Base64 Hashes Used in Web Scanning
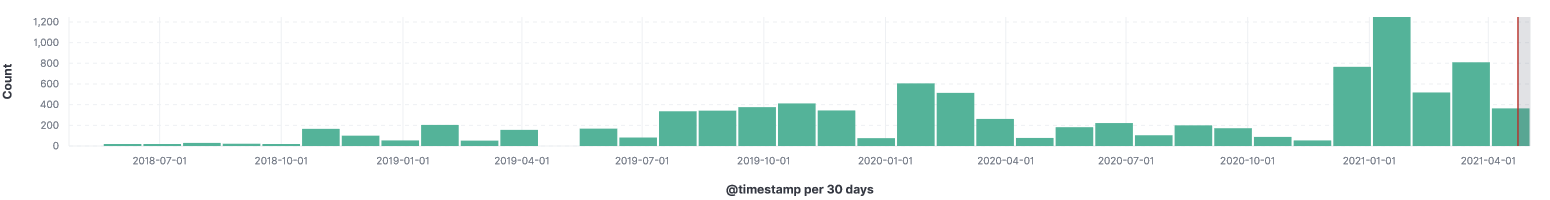
I have honeypot activity logs going back to May 2018 and I was curious what type of username:password combination was stored in the web traffic logs following either the Proxy-Authorization: Basic or Authorization: Basic in each logs. This graph illustrate an increase in web scanning activity for username:password over the past 3 years.
Sample Log
20210422-190644: 192.168.25.9:8088-112.112.86.46:53540 data CONNECT www.voanews.com:443 HTTP/1.1
Host: www.voanews.com:443
Proxy-Authorization: Basic Og==
User-Agent: PycURL/7.43.0 libcurl/7.47.0 GnuTLS/3.4.10 zlib/1.2.8 libidn/1.32 librtmp/2.3
Proxy-Connection: Keep-Alive
The statistic are kind of interesting, username:password combination goes from mostly random to easily recognisable.
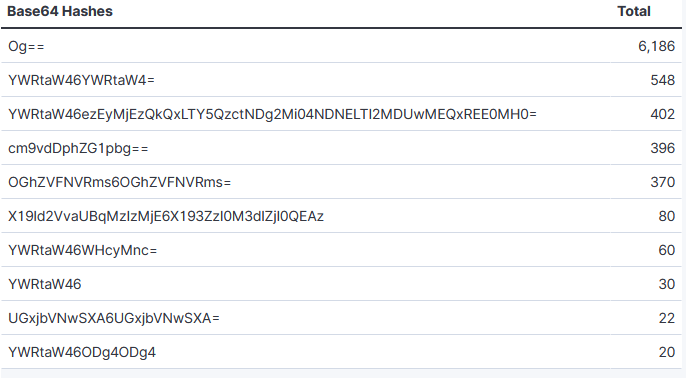
Top 5 Most Popular Hashes
Og== → :
YWRtaW46YWRtaW4= → admin:admin
YWRtaW46ezEyMjEzQkQxLTY5QzctNDg2Mi04NDNELTI2MDUwMEQxREE0MH0= → admin:{12213BD1-69C7-4862-843D-260500D1DA40}
cm9vdDphZG1pbg== → root:admin
X19ld2VvaUBqMzIzMjE6X193ZzI0M3dlZjI0QEAz → __eweoi@j32321:__wg243wef24@@3
Top 10 Hashes
Beside a single column : being the most common empty username:password combination used in the large majority of the scans, admin:admin and root:admin which comes second and forth are still active and popular today. As for the third password, I published a diary in October 2019 about this activity noted active until May 2020, looking for NVMS9000 Digital Video Recorder which goes into more details about this activity [1].
Other often seen username:password combination that are easily guessable:
[email protected]:Jxl112912 admin:
support:admin admin:nbv_12345
root:123456 admin:support
root:1234567890 admin:qwerty
root:123321 admin:123123
root:111111 admin:1234
tomcat:tomcat admin:12345
test:test admin:123456
ubnt:ubnt admin:888888
user:123456 admin:Xw22w
user:1234567890 admin:changeme
user:123321 default
user:111111 user:password
user:admin
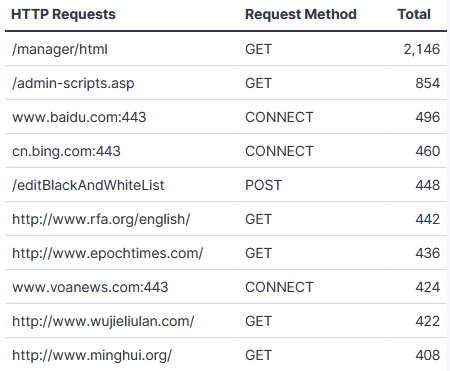
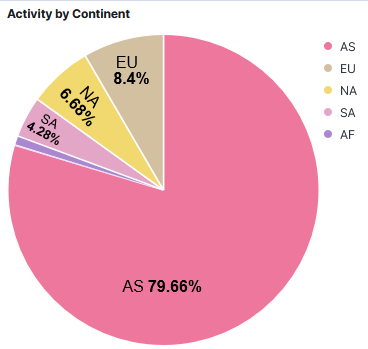
Other interesting stats over the past 3 years is the HTTP requests and the activity by continents.
If unsure what services are being shared to the world, check what Shodan or Censys has been able to discover from a malicious actor perspective. As a home user, you can go to this page to see what Censys has been able to discover on what the router is sharing to the world.
[1] https://isc.sans.edu/forums/diary/Scanning+Activity+for+NVMS9000+Digital+Video+Recorder/25434/
[2] https://isc.sans.edu/forums/diary/Password+Reuse+Strikes+Again/26474
[3] https://isc.sans.edu/forums/diary/Will+You+Put+Your+Password+in+a+Survey/25866
[4] https://isc.sans.edu/forums/diary/Cracking+AD+Domain+Passwords+Password+Assessments+Part+1+Collecting+Hashes/23383
[5] https://isc.sans.edu/forums/diary/Password+History+Insights+Shared+by+a+Reader/22278
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments