Scans for ownCloud Vulnerability (CVE-2023-49103)
Last week, ownCloud released an advisory disclosing a new vulnerability, CVE-2023-49103 [1]. The vulnerability will allow attackers to gain access to admin passwords. To exploit the vulnerability, the attacker will use the "graphapi" app to access the output of "phpinfo". If the ownCloud install runs in a container, it will allow access to admin passwords, mail server credentials, and license keys.
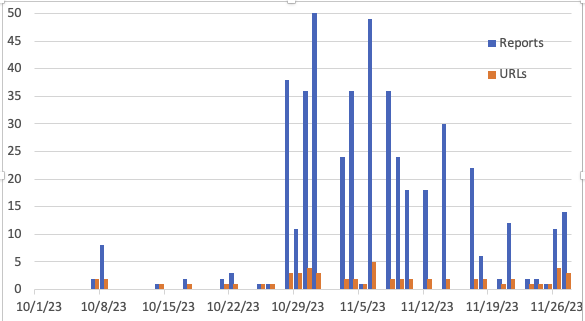
As of Sunday, we are seeing individual scans for one of the affected URLs:
/owncloud/apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php
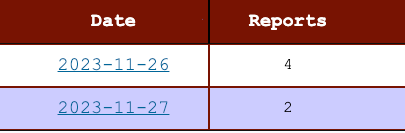
Currently, there are 5 different IPs responsible for these scans:
| IP Address | Details |
| 146.235.221.198 | This IP is part of Oracle's cloud. It has been quite active today, scanning for various exposed files on web servers like ".env". |
| 185.220.101.191 | Tor exit node. As typical for tor exit nodes, this IP is involved in various scans. |
| 104.255.175.10 | This IP, part of H4Y in the US, has been involved in a few scans this last month. The scans look similar to 146.235.221.198. Potentially part of the scam botnet/threat actor. |
| 85.203.44.8 85.203.44.5 |
Part of Portlane in the Netherlands. Only active yesterday looking for ownCloud and sftp-config.json |
Attacks against ownCloud are not rare. There is a pretty steady "trickle" of attacks against ownCloud. Many of them are likely just attempting to find instances of ownCloud to exploit old vulnerabilities or attempt weak passwords.
[1] https://owncloud.com/security-advisories/disclosure-of-sensitive-credentials-and-configuration-in-containerized-deployments/
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments