Quickie: Using radare2 to disassemble shellcode
This post is just a quick place to document a tip/tool that other malware analysts might find useful. As some of you may be aware, I occasionally teach FOR610: Reverse Engineering Malware. I love the class and on days 3-5 we talk about shellcode and discuss various ways of examining shellcode. Also, I've been doing malware analysis for quite a while and have primarily used IDA and OllyDbg (now, x64dbg, since Olly has been abandoned) for it, but I know some of my colleagues really like radare2. I've never had the time to learn radare2, but in a recent case at the $dayjob, I found some shellcode being executed by powershell. Rather than look at it in IDA, I decided to see what I could see in radare2. Since I do most of my analysis in Linux, being able to do this quickly from the command-line was very attractive. I was able to extract the shellcode as a binary file and with a few minutes of research found that the following one-liner did the job. I figured, this might be of interest to other analysts who haven't used radare2 much either, so here you are.
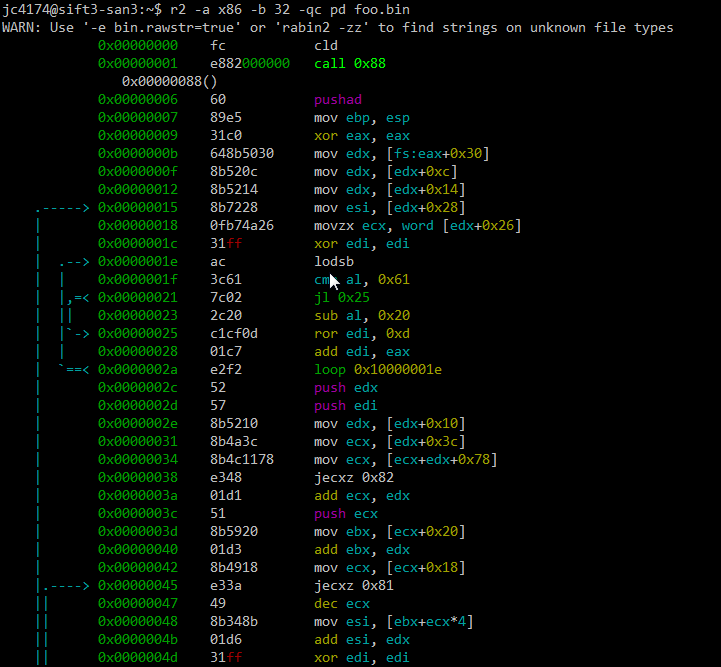
Note, the switches to the r2 command are -a x86 -b 32 because this shellcode is 32 bit x86 code, -q to just do the disassembly and quit, -c pd to print the disassembly, and, of course, the file containing the binary shellcode (foo.bin). I'm not going to spend any time here examining what the shellcode does. The purpose of this quick post was just to document one way to use radare2. If you want to learn more about how to deal with shellcode, come take FOR610 with us.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
| LINUX Incident Response and Threat Hunting | San Diego | May 11th - May 16th 2026 |


Comments