May 2021 Forensic Contest: Answers and Analysis
Introduction
Thanks to everyone who participated in the May 2021 forensic contest originally posted two weeks ago. We received 45 submissions through our contact page, and most people had all the correct answers. Unfortunately, we could only pick one winner. In this case, our winner was the first to submit the correct information. Join us in congratulating this month's winner, Pratik! Pratik will receive a Raspberry Pi 4 kit.
You can still find the pcap for our May 2021 forensic contest here.
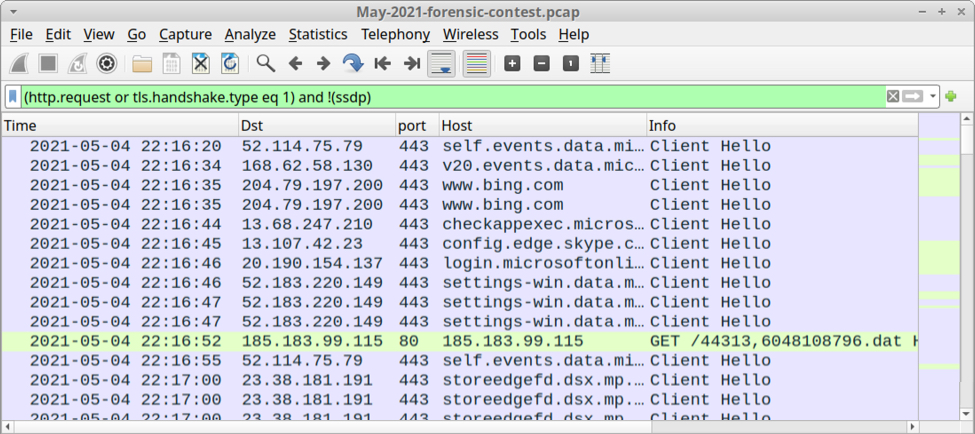
Shown above: Pcap of the infection filtered in Wireshark.
Answers
IP address of the infected Windows computer:
- 172.16.4.206
Host name of the infected Windows computer:
- DESKTOP-V0FEH1L
User account name on the infected Windows computer:
- alfonso.paternoster
Date and time the infection activity began in UTC (the GMT or Zulu timezone):
- 2021-05-04 at 22:16:52 UTC
The family or families of malware on the infected computer:
- Qakbot (Qbot)
To help in your analysis of this activity, please review the Requirements section in our original diary for this contest.
Malware from the pcap
The iniitial malware activity in the pcap is seen when the victim's host retreived a Windows EXE or DLL from 185.183.99[.]115 on 2021-05-04 at 22:16:52 UTC.
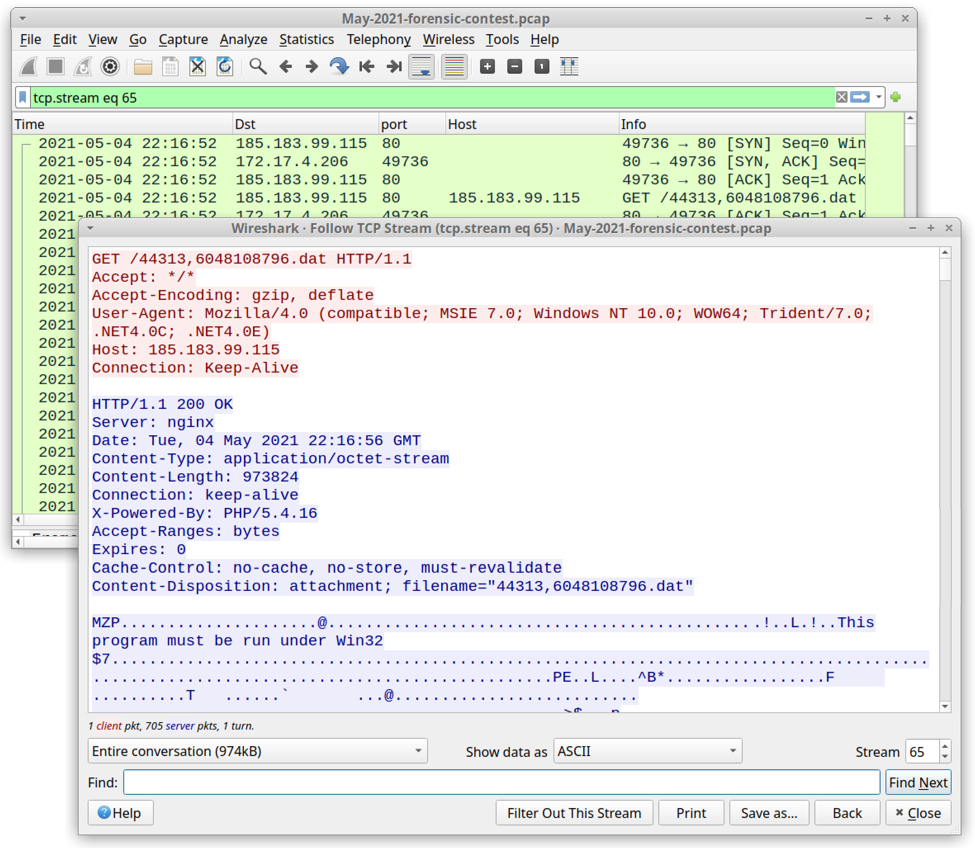
Shown above: TCP stream of traffic from 185.183.99[.]115 in the pcap.
The URL hosting this malware was reported to URLhaus, where it is tagged as Qakbot malware. The IP address is also related to some malicious Excel spreadsheets with file names that start with Outstanding-Debt- and end with 05042021.xlsm.
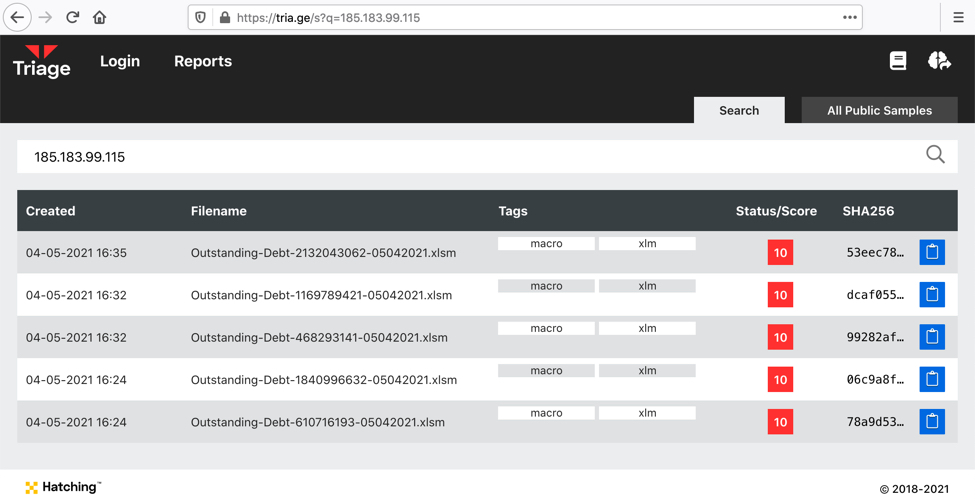
Shown above: Malicious Excel files submitted to Hatching Triage that contacted 185.183.99[.]115.
Qakbot traffic
Here's a Wireshark filter I use to review suspected Qakbot traffic:
Qakbot causes HTTPS C2 traffic directly to IP addresses, often over TCP port 443, but also using non-standard HTTPS ports like 995 or 2222. Qakbot also generates other traffic when it turns an infected Windows host into a spambot. Using the above Wireshark filter, I can quickly find the following Qakbot activity:
- Connectivity check to www.openssl.org (a legitimate site, not inherently malicious on its own)
- TCP traffic over TCP port 65400
- Connectivity/ IP address checks to api.ipifiy.org (also a legitimate site, not inherently malicious)
- Connectivity or banner checks to various email servers
- SMTP-based spambot traffic from the infected host
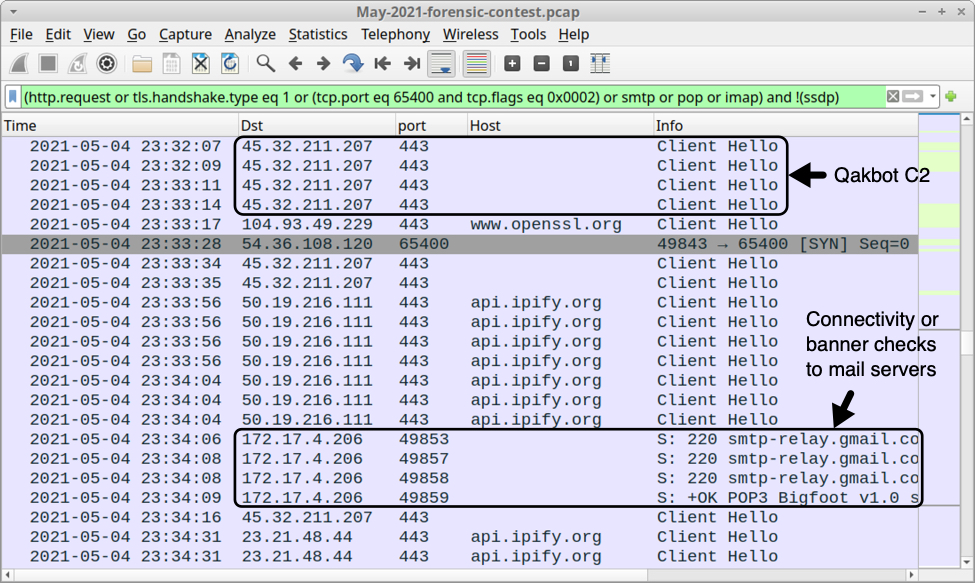
Shown above: Other Qakbot-specific traffic from the infected Windows host.
Use a basic web filter and scroll down to the end of the pcap. You should see indicators the infected host became a spambot and was contacting various email servers over TCP ports 25 and 465.
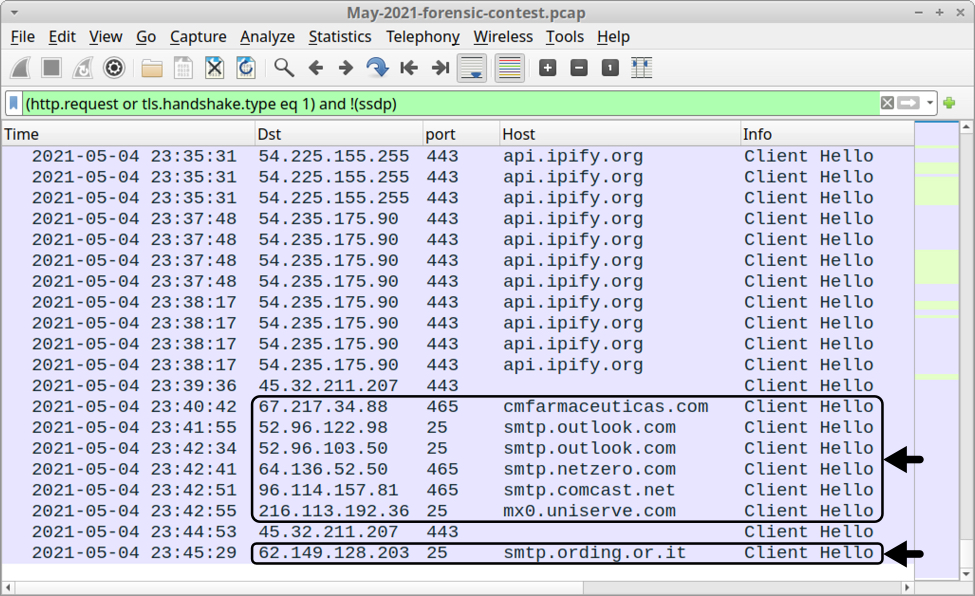
Shown above: Start of spambot traffic from our Qakbot-infected host.
Final words
Qakbot infection activity follows noticeable patterns, which we covered in today's diary. The traffic isn't much different than cases I've reported before, like this example from February 2021.
Thanks to all who participated in the May 2021 forensic contest, and congratulations again to Pratik for winning this month's competition!
You can still find the pcap here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments