Unveiling the Mirai: Insights into Recent DShield Honeypot Activity [Guest Diary]
[This is a Guest Diary by Elias Bou Zeid, an ISC intern as part of the SANS.edu BACS program]
Introduction
In this digital age, as our dependence on technology grows, understanding which devices are connected to our networks and keeping track of their security updates is critically important. In this post, I dig into my instance of the DShield honeypot to see what attack vectors malicious actors are trying to exploit. What I found were several attempts to upload the Mirai family of malware. This finding serves as a stark reminder of the vast amounts of vulnerabilities available in the wild.
Description of Mirai
Mirai, a notorious malware strain, has caused a disruption since its inception. Designed to exploit the security weaknesses in IoT (Internet of Things) devices, it converts these devices into a network of bots, or a 'botnet,' used to launch large-scale network attacks. The fact that malicious actors are still leveraging Mirai is a showcase of Mirai's capabilities and its evolving threat landscape. [1]
Mirai Overview
The method in which Mirai infiltrated numerous IoT devices was through common vulnerabilities, such as weak and default username and password combinations. Once Mirai gains access to a system, it carries out its primary function – to enslave devices and coordinate them for massive Distributed Denial of Service (DDoS) attacks. Mirai’s evasion & persistence mechanisms include but are not limited to the following[2][7]:
- Rapid Propagation: Once a device is infected, Mirai immediately seeks out new devices to infect.
- Binary Removal: After successful infection and propagation, Mirai often deletes its binary from the disk to reduce its footprint.
- Implements persistence mechanisms suitable for various Linux distributions.
- Memory Residency: Mirai's main persistence method is running in adevice's RAM. Even if its binary is removed from the filesystem, the malware remains active in memory.
- Watchdog Process: Mirai can initiate a watchdog process to monitor and restart its main process if terminated, maintaining its active presence.
- Blocking Ports: To prevent re-infection or infection by other competing malware, Mirai often blocks specific ports on the infected device
Infection Diagram and Order of Operations [6]
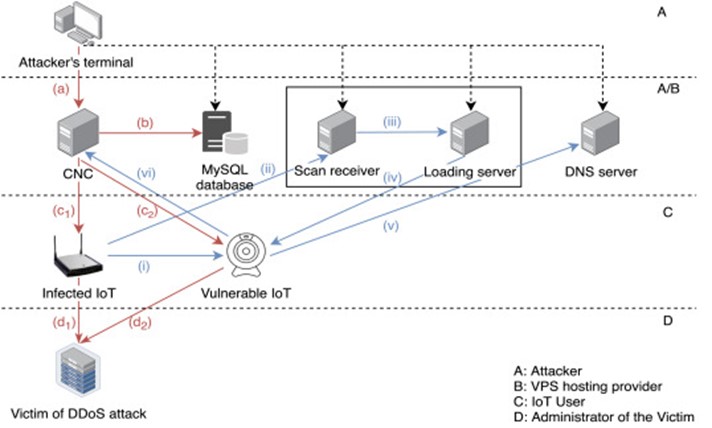
Mirai Botnet Components
- Command & Control (CNC) server
- MySQL database server
- Scan Receiver
- Loading server (Loader)
- DNS server
- Vulnerable IoT devices
Infection Process
1. Infected IoT device searches for vulnerable IoT devices
2. Vulnerable device details sent to Scan Receiver
3. Loader captures vulnerable device's info
4. Loader uploads malware to vulnerable device
5. New bot registers with CNC server
6. New bot retrieves CNC server IP from DNS server
DDoS Attack Process
1. Attacker sends command from Remote Terminal to CNC server via Telnet (step a)
2. Command logged in MySQL database (step b)
3. Attack target forwarded to infected IoT devices (bots) (step c)
4. Bots send network packet flood to target (step d)
What Devices are Mirai’s Main Target?
The main targets for Mirai are IoT devices (smart speakers, cameras, and smart home connected equipment) that have weak Telnet (port 23) and SSH (port 22) credentials. While the primary targets of Mirai are IoT devices, the elementary tactics it uses (exploiting weak credentials), could probably be applied to other types of systems that share similar vulnerabilities. However, its code and method of operation are specifically tailored for IoT environments. [1][2][3]
Log & PCAP Collection, Will It Help Detect Mirai?
As the somewhat recent adage goes, “Packets or It Didn't Happen” is very applicable in a situation like this. Collecting logs/PCAPs is an important strategy in identifying and monitoring threats against IoT devices. These logs/PCAPs are beneficial in revealing device activities, aiding in the detection of anomalies, unauthorized access, and malware infections like Mirai.
Some aspects of log monitoring include detecting unauthorized access through the analysis of login attempts, tracking device behavior to spot deviations from baseline, identifying malware activity through unusual network traffic (C2 traffic), and providing an audit trail for forensic analysis in the event of a breach. [5]
Additionally, for some organizations under regulatory scrutiny, log collection not only fulfills compliance mandates but also assists in incident reporting and documentation. This comprehensive approach is essential for maintaining the security and integrity of IoT devices in today’s evolving threat landscape.
Tools such as SiLK and Zeek can help parse large PCAP repositories for analysis.
How To Protect Devices from Mirai
Combating threats like Mirai requires a multi-faceted approach. Key strategies include[2]:
1. Implementing strong, unique passwords for all IoT devices and changing them regularly.
2. Limiting remote access capabilities like SSH (Secure Shell) and Telnet to devices, ensuring only necessary connections and devices are allowed.
3. Regularly updating firmware and software to patch any security vulnerabilities.
Defining the Key Question
This post aims to answer one crucial question: "What strategies can individuals and organizations, which most of whom utilize IoT devices, safeguard themselves against advanced malware attacks such as Mirai?"
The Importance of the Issue
Understanding and preparing for threats like Mirai goes beyond just safeguarding our data; it's about preserving our accustomed lifestyles, and the way we operate. As we continue to integrate digital solutions into the majority of aspects of our lives, the attack vectors of such threats grow, jeopardizing not just individual privacy and security but also corporate and national stability.
Who Stands to Gain and Why?
This information is crucial for a wide range of audiences:
- IT professionals can use these insights to strengthen their organization's defenses against similar attacks.
- Cybersecurity experts will find detailed analysis of Mirai's mechanisms useful for developing more robust security solutions.
- The general public, especially those with IoT devices, can benefit from understanding how to secure their personal devices.
Summing Up
The Mirai malware is a reminder of the continuous and evolving threats in cyberspace. By understanding how such attacks unfold and implementing proper security measures, and log collection and analysis, we can safeguard our digital infrastructures. It is important that we stay informed, vigilant, and proactive in our approach to cyber security.
IOC’s (malware hashes)
Virustotal: 5466d9405031060ffb564f14b5a263eda12e179287ca4a4a7c94501cd6a25c53
Virustotal: b023af46798a045ce9606318928ed9a96bd64bc25c7279a08b5fee38176e5dc9
[1] https://blog.cloudflare.com/inside-mirai-the-infamous-iot-botnet-a-retrospective-analysis/#:~:text=What%E2%80%99s%20remarkable%20about%20these%20record,devices%2C%20according%20to%20our%20measurements
[2] https://www.cisecurity.org/insights/blog/the-mirai-botnet-threats-and-mitigations#:~:text=IoT%20devices%20built%20for%20convenience,3
[3] https://www.securityweek.com/mirai-variant-v3g4-targets-13-vulnerabilities-to-infect-iot-devices/#:~:text=During%20the%20second%20half%20of,devices%20and%20then%20abuses
[5] https://www.stratosphereips.org/datasets-iot23
[4] https://github.com/jgamblin/Mirai-Source-Code
[6] https://www.sciencedirect.com/science/article/pii/S2666281720300214
[7] https://www.cyfirma.com/blogs/mirai-the-botnet-that-made-iot-dangerous/?sfw=pass1701218240
[8] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments
NachtWache
Jan 3rd 2024
2 years ago