BazarLoader phishing lures: plan a Halloween party, get a bonus and be fired in the same afternoon
Phishing messages distributing BazarLoader have come to be commonplace in the past six months, but in the last couple of weeks I’ve been seeing more and more e-mails spreading this malware caught in my quarantine. Although contents of these messages differ, their appearance is usually similar – they all contain a fairly long link to Google Docs along with a text part instructing the recipient to visit the included URL. The lures can range quite widely and the uncoordinated way, in which the messages are distributed, can result in a single recipient receiving fairly amusing combinations of messages. Given the current global not-so-optimistic situation, I thought I’d try to share something a little bit “lighter” today and take a look at some of these messages, but before we get to that, let’s take a short look at the URLs distributed in the e-mails.
Should a recipient click on the Google Docs link, they would be directed to a web page containing a fake preview of a document corresponding to the lure mentioned in the e-mail. The page would also contain download links, from which a victim might seemingly download the promised document. The downloaded file would however insted be a BazarLoader binary.
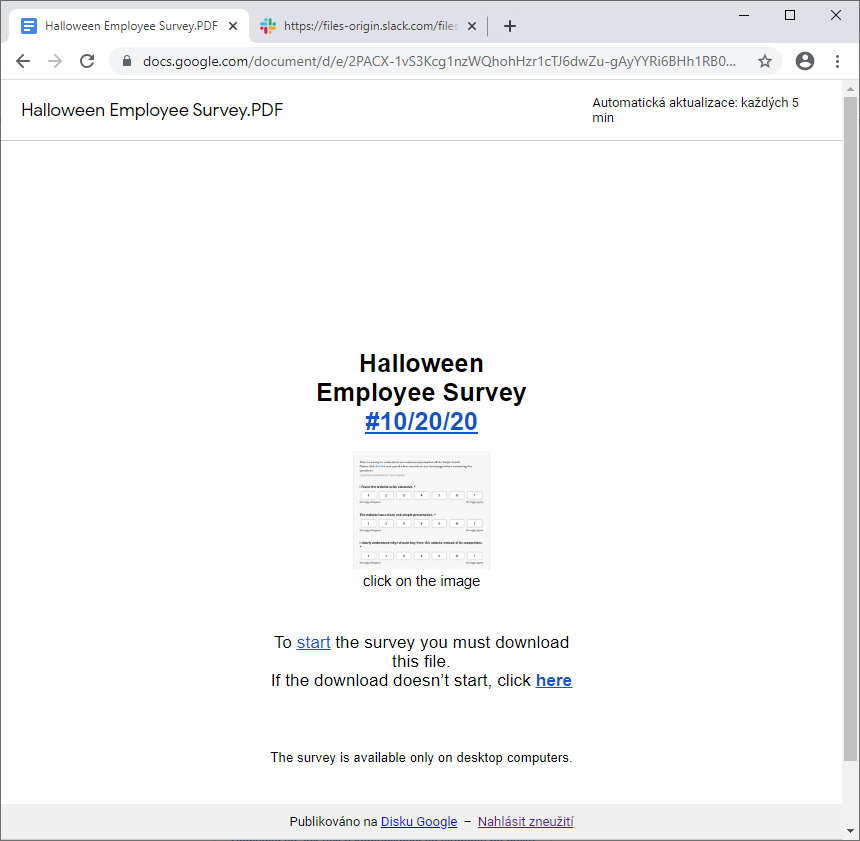
It is worth mentioning that in the latest campaign I’ve seen (the case of “Halloween survey” shown above), the threat actors appeared to use a Slack to host the final payload using the following URL.
hxxps[:]//files-origin[.]slack[.]com/files-pri/T012C3R8D0U-F01D639HZJQ/download/report-review20-10[.]exe?pub_secret=e33269e24f
The link was no longer working when I tried it, but from what I’ve read about Bazar, use of Slack would seem to be a new way of distributing its malicious executables. But back to the phishing e-mails themselves...
As we’ve mentioned, the messages are visually very similar, but the lures differ significantly. And since distribution of these e-mails seems to be completely uncoordinated, reading through those, which one might receive in single a week or two, might make one wonder whether the threat actors aren’t subtly trying to make us embrace the old U.S. Army motto of “Be All You Can Be”.
The reason at least I get this feeling is, that going only by the messages addressed to me personally in the last few weeks:
- I have been probably the most complained-about employee in the company (and I have received several substantial pay cuts because of that)
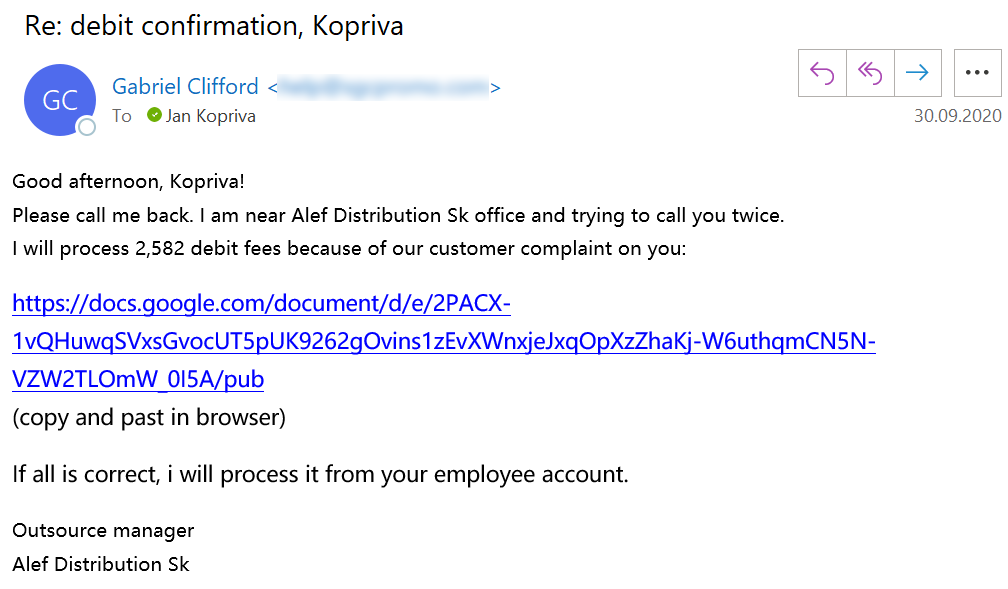
- I was fired (probably due to me ignoring all the customer complaint reviews)
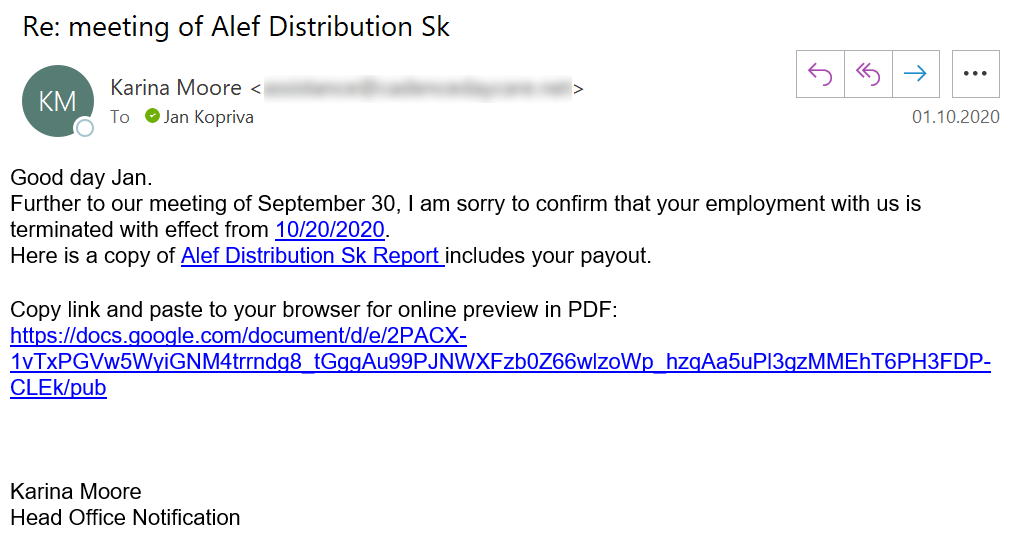
- I have been complained about a number of additional times (I guess they changed their minds on the "termination issue"?)
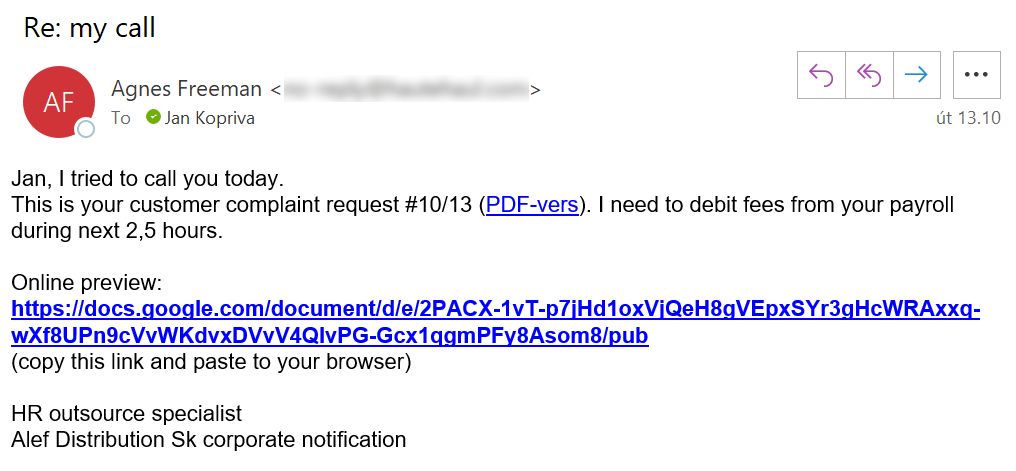
- I was awarded a bonus for being such a good employee (our financial department probably didn’t hear about me not getting on too well with customers…)

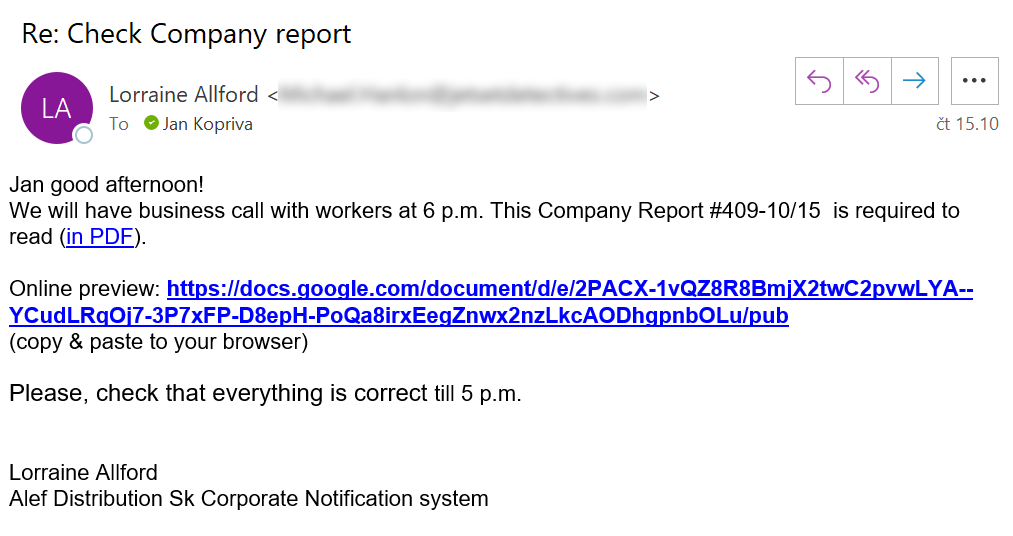
- I was asked to read a company report (hopefully not one mentioning me by name and heavily discussing how to avoid customer complaints)
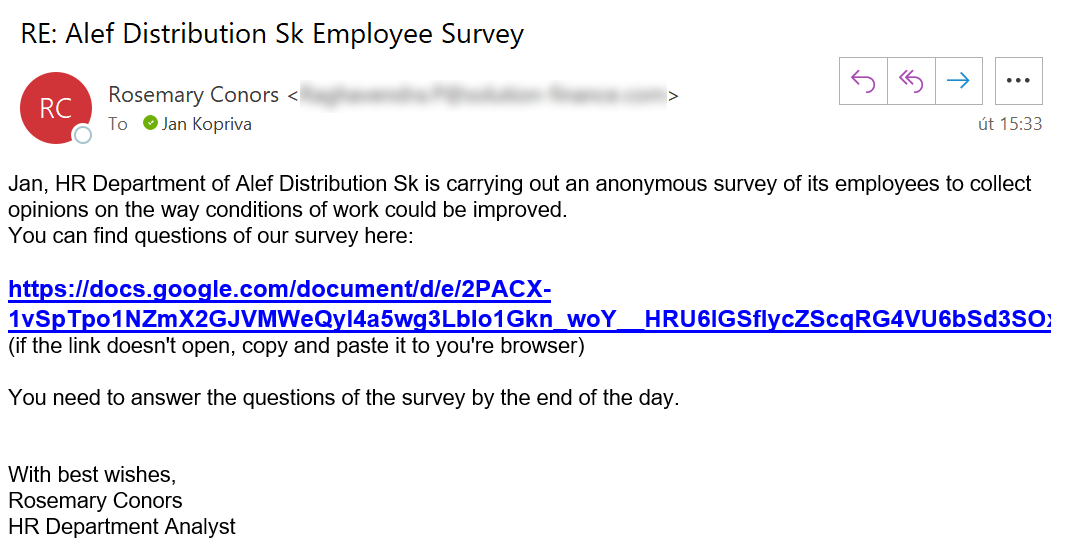
- I was asked to participate in a company survey on improving working conditions (I guess they decided bad working conditions were the main reason for me not being too good with customers...)
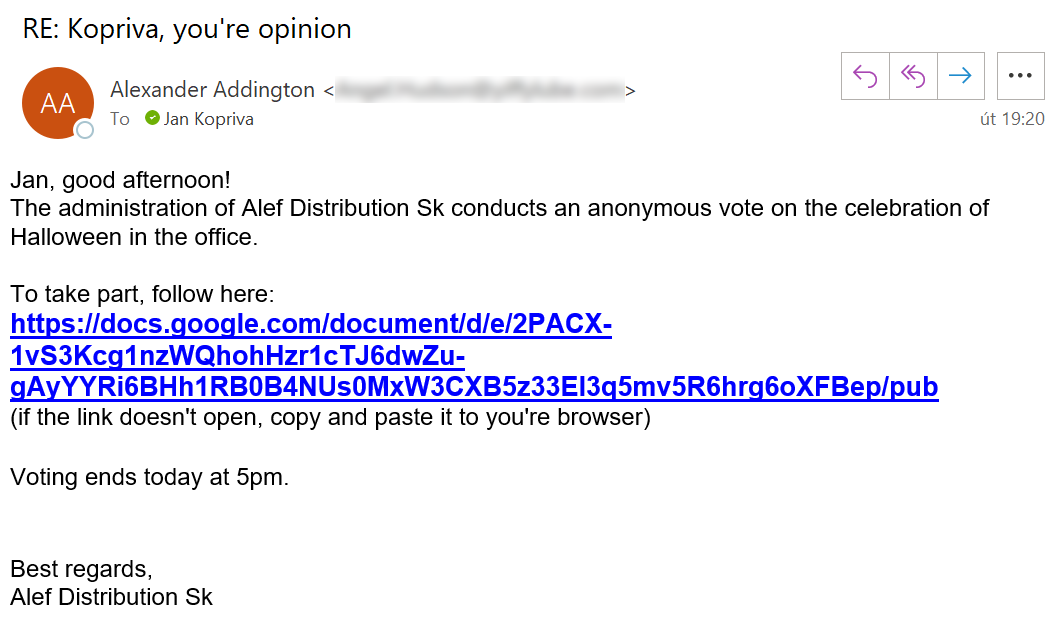
- And finally, this Tuesday I was asked to tell the company how we should celebrate Halloween this year (maybe they have taken my thoughts on how to improve the working conditions to heart?)
Reading through all of these e-mails (and many more), one can’t help but wonder whether sending out similarly looking messages to the same addresses over and over again is really effective for the attackers... Unless their aim is to make the more impressionable recipients feel a bit unsure about the dependability of their memory when it comes to their interactions with customers.
Although I don’t mean to make light of phishing, as it is an undeniable threat, it is good to sometimes take a look at it’s more amusing side. My experience is that this is especially true when it comes to security awareness courses as humor tends to make any examples "stick" a bit more. And since October is a Cybersecurity Awareness Month[1,2], if you haven’t yet shared any tips about how to stay a bit safer online with your less technically-oriented colleagues, maybe showing them the contradictory tone of some of the phishing lures above might not be a bad start...
[1] https://www.cisa.gov/national-cyber-security-awareness-month
[2] https://cybersecuritymonth.eu/


Comments
Anonymous
Oct 22nd 2020
5 years ago
Anonymous
Oct 22nd 2020
5 years ago