required.
- A backout plan is a MUST. If you've ever had a change go south on you, you have an appreciation for how useful a step-by-step backout plan can be! Be sure to have a time estimate for this as well.
- The business will want to know how long any affected systems will be affected. Be sure to include the backout time in your outage estimate, and also indicate which other systems will be affected.
- The business will want to know what is being updated, but more importantly, what *else* will be affected by your change. For instance, updating a core router cluster might result in "all systems will be offline". Or, if your cluster is built in a different way, the answer here might be "no systems impacted".
- Often you'll need to indicate which specific user groups need to be notified of changes - filling this in is often a cooperative effort between the change owner and the management team.
I have an example change control form, that I'll often use to as a starting point when a client needs change control - you can find it here ==> http://isc.sans.edu/diaryimages/files/change%20control%20form%201a.doc
The Review Process:
Every change to the production system should be reviewed. This isn't neccessarily so that everyone gets a chance to tell you that there's a better way to accomplish what you are doing (though this can sometimes happen), it's more to ensure that you don't have conflicting changes, or too many changes at once.
Conflicting changes are a real problem in larger IT groups. Back in the day, I had a set of server updates scheduled with a client. The networking team had router upgrades booked that same weekend, so all of our server updates got pre-empted, halfway through the process (oops). Needless to say, that client now has weekly change control meetings.
Too much change is another common problem. If you've got a high volume of changes going through in a short period of time, it's often tough to keep track of what changes might be impacted by what other changes. It's also easy to let things like documentation slide if there are a lot fo changes planned, with the good intentions of "catching up on that later" (we all know how this ends!).
Anyway, the common practice is to have weekly change control meetings, which have to be attended by a rep from each major group in the department. Each change is there for a yes/no - this meeting is not the place to hash out exactly how anything might be done or done better. If those discussions are still in play, then the change should be denied until there is agreement on these points. Changes should be distributed to each member of the group in advance to prevent issues like this.
Workflow tools like sharepoint or bolt-on products for email are a common way to deal with this approval process, but these are essentially "paving the cowpath" tools - plain old paper or simple emails can do a good job here also.
Emergencies:
You'll always have emergency changes. If you've got a known problem, and the fix must be put in before your next Change Control meeting or you risk a service interruption for instance. Or you need a quick network change before that new application can be rolled out (that no-body thought of until the last minute). Normally there is a fast-track for emergency changes of this type, where a small quorum of change approvers can green light an emergency change. Note that this gets your change in quick, but should NOT get you off the hook for the rest of the process - you still need to present it at the next change control meeting so everyone *else* knows what's been done, do documentation updates, assess the chagne for violations to regulatory compliance or security policies and all the rest - what the emergency process gives you is a special dispensation to do all the other process stuff after the change is in.
Documentation updates:
Everyone hates documentation. Even I do, and I'm the guy telling folks they should keep their docs up to date. But seriously, if you change your environment, you should reflect that in your documentation. I recently had to restore a firewall from 12 months old documentation, then dig the changes out from 12 months of correspondence in the sysadmin's inbox- this was NOT fun.
The easy way to do this is to automate your documentation. If you can script data collection, so that your critical infrastructure documentation can be updated automatically, you can schedule this in a daily process. Not only does this keep your docs up to date, you can then script "diff" reports and alert on changes. This is a great way to report to your IT management on changes, both approved (good changes) and un-approved (bad changes).
There are lots of products like this (CATTOOLS springs immediately to my mind, I'm a network person), but you can easily write you own scripts as well for network gear, SANs (the storage kind), Windows or Linux hosts, or anything that supports scripting really (more here http://www.sans.org/reading_room/whitepapers/auditing/admins-documentation-hackers-pentest_33303 , and there are tons of other resources and tools on the net to help! )
DRP / BCP review:
Does this change need to be replicated at your site and reflected in your DR / BCP plan? The last thing you want is for a change to go into production, and then find out it never made it to the DR Site during an expensive DR Test window, or worse yet, during an actual disaster.
Security and Regulatory Review
Changes to production systems should be reviewed with an eye towards the original design of the system. For instance:
Does the proposed change open up a backdoor path between two different security zones? We see this often, where developers are ready to deploy a new system that requires access to the same database as a different appplicaiton in a different security zone. Simply opening up the required port for direct database access could easily end badly for everyone at the next PCI or NERC/FERC audit (or whatever regulatory umbrella you might be under). Really this issue should be addressed earlier in the process, but the change control process that governs production is your final safety net for issues of this type. Well, the final safety net except for the audit that is ...
Or, is that new subnet inside or outside the range permitted for various VPN user groups? It's often the case that a new subnet or host should *not* be accessible from the VPN access for most users (SQL servers for instance). On the other hand, other hosts need to be accessible to almost all users (the corporate internet). The important thing is that as changes are implemented, that accesses to any new servcie should be assessed based on the underlying security policies that should drive the design
Risk Assessment
Hey, have I talked about Risk Assessment enough lately? Here we go again - I'm seeing more and more organizations that have inserted a Risk Assessment section into their Change Control document. I really (really) applaud this trend, but it'd be better if it was coupled with an awareness of how risk assessment should be done. What is often seen in these new sections is a list of the remotest possible negative outcomes of the change. What I'd rather see is more references to the hard work that's gone into establishing system redundancies
The Change Control Document that I posted above is one that I"ve used as an example for a while now. If you've got a more complete document, if there is something that you feel should be added or changed, or if I've missed anything in the process description, please use our comment form and share !
===============
Rob VandenBrink
Metafore
2 Comments
Risk Assessment Reloaded (thanks PCI ! )
Last month was Cyber-Security Awareness Month, and we had some fun presenting a different security standard each day. One of the standards we discussed was the ISO 27005 standard for Risk Assessment ( https://isc.sans.edu/diary.html?storyid=14332 ). So when the PCI Council released Risk Assessment Guideance this past week, it immediately caught my attention.
You can find the document here ==> https://www.pcisecuritystandards.org/documents/PCI_DSS_Risk_Assmt_Guidelines_v1.pdf
After a few days to read it, I'm impressed. They didn't try to invent a new Risk Assessment framework, instead, they refer to and borrow from OCTAVE, ISO 27005 and NIST SP 800-30.
This approach has a couple of big advantages:
- Everyone who is already doing Risk Assessment, and is basing their approach on one of the major methodolgies, is already PCI compliant for Risk Assessment
- If any of the "root" standards is updated, the PCI guidance for Risk Assessment doesn't need a corresponding update
That being said, the document is a good read - it's essentially a quick course in "mom and apple pie" Risk Assessment. So for anyone who already has a program, it's a nice review on a Friday afternoon (yes, I did say that!). But there are a boatload of large corporations who insist that they "mitigate" or "eliminate" risk, but don't actually have a written RA methodology or a formal RA program. I'm hoping that with a PCI document on the table, this will have a positive impact on organizations in this situation.
Happy reading everyone!
===============
Rob VandenBrink
Metafore
0 Comments
Greek National Arrested on Suspicion of Theft of 9M Records on Fellow Greeks
From the Associated Press via The Washington Post (http://www.washingtonpost.com/world/europe/greek-police-arrest-man-on-suspicion-of-theft-of-9-million-personal-data-files-on-greeks/2012/11/20/72dc5c64-331a-11e2-92f0-496af208bf23_story.html)
The report cites a 9 million record value and notes that Greece currently has a population of around 10 million (WolframAlpha tells me that the 2010 estimate is 11.2M.) The WP article also wisely notes that 9M value is from a data-file that hasn't been de-duplicated.
This number is expected to down-- possibly drastically, depending on the time periods covered by the data (this is me "guessing" now.) For example if the 9M records covered 9 years, there could be an overlap for every year reducing the file down to 1M (still pretty bad.) Once you've reduced the data down to the Name/Address/Tax-ID number triples you're still not done. Typographical errors will have to be dealt with, and the possibility of Tax-ID number re-use.
The interesting questions are of course: "where did these data come from" and "how did the man access them?" Lessons Learned reports aren't very effective if they're kept internally. However it is reasonable to expect to wait until after the trial for those reports to become public.
0 Comments
Behind the Random NTP Bizarreness of Incorrect Year Being Set
A few people have written in within the past 18 hours about their NTP server/clients getting set to the year 2000. The cause of this behavior is that an NTP server at the US Naval Observatory (pretty much the authoritative time source in the US) was rebooted and somehow reverted to the year 2000. This, then, propogated out for a limited time and downstream time sources also got this value. It's a transient problem and should already be rectified. Not much really to report except an error at the top of the food chain causing problems to the layers below. If you have a problem, just fix the year or resync your NTP server.
Just goes to show how reliant NTP is that it is all but a "fire and forget" service once configured until "bad things happen".
--
John Bambenek
bambenek \at\ gmail /dot/ com
Bambenek Consulting
5 Comments
New Poll: Top 5 Unresolved Security Problems of 2012
Since it is a holiday week (at least here in the United States) thought I would put up a new poll question. Unlike previous ones, this one is open-ended and comment-only. What do you think the top 5 unresolved or underresolved security issues are of 2012? What do you think is eating our lunch out there that we lack the tools or techniques to handle?
--
John Bambenek
bambenek \at\ gmail /dot/ com
Bambenek Consulting
20 Comments
Information Security Incidents are now a concern for colombian government
Before you start reading: This diary has two parts: One written in english and one written in spanish. Both have the same information, so choose the one you feel more comfortable with.
Like any other country in the world, we are no strangers to security incidents. Many criminals have moved their real world actions to the virtual world, where they have committed numerous crimes and actions that have impacted IT infrastructure of too many companies. Therefore, the National Economic and Social Policy Council (CONPES) issued the 3701 document, which sets out in policy guidelines for cybersecurity and cyber defense of Colombia. The objective of this policy is to strengthen state capacities to address threats that undermine their security and defense in the cyberspace arena creating the atmosphere and the conditions for protection inside it. The document creates the following institutions:
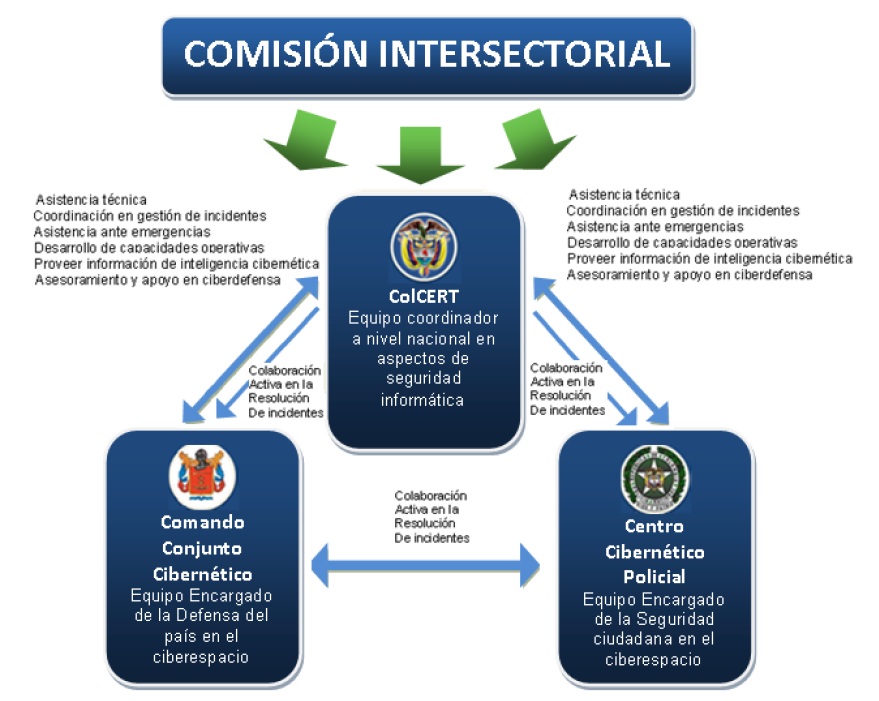
Source: CONPES Document 3701 Page 21
- Intersectoral Committee: responsible for setting the strategic vision of information management and to establish policy guidelines regarding the management of the technology infrastructure, public information, cyber security and cyber defense.
- The Cyber ​​Emergency Response Group of Colombia (colCERT) is the national agency on issues of cybersecurity and cyber defense. Receive guidelines intersectoral commission mentioned above. Its mission is to coordinate the actions necessary for the protection of critical infrastructure against the Colombian state of cybersecurity emergencies that threaten or compromise national security and defense.
- The Cyber ​​Joint Command of the Armed Forces (CCOC) depends on the General Command of the Armed Forces, who may delegate his functions within the military forces depending on the specialties in the sector. This should prevent and counter threats or cyber attack affecting nature values ​​and national interests.
- Police Cyber ​​Center (CCP) is responsible for the cybersecurity of Colombia, through the provision of support and protection against cybercrime. Develops work of prevention, care, investigation and prosecution of computer crime in the country, reporting on its website on cyber vulnerabilities. Additionally, receives and national guidelines on cybersecurity and works in coordination with the colCERT.
colCERT manages the following relations:
- Sectorial CSIRT: Since all critical sectors from the economy are encouraged to constitute their own CSIRT, colCERT coordinates with them incident response in case of something big happens.
- Law enforcement agencies: All law enforcement agencies that might have any kind of trouble with cibercrime or ciberterrorism must seek help from colCERT.
- Academic sector: colCERT must support research efforts and encourage universities to increase knowledge on incident response and infosec subjects.
- Other state agencies: colCERT must protect all state agencies from ciber threats.
We are just beginning, but this effort sure will address most of our problems at this time.
----------------------------------- SPANISH VERSION -----------------------------------
Al igual que el resto de paises del mundo, no somos ajenos a los incidentes de seguridad. Muchísimos criminales han trasladado su accionar del mundo real al mundo virtual, en donde han cometido numerosos delitos y acciones que han impactado la infraestructura de TI de las compañías. Por esto, el Consejo Nacional de Política Económica y Social (CONPES) emitió el documento 3701, en donde se estipulan los lineamientos de política para ciberseguridad y ciberdefensa de Colombia. El objetivo de esta política es fortalecer las capacidades del Estado para enfrentar las amenazas que atentan contra su seguridad y defensa en el ámbito cibernético (ciberseguridad y ciberdefensa), creando el ambiente y las condiciones necesarias para brindar protección en el ciberespacio. Con base en lo anterior, se crean las siguientes instituciones:

Fuente: Documento CONPES 3701 Página 21
- Comisión intersectorial: Encargada de fijar la visión estratégica de la gestión de la información y de establecer los lineamientos de política respecto de la gestión de la infraestructura tecnológica, información pública y ciberseguridad y ciberdefensa.
- El Grupo de Respuesta a Emergencias Cibernéticas de Colombia (colCERT) es el organismo coordinador a nivel nacional en aspectos de ciberseguridad y ciberdefensa. Recibirá los lineamientos de la comisión intersectorial mencionada anteriormente. Su misión es la coordinación de las acciones necesarias para la protección de la infraestructura crítica del Estado colombiano frente a emergencias de ciberseguridad que atenten o comprometan la seguridad y defensa nacional.
- El Comando Conjunto Cibernético de las Fuerzas Militares (CCOC) depende del Comando General de las Fuerzas Militares, quien podrá delegar sus funciones dentro de las Fuerzas Militares dependiendo de las especialidades existentes en el sector. Este deberá prevenir y contrarrestar toda amenaza o ataque de naturaleza cibernética que afecte los valores e intereses nacionales.
- El Centro Cibernético Policial (CCP) está encargado de la ciberseguridad del territorio colombiano, mediante la prestación del apoyo y protección ante los delitos cibernéticos. Desarrolla labores de prevención, atención, investigación y judicialización de los delitos informáticos en el país, informando en su página web sobre vulnerabilidades cibernéticas. Adicionalmente, Recibe y atiende los lineamientos nacionales en ciberseguridad y trabaja de forma coordinada con el colCERT.
El relacionamiento del colCERT con las demás entidades se resume en lo siguiente:
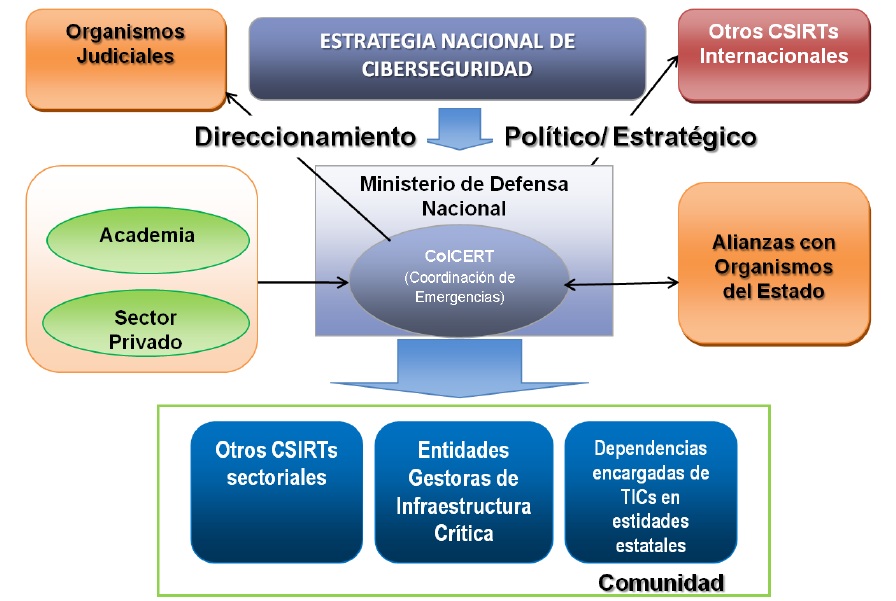
El relacionamiento del colCERT se resume en lo siguiente:
- CSIRT Sectorial: Todos los sectores críticos de la economía deben constituir su propio CSIRT y colCERT coordina con ellos la respuesta a incidentes en caso de que algo grande suceda.
- Las fuerzas de seguridad: Todos los organismos encargados de hacer cumplir la ley que puedan tener algún tipo de problema con el cibercrimen o ciberterrorismo debe buscar la ayuda de colCERT.
- Sector académico: colCERT debe apoyar los esfuerzos de investigación y alentar a las universidades para aumentar el conocimiento sobre la respuesta a incidentes y temas de seguridad de la información.
- Otras agencias estatales: colCERT debe proteger a todas las agencias del estado de las amenazas ciberterroristas.
Apenas estamos empezando, pero este esfuerzo que se está implementando actualmente se ocupará de la mayoría de nuestros problemas en este momento.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
2 Comments
Another month another password disclosure breach
Adobe has revealed that apparently a password database from connectusers.com was compromised via a SQL injection attack.[1] Ars Technica reports that the passwords were hashed using MD5 (not clear whether they were salted or not).[2] Do we really need to remind you what constitutes a strong password and not to reuse them?
Some previous password diaries that might be of interest:
Potential leak of 6.5+ million LinkedIn password hashes
Critical Control 11: Account Monitoring and Control
Theoretical and Practical Password Entropy
An Impromptu Lesson on Passwords
Password Rules: Change them every 25 years (or when you know the target has been compromised)
References:
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
3 Comments
Skype account hijack vulnerability fixed
The folks over at Microsoft (who now owns Skype) fixed a bug earlier today that potentially would have allowed anyone to hijack a Skype account simply by knowing the e-mail address the account was associated with. Apparently the vulnerability was found at least 3 months ago by a Russian researcher who claims that many users were affected. I'm not aware of any procedures in place to reclaim a Skype ID that was hijacked, but if anyone knows of one please let us know either by leaving a comment or contacting us via the contact page. Trend Micro[1] has a pretty good writeup, so I won't rehash the whole thing here and Microsoft has responded[2].
References:
[1] http://countermeasures.trendmicro.eu/skype-vulnerability/
[2] http://heartbeat.skype.com/2012/11/security_issue.html
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
0 Comments
Microsoft November 2012 Black Tuesday Update - Overview
NOTE: Several of these patches apply to Windows 8 and Windows RT that were just released last month.
Overview of the November 2012 Microsoft patches and their status.
| # | Affected | Contra Indications - KB | Known Exploits | Microsoft rating(**) | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS12-071 |
Cumulative Security Update for Internet Explorer (Replaces MS12-063 ) |
|||||
|
Internet Explorer 9 CVE-2012-1538 CVE-2012-1539 CVE-2012-4775 |
KB 2761451 | no known exploit. |
Severity:Critical Exploitability: 1,1,1 |
Critical | Important | |
| MS12-072 |
Vulnerabilities in Windows Shell Could Allow Remote Code Execution (Replaces ) |
|||||
|
Remote Code Execution CVE-2012-1527 CVE-2012-1528 |
KB 2727528 | no known exploit. |
Severity:Critical Exploitability: 1,1 |
Critical | Critical | |
| MS12-073 |
Vulnerabilities in Microsoft Internet Information Services (IIS) Could Allow Information Disclosure (Replaces MS11-004 ) |
|||||
|
IIS CVE-2012-2531 CVE-2012-2532 |
KB 2733829 | PoC code may exist. |
Severity:Moderate Exploitability: ?,? |
Less urgent | Important | |
| MS12-074 |
Vulnerabilities in .NET Framework Could Allow Remote Code Execution (Replaces MS11-078 MS11-100 MS12-016 MS12-034 ) |
|||||
|
.NET Framework 1.0 SP3, .NET Framework 1.1 SP1, .NET Framework 2.0 SP2, .NET Framework 3.5, .NET Framework 3.5.1, .NET Framework 4, .NET Framework 4.5 CVE-2012-1895 CVE-2012-1896 CVE-2012-2519 CVE-2012-4776 CVE-2012-4777 |
KB 2745030 | no known exploit |
Severity:Critical Exploitability: 1,3,1,1,1 |
Critical | Critical | |
| MS12-075 |
Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (Replaces MS12-055 ) |
|||||
|
Windows Vista, Windows 7, Windows 8, Windows RT, Windows Server 2003, Windows Server 2008, Windows Server 2012 CVE-2012-2530 CVE-2012-2553 CVE-2012-2897 |
KB 2761226 | no known exploit |
Severity:Critical Exploitability: 1,1,2 |
Critical | Critical | |
| MS12-076 | Vulnerabilities in Microsoft Excel Could Allow Remote Code Execution (Replaces MS12-030 MS12-051 ) | |||||
|
Excel 2003, Excel 2007, Excel 2010, Excel 2008 on Mac CVE-2012-1885 CVE-2012-1886 CVE-2012-1887 CVE-2012-2543 |
KB 2720184 | no known exploit |
Severity:Important Exploitability: 1,1,1,1 |
Critical | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
-
We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
(**): The exploitability rating we show is the worst of them all due to the too large number of ratings Microsoft assigns to some of the patches.
------
Post suggestions or comments in the section below or send us any questions or comments in the contact form
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
5 Comments
Request for info: Robocall Phishing Against Local/Regional Banks
Last week, my wife got an automated call from a bank with only a local presence that her debit card was deactivated. The call went to her cell phone. She wasn't a customer of that bank so it was easy for her to discard the call (I am a customer with my commercial accounts). It seems they simply wardialed every phone number with the right area code and three digit exchange in the area of that bank.
Looking to correlate data, the attack isn't new or particularly novel, but curious if it has been seen this month in other areas of the United States. Please drop a line with some details if so.
It goes without saying, if someone calls you asking for personal information, ask for a call back number and/or tell them you will call the customer service number in the phone book.
Thanks!
--
John Bambenek
bambenek \at\ gmail /dot/ com
Bambenek Consulting
9 Comments
Fresh batch of Microsoft patches next week
Next week Microsoft will release 6 new security bullitins. Of the six bulletins, five of them are critical and allow for remote execution of code. The pre-notification information indicates that the vulnerabilities are in Microsoft Office, Windows Server Platforms, the Desktop Platforms and Windows RT (Surface). It looks like next Tuesday will be interesting. Read more about it at the link below.
http://technet.microsoft.com/en-us/security/bulletin/ms12-nov
0 Comments
Remote Diagnostics with PSR
Have you ever been in this situation? Someone calls you for help and tries to explain their problem. They do such a poor job of explaining what they are seeing that you aren’t even sure what OS they are using much less how to fix their problem. You wish you had some way of remotely seeing their desktop, but the user is incapable of following instructions required for you to remotely connect to and administer their machine. This is especially frustrating when you are in the identification or containment phase of an incident. Communications is an essential element of handling incidents effectively. When you are in a pinch, here is a new tool to add to your tool belt.
Microsoft Windows 7 has a tool called PSR (Problem Sequence Recorder). PSR will capture screen images, mouse clicks and some keyboard input and put in into a zip file that can be emailed back to you. The information is recorded in the sequence that the user sees it. You can see what they clicked and the order in which they clicked it. You can see what was on their screen and to a very limited extent what they typed. If you just run PSR.EXE it will bring up a GUI (graphical user interface). It is really easy to use. It has a start button and a stop button. When you click stop it prompts you to save a file. It produces a zip file containing the diagnostic information that the user can email to you (assuming that they have SOME connectivity).
While the GUI is pretty simple, PSR has whole bunch of useful CLI (Command Line Interface) options. Instead of having them run the GUI you could have them run the following at the start line (Explorer Run).
psr.exe /start /output \\?\%USERPROFILE%\Desktop\diag.zip /maxsc 100 /sc 1 /gui 0
That will start recording the user’s screens, keys and clicks. “/output <path>” defines the path and file that will contain the screen captures and the rest of the data. “/maxsc 100” changes the maximum number of screen captures it will capture from the default of 25 to 100. “/sc 1” turns on screen captures. Alternatively if you don’t want screen captures you can turn them off with “/sc 0”. “/gui 0” prevents the graphical user interface from displaying. User interactions will be recorded until you run the following:
psr.exe /stop
This will create a file called “diag.zip” on the user’s desktop where they can grab it and send it to you. When you open it up you will find a .mth file with lots of useful information. When you open it with Internet Explorer you will see something like this:
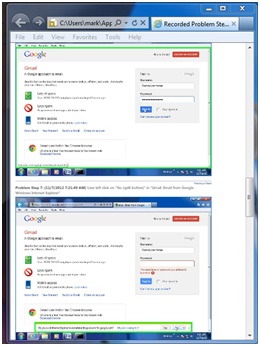
The green box shows where the user clicked on the screen. You can use this to see exactly what is on the user’s screen and make a more informed decision about how to respond.
I first started looking at PSR as a penetration testing tool. As you might imagine, the ability to capture screenshots, mouse clicks and keystrokes invisibly in the background is potentially useful to a penetration tester. However, I think it is more useful as an incident response tool. The screenshots can be useful to a penetration tester, but it doesn’t record all the keystrokes. You can include Event Tracing logs with the “/arcetl 1” option. Pauldotcom.com readers might know that I am very fond of ETW logs being used as a keylogger in a penetration test.
There are other interesting CLI options. For example, you can specify that you only want to record interactions with a specific process with the “/recordpid <process id#>” option. Here is the official list of CLI options from Microsoft's website. Examining the binary I notice there is also an undocumented “/uisavedir <directory>” option. For more information you can check out Microsoft's website at the link below. The list of command line options and examples from the Microsoft website are also below.
PSR Command Line Options
psr.exe [/start |/stop][/output <fullfilepath>] [/sc (0|1)] [/maxsc <value>]
[/sketch (0|1)] [/slides (0|1)] [/gui (0|1)]
[/arcetl (0|1)] [/arcxml (0|1)] [/arcmht (0|1)]
[/stopevent <eventname>] [/maxlogsize <value>] [/recordpid <pid>]
/start Start Recording. (Outputpath flag SHOULD be specified)
/stop Stop Recording.
/sc Capture screenshots for recorded steps.
/maxsc Maximum number of recent screen captures.
/maxlogsize Maximum log file size (in MB) before wrapping occurs.
/gui Display control GUI.
/arcetl Include raw ETW file in archive output.
/arcxml Include MHT file in archive output.
/recordpid Record all actions associated with given PID.
/sketch Sketch UI if no screenshot was saved.
/slides Create slide show HTML pages.
/output Store output of record session in given path.
/stopevent Event to signal after output files are generated.
PSR Usage Examples:
psr.exe
psr.exe /start /output fullfilepath.zip /sc1 /gui 0 /record <PID> /stopevent <eventname> /arcetl 1
psr.exe /start /output fullfilepath.xml /gui 0 /recordpid <PID> /stopevent <eventname>
psr.exe /start /output fullfilepath.xml /gui 0 /sc 1 /maxsc <number> /maxlogsize <value> /stopevent <eventname>
psr.exe /start /output %temp%\%computername%_PSR.zip /sc 1 /gui 1 /arcetl 1 /arcxml 1 /sketch 1 /slides 1
psr.exe /stop
Join me in San Antonio Texas November 27th for SANS 504 Hacker Techniques, Exploits and Incident Response! Register Today!!
Follow me on Twitter @MarkBaggett
Mark Baggett
0 Comments
Adobe Patches
Rumor has it that there is an Adobe Reader (PDF) zero-day. Google "Group IB zero day", and you'll find all the news outlets quoting each other. We don't have a sample PDF yet. If you have one, please share. Needless to say that a PDF exploit is serious, and if indeed embedded in the Blacole exploit kit, is even more serious. Not that the bad guys need PDF though .. it looks to me like 70% of the Internet is anyway still vulnerable to CVE2012-4681 (Java JRE), which has been in Blacole since late August.
Not a rumor: Flash Player has a couple of serious vulnerabilities, and Adobe has the patches: https://www.adobe.com/support/security/bulletins/apsb12-24.html Not that this is news, really. Adobe browser plugin products NOT having serious vulnerabilities for a change .. now THAT would be news.
0 Comments
Get a 40% discount on your hotel room!
Here's a novel (to me) phishing approach. Cal, one of our readers, was staying at a hotel in Arizona on business, and he got a call to his room from the - alleged - front desk. They were saying that their computer had gone down, and that they needed to re-verify his billing information.
Cute, isn't it.
Being a security geek, Cal didn't fall for it, said that he was currently talking on his mobile phone with his wife, and whether he could call back. Not surprisingly, the "front desk" seemed a tad reluctant to provide a number. Stalemate. That's when the phish caller came up with a very customer service oriented approach: "We really regret this trouble, and we will gladly offer you 40% off your room rate for the inconvenience"
But no dice: Not even the prospect of a "rebate" was sufficient to convince Cal to hand out his personal data and credit card information to an unknown caller. He hung up, walked down to the front desk, and upon asking, the lady at the front desk put her head down and said "You too? They've been calling 201, 203, 204, 210, and now you?"
Given the right circumstances and timing, I'd say quite a few hotel guests would fall for this. Make sure you are not one of them!
1 Comments
Cisco TACACS+ Authentication Bypass
Cisco has released a patch that addresses a TACACS+ Authentication Bypass vulnerability. Exploitation is likely very easy. If you are using Cisco ACS for authentication you should probably take note of this annoucment.
The following Cisco Secure ACS versions are affected by this vulnerability:
| Cisco Secure ACS Version | Affected |
|---|---|
| 5.0 | Yes |
| 5.1 | Yes |
| 5.2 | Yes |
| 5.3 | Yes |
| 5.4 | No |
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20121107-acs
Thanks to the ISC reader who asked not to be mentioned by name who brought this to my attention. And thanks to Scott for keeping me straight on the versions.
Join me in San Antonio Texas November 27th for SANS 504 Hacker Techniques, Exploits and Incident Response! Register Today!!
Follow me on Twitter @MarkBaggett
Mark Baggett
0 Comments
Multiple 0-Days Reported!
I'm getting really good feedback on our bug hunt. I've had a couple of people report interesting vulnerabilities to ISC or me directly that they have discovered using the technique outline on the ISC Diary here (https://isc.sans.edu/diary/Help+eliminate+unquoted+path+vulnerabilities/14464). The vulnerability reported can be used by malware instead of creating registry entries to survive a reboot. In cases where the program run as a service they can be used for privilege escaltation.
As you are checking your programs, be sure to occationally check for instances of CALC.EXE running invisibly in the background. Those are sometime the more interesting processes to look at. :)
Thanks to everyone reporting vulnerabilites. Be sure to post a comment on the bug hunt diary and read the comments from other people finding the bugs.
Join me in San Antonio Texas November 27th for SANS 504 Hacker Techniques, Exploits and Incident Response! Register Today!!
Follow me on Twitter @MarkBaggett
Mark Baggett
0 Comments
Help eliminate unquoted path vulnerabilities
Metasploit’s “Service Trusted Path Privilege Escalation” exploit takes advantage of unquoted service paths vulnerability outline in CVE-2005-1185, CVE=2005-2938 and CVE-2000-1128. The vulnerability takes advantage of the way Windows parses directory paths to execute code. Consider the following command line.
C:\windows\system32\notepad \temp\file.txt
This tells windows to launch notepad.exe from the c:\windows\system32\ directory and pass it the argument \temp\file.txt. The result is notepad.exe will execute and begin editing file.txt from the temp directory. How does Window’s differentiate between the program and the arguments? The SPACE is used as a delimiter between the program to execute and the arguments. Now consider this command line.
C:\program files\Microsoft Office\Winword.exe
If space is used as a delimiter, wouldn’t Windows think you are trying to execute the program C:\PROGRAM.EXE and pass it the argument “files\Microsoft Office\Winword.exe”? Or maybe you are trying to execute “C:\Program files\Microsoft.exe” and pass it the argument “Office\Winword.exe”? So how does it know what you are trying to do? If the software developer places quotation marks around the path then Windows knows the spaces are spaces and not delimiters. If the software developer fails to put the path in quotes then Windows just doesn’t know. If Windows doesn’t know then it tries to execute all the possible programs in the path. First it tries “C:\Program.exe”, Then, it tries “C:\Program files\Microsoft.exe” and finally the path we intended for it to execute.
This programming error is very common because when a developer is addressing paths on the file system they are usually stored in strings. Because they are in strings the developer has used quotes once already and they often fail to consider that they need two sets of quotes. For example, the following line would incorrectly assign the path variable.
pathvariable = “C:\Program Files\Common Files\Java\Java Update\jusched.exe”
Really, the developer needs to double quote it because they need the path to contain quotes. So they should have assigned their variable by doing something like this:
pathvariable = “\\”C:\Program Files\Common Files\Java\Java Update\jusched.exe\\””
In the first case, an attacker can strategically place a program in the path and his program will be executed instead of the intended program. If the process runs under administrative privileges or some account other than the attacker it can be used to cause code to execute under a different set of privileges.
We have known about these types of vulnerabilities for 12 years now. So much so, that if you create a file called c:\program.exe Windows will generate this pop up when you reboot the machine.
With such an old vulnerability, surely very few programs suffer from this problem, right? You might be surprised at how often this vulnerability occurs. So let’s start fixing it! This is an easy problem to identify. Here are some steps you can follow to identify applications that fail to quote their file paths directly. Then you can help fix this by contacting the vendor to have them fix these issues.
First you need to copy any existing executable and create a program named c:\program.exe. For example, take a copy of calc.exe and name it c:\program.exe. Then make a copy of calc.exe named c:\program files\common.exe. Last, create a copy of calc.exe called c:\documents.exe. Then go about your business and use your computer as you normally would. Sometime while you are running normal applications they will accidently launch the renamed calc.exe. System reboots, services and scheduled tasks may trigger calculator. Whatever the cause, eventually you will likely run a vulnerable program and it will launch the application on your computer. Several days may transpire between the time you create the files and the time they are executed. Remember you did this when you have strange copies of calc.exe spontaneously launching on your computer. Once one your copy of calculator executes, first find out which one of your calc.exe programs launched and who launched it. Use WMIC to query which copy of your calculator is running like this.
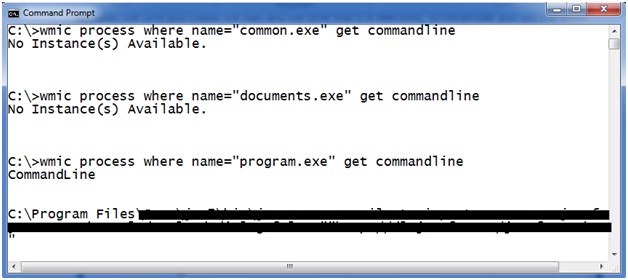
Here you can see this query for “program.exe” returns the command line that was executed when our executable launched. This program failed to properly quote the system paths and launched your renamed program. Often times you may be able to identify the vendor responsible for the software from just the command line that launched your program. But often times it is also useful to know the parent process that launched the command line that started your program. To find out what program launched the unquoted path we use the following commands.
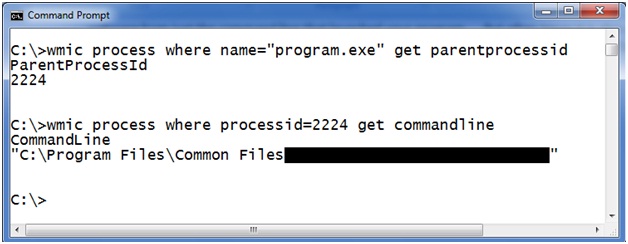
There you go bug hunter. You found a 0-Day vulnerability! Now notify the vendor so they can patch it and keep everyone safe. While you are at it you can notify us if you would like.
Join me in San Antonio Texas November 27th for SANS 504 Hacker Techniques, Exploits and Incident Response! Register Today!!
Follow me on Twitter @MarkBaggett
Mark Baggett
Update: Here are some additional references. Thanks to altonius for the links
http://blakhal0.blogspot.com/2012/08/hiding-files-by-exploiting-spaces-in.html
19 Comments
What to watch out For on Election Day
Today (Tuesday) is election day in the US. Many voters have already cast their ballot via absentee and early voting, but the vast majority will vote today. Like any major event, this is likely going to be used and abused in some way online. Here are some of the network security related issues to watch out for:
Search Engine Poisoning
This is an issue we have certainly seen less off this year. Search engines appear to get a better handle at poisoning of common search terms by black hat SEO operations. But it doesn't mean it isn't happening, and this is an event with a long lead time so it is possible that we see something new and different.
Social Media Links
Facebook as been pretty crowded lately with statements supporting various candidates. So far, I haven't seen this used maliciously, but it is an obvious easy target to introduce a link to a malicious version of a popular video clip. Of course fake late breaking news could be used to sway some last minute decisions, but it is likely too late for that.
DDoS Attacks
This year, we have seen plenty of politically motivated DDoS attacks. It would be no surprise, to see more of that tomorrow. On the other hand, large news sites will see record viewer numbers, and likely very dynamic frequently updated content. This will make them even more vulnerable to a DDoS attack, or it may be hard to figure out if a site is down or slow due to a DDoS attack or just "normal" high load. If you still have a TV or a Radio, it maybe a more reliable source of the latest news.
Twitter Hype
We have seen some use of twitter to amplify fringe messages in the last couple months. For example stories about looting ahead of the hurricane Sandy, or suggestions of riots after the election. Needless to say: It is not true if it is tweeted. (even though it is on the internet, and we know everything on the internet is true ;-) ). Don't spread/re-tweet rumors. Also, the "late breaking scandal" may use twitter. See the "social media" comment above.
Polling Place Locations
Refer to official guides, and official websites to find out where to vote. Polling places can change from election to election and you may be standing in line only to be told that you are in the wrong location. So far, this has not been abused but misinformation has been spread via outdated unofficial sites.
Summary
only use official information from the original official source. If at all possible, use printed material like sample ballots that you received in the mail (not that they are always right), and refer to URLs that you have bookmarked in the past. There have been some news reports that areas affected by hurricane Sandy will allow for special voting arrangements like e-mail. Please confirm with an official source before e-mailing or faxing your vote. I will try and collect some of these sources here later.
Anything I forgot? (of course: go and vote if you are eligible to do so).
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Possible Fake-AV Ads from Doubleclick Servers
Reader James ran into a Fake AV ad delivered by Double click. It is not clear if this is the result of a compromise of double click, or a paid ad that slipped through doubleclick's content review process. James' started out at a local new paper web site, that like many others features ads served by double click. Luckily, James used a proxy tool (Fiddler) to record the session. Here are some of the excerpts (slightly anonymized and spaces inserted to avoid accidental clicks):
GETÂ http://ad.doubleclick.net/adj/mi.ida00/News;atf=n;dcove=d;pl=sectfront;sect=News;
pos=2;sz=300x250;tile=8;!c=news;gender=;year=;income=;ord=230528779772346? HTTP/1.1
Accept: */*
Referer: [local newspaper URL]
Accept-Language: en-us
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; [...]
Accept-Encoding: gzip, deflate
Host: ad.doubleclick.net
Connection: Keep-Alive
Cookie: id=xxxxa||t=1352150000|et=730|cs=yyyy
The reply to this request was:
HTTP/1.1 200 OK
Content-Type: application/x-javascript
Content-Length: 167
Date: Mon, 05 Nov 2012 22:32:59 GMT
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
Reminder: Ongoing SMTP Brute Forcing Attacks
Our reader (and podcast listener) Pete wrote in with a little SMTP log snippet:
2012-11-04 22:37:36 courier_login authenticator failed for 153.red-2-139-216.staticip.rima-tde.net ([192.168.2.33]) [2.139.216.153]:4232: 535 Incorrect authentication data (set_id=anna)
2012-11-04 22:37:36 courier_login authenticator failed for 153.red-2-139-216.staticip.rima-tde.net ([192.168.2.33]) [2.139.216.153]:4232: 535 Incorrect authentication data (set_id=anna)
2012-11-04 22:37:37 courier_login authenticator failed for 153.red-2-139-216.staticip.rima-tde.net ([192.168.2.33]) [2.139.216.153]:4232: 535 Incorrect authentication data (set_id=anna)
2012-11-04 22:37:37 courier_login authenticator failed for 153.red-2-139-216.staticip.rima-tde.net ([192.168.2.33]) [2.139.216.153]:4232: 535 Incorrect authentication data (set_id=anna)
2012-11-04 22:37:38 courier_login authenticator failed for 153.red-2-139-216.staticip.rima-tde.net ([192.168.2.33]) [2.139.216.153]:4232: 535 Incorrect authentication data (set_id=anna)
In this case, the attacker is '2.139.216.153'. According to our DShield data, the host has a history of port 25 scanning, and evidently, participates in these brute force attacks once it finds port 25 open. (see https://isc.sans.edu/ipdetails.html?ip=2.139.216.153 ).
But this is just one of many IPs that Pete sees coming into his network. They all use "192.168.2.33" as hostname, which appears to be hard coded into the bot used to produce these scans.
Typically, these scans try to brute force SMTP credentials (not POP/IMAP credentials) to send spam via your users e-mail accounts. A few tips to help mitigate these attacks:
- enable rate limits for inbound authentication attempts. This will at least slow down the attack. (consult your mail servers manual for details. Each server is different)
- enable reasonable rate limits for outbound email. This way, it is easier to detect compromised accounts, and the account is of less value to the spammer
- do not rely on passwords. Use SSL client certificates (or at least enforce a strong password policy)
- only allow connections to send mail from inside your network, or via a VPN.
Any other ideas? FWIW: I do not recommend strict "lock out" policies for mail servers. They can make it impossible to change your SMTP password. Many users will use multiple devices these days, and if you for example lock an account after 3 bad logins, a user changing a password will be locked out as the users cell phone / tablet will continue to use the old password until it is changed. If you do implement lock out, then please communicate this to your users and ask them to first turn off all devices (that can be challenging as they may not even remember which devices they have) and then change their password.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
What's important on your network?
Often when you ask someone what is important on their network, they will say "Everything". But that cannot be the case. You have to determine your High Value Targets first. A High Value Target is a device, system, database or resource that you cannot live without and still accomplish your mission. If you look at this from a military perspective, it is the key targets that can win you or lose you the war. This may seem like common sense, but strangely many people have not considered this. We protect networks so they can accomplish some defined mission whether it be information sharing or business related as examples. Too often its seems we forget the mission part and don't really factor it into why we are doing security; whether designing an infrastructure or monitoring that infrastructure. It becomes just a checklist....IDS (check)...Firewall(check)...Antivirus(check)...logs(check)...but are you really focusing on what is critical?
To protect a network/resource properly, you have to know your High Value Targets. In order to do this, your going to have to talk with your different business areas that make up your company/organization and understand what is important to them and what risk are they willing to take. It may be that you have to help guide them to even get them to understand what you are asking. That is ok, because it shows them that you are concerned and your are willing to take the time to help them and help yourself learn. If you don't understand what is important to the company/organization, then your ability to design or monitor an infrastructure effectively is greatly diminished. I would venture to say that we do a better job understanding our High Value Targets when it comes to designing the infrastructure but we fail when it comes to understanding it in order to effectively monitor it. If you asked all your analysts on your different shifts (or however your monitoring) what the top five High Value Targets were on your network, what answers would you get? Would those answers line up with the business owners? An attack or anomalous traffic toward one asset may not be that worrying, but what if its toward one of your High Value Targets?
In today's world, the threat has become very tailored and very specific. We have so much traffic to monitor on our infrastructures today that we have to have a tailored and structured approach to monitoring. You have to know what has the priority when it comes to protecting and/or monitoring. What can't the company/organization live without? I can assure your that the attacker is trying to find or already knows your high value targets. The real question is do you know what they are?
4 Comments
Lamiabiocasa
Earlier today, ISC reader Travis noticed that his proxy server was blocking some images from BusinessWeek Business Exchange (bx.businessweek.com). On closer inspection of the blocked content, he found that some files indeed had peculiar contents:
1 Comments
The shortcomings of anti-virus software
No, this isn't about lousy detection rate. I think we're pretty much resigned to that, irrespective of the latest fancy marketing terms the industry uses to sell us the same failed concept. This is about the forensic quality, or rather lack thereof, of anti-virus.
Let's say your anti-virus (AV) happens to find a Spyware. Something like the spyware that I described in yesterday's ISC diary. What does it do with it? If your AV is anything like the products that I've seen in use, it will display a Halloween-like scary pop-up ("Danger! Virus!") and will delete or quarantine the threat.
So far so good. This used to be cool back when all we wanted our anti-virus to do was to get rid of the threat. But these days are over. Increasingly now, anti-virus alerts us (maybe) to a persistent threat that has been on the system for days, weeks, heck, even months. And deleting or quarantining such a threat causes a serious problem: It modifies or eradicates evidence. Yes, we get an alert, but then we are like the CSI guys who get called to a murder scene that doesn't have a body. Sure we can spend hours trying to lift DNA off cigarette stubs, but things would be so much easier if the caller could tell us what exactly he has seen where, and where the body was?
In other words: If anti-virus removes a registry key to unhook a DLL, why can't the AV log tell me (a) where this registry key was and (b) when it was created? You know, this would give a first indication on how far back we have to dig to determine what data was stolen. The same holds true for the actual threat files that get deleted or quarantined: A full MAC (modify/access/create) timestamp in the logs shouldn't be too much to ask for? Maybe garnished with an MD5 checksum for good measure, so that the analyst can tell right away if the exact same threat has been seen on another PC already?
I don't think the AV companies have caught on to this yet - they seem to be deleting and quarantining threats with the same casual indifference like they did 20 years ago, stomping all over the crime scene, and wiping out or contaminating important forensic evidence in the process.
If your enterprise-grade anti-virus software does any better in forensics than described above, please let us know via the contact page. If it has the same shortcomings, please let us know as well, but more importantly, please let your AV vendor know. Maybe, someone listens.
10 Comments
Patched your Java yet?
Yes, there's some irony to this diary entry. In the past, I have been suggesting repeatedly that organizations who do not have an all-out requirement to keep a Java JRE runtime installed, should get rid of it. Yet, here I was, a couple of days ago, reviewing some SIEM events at a Community College where I help out with IT Security, when something caught my eye (URLs defanged to keep you from clicking):
src='192.168.36.25' media-type='application/x-jar' url='GET hxxp://outdrygodo.mine. nu/finance/etzko5.jar'
src='192.168.36.25' media-type='-' url='GET hxxp://outdrygodo.mine. nu/finance/qkefaw.php'
src='192.168.36.25' media-type='application/octet-stream' url='GET hxxp://outdrygodo.mine. nu/finance/e32ezw.php?category=/&news_id=314214&date=1012&gen=j&lam=true'
Basically, a user here is getting an unsolicited Java Applet. A little while later, the same workstation gets an "octet stream" (think: executable). This can't be good. But why isn't anti-virus alerting on it? [Yes, this is a purely rhetorical question :)]
Turns out, the workstation in fact has been infected. The JAR contained an exploit for CVE-2012-4681. And there is a "skype.dll" sitting in C:\ProgramData, and, even "better", it apparently happily talks to some server in the Ukraine:
src='192.168.36.25' media-type='-' url='POST hxxp://195.191.56. 242/posting.php?mode=reply&f=72&sid5=0ef2884d693eadc605e9bf726c1b9881'
Checking through the logs in detail now, we determined that the PC was talking to this server in the Ukraine whenever the user was logging into some web page. User goes to GMail? PC talks to the Ukraine. User goes to Amazon? PC talks to the Ukraine. User goes to online bank? Yup: you get the drift. In between, the spyware kept mum. But whenever the user happened to enter some password, the spyware merrily ratted him out.
Looking through the logs even further back, we were able to determine that the original infection had happened when the user visited a - perfectly benign - newspaper web site, which at the time apparently was featuring a poisoned advertisement banner somewhere within the page content. The entire attack happened compeletely stealthily, there is nothing the user could have seen or done (maybe with the exception of Java popping up in the tray, but who pays attention to that?)
In short, if your Java JRE is unpatched, you will get hacked. Silently and stealthily. The bad guys will grab all your passwords for a week or so. And then, they will move in, and change your life.
In the case at hand, it was an e-banking application, of all things, that did not yet work with Java JRE 7, and had kept the user from upgrading his Java JRE. From other users, I hear that some releases of enterprise software from large vendors like SAP, Oracle, etc, are also not fully compatible with the latest Java JRE, and thus force their users to remain exposed to attacks like the one described above.
Bottom line:
If you don't need Java JRE on your PC, get rid of it.
If you need it, patch it.
If you can't patch it because some silly application is not compatible with the patch, kick the [beep] of whoever supplies that application.
In case you are in the latter situation, feel free to share in the comments box below. Maybe there are other ISC readers similarly affected, and if you join forces, the vendor might be more inclined to listen.
21 Comments




0 Comments