Mark of the Web: Some Technical Details
The Mark of the Web (MoTW) is file metadata in Windows that marks a file that was obtained from an untrusted source.
When a file is downloaded from the Internet, browsers will not only write the file to disk, but also include metadata with the origin of the file. This also applies when an email attachment is saved to disk with Outlook.
This metadata (MoTW) is used by several applications to activate extra precautions when a file from an untrusted source is opened. For exampe, Microsoft Office will open a document downloaded from the Internet in Protected View (indicated by the yellow banner), SmartScreen will prompt you before a file is launched, ...
The metadata/MoTW is stored in an Alternate Data Stream on NTFS disks. The name of this ADS is Zone.Identifier.
You can view this with Notepad, for example. Say that you downloaded a file from the Internet called invoice.docx, then you can view the MoTW with this command:
notepad.exe invoice.docx:Zone.Identifier
And you will see something like this:
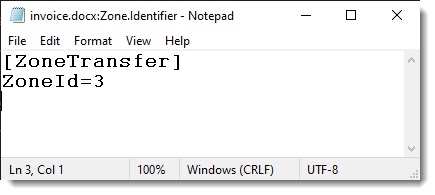
ZoneId 3 is the Internet.
Here are the possible values:
| Zone ID | Displayname | Description |
|---|---|---|
| 0 | Computer | Your computer |
| 1 | Local intranet | This zone contains all Web sites that are on your organization’s intranet. |
| 2 | Trusted sites | This zone contains Web sites that you trust not to damage your computer or data. |
| 3 | Internet | This zone contains all Web sites you haven’t placed in other zones |
| 4 | Restricted sites | This zone contains Web sites that could potentially damage your computer or data. |
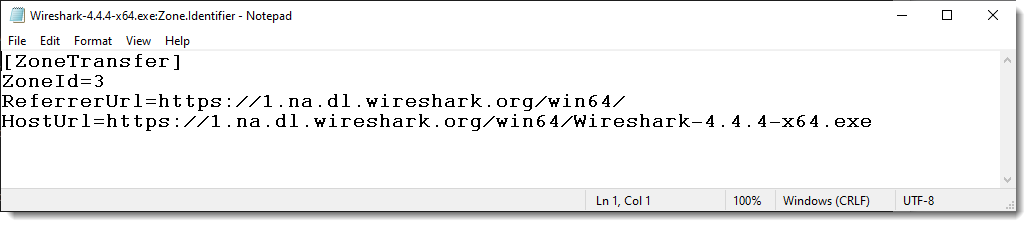
Browsers will also add fields that record the URL, like this:
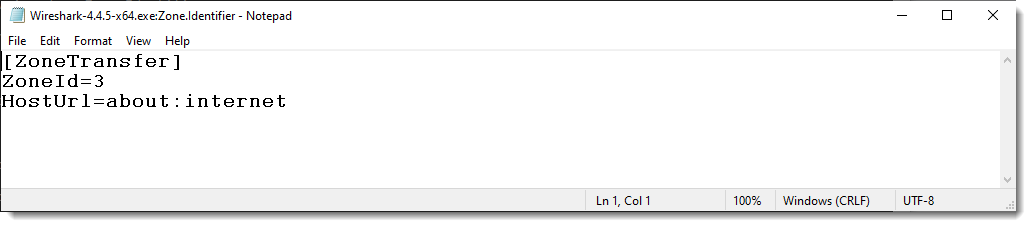
If this is done in incognito mode, then the URL is not recorded:
This MoTW is propagated when a file is copied (to another NTFS disk).
It is also propagated by various applications that handle container formats. For example, many archiving utilities will copy the MoTW from a download ZIP file to the extracted files. Sometimes this needs to be configured, like with 7-Zip. WinRAR is also a bit special, I'll write about this in another diary entry.
Threat actors are always on the lookout for new methods to bypass MoTW propagation, so stay vigilant.
Didier Stevens
Senior handler
blog.DidierStevens.com


Comments