Malspam with links to Word docs pushes IcedID (Bokbot)
Introduction
On Monday 2019-12-23, a wave of malicious spam (malspam) was distributing IcedID malware, also known as Bokbot. Today's diary reviews recent infection activity by this malware.
But first I'll start with a poetic satire of "A Visit from St. Nicholas" by Clement Clark Moore...
Twas the week during Christmas, when all through the net
malspam was spreading, as if on a bet.
Windows and Office were run without care
in hopes that malware would never get there.
Sysadmins weren't patching as well as they could be,
'cause IT procedures made updates untimely.
When what to our mailservers did soon appear?
Twas emails with Word docs and macros so clear!
They slipped past our mail filters as they all came,
recipients were varied, the subjects the same.
With code full of exploits and great obfuscation,
those messages made it to many workstations.
One person was foolish and opened the Word doc,
enabling macros because, why the heck not?
His laptop infected, the malware spread quickly.
Got to the DC, the server became sickly.
Provided a backdoor throughout all their networks,
with full admin rights and some privileged perks.
The criminals were happy, their eyes shining bright.
They had a great Christmas that cold winter night!
Anyway, back to the malware... As I already mentioned, today's diary reviews recent infection activity by IcedID.
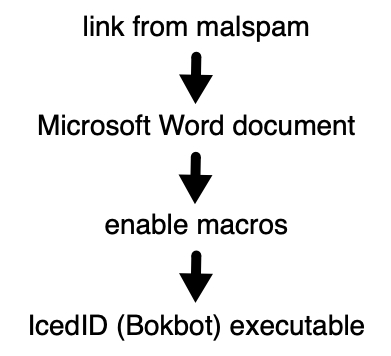
Shown above: Flow chart for recent IcedID infection activity.
The malspam
I don't have a copy of the malspam. However, an anonymous person submitted URLs that returned the associated Word docs to URLhaus. If you want to search for IcedID activity, search for items tagged as IcedID as shown here.
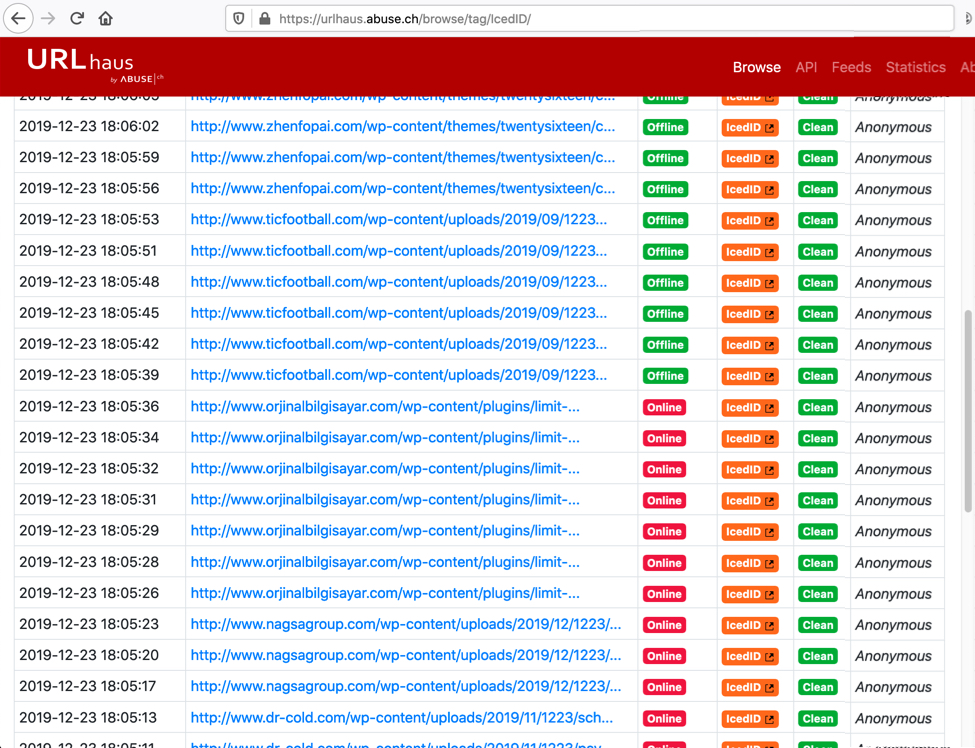
Shown above: A recent search in URLhaus for items tagged as IcedID.
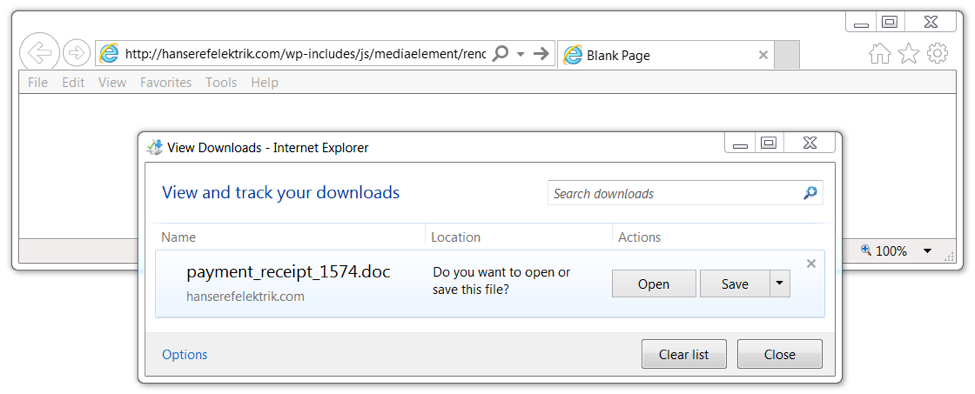
Shown above: Testing one of the URLs from URLhaus in my lab environment.
The Word documents
I received different Word docs from the same links when I tested them in my lab environment. The first Word document had a template that was mostly red (maybe reddish-orange). My second sample had a different template that was mostly blue.
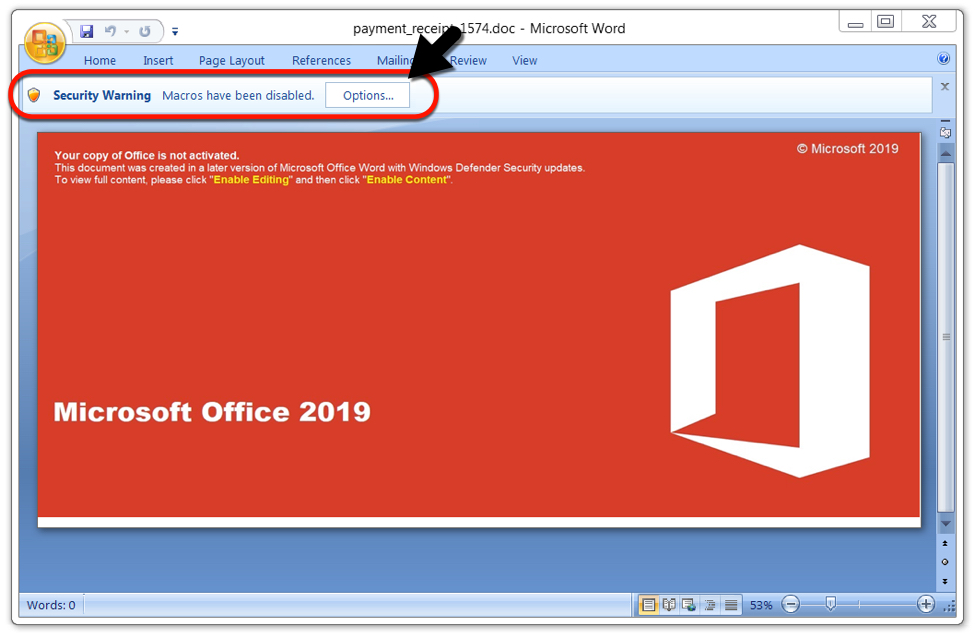
Shown above: The type of Word document returned when I tried the links earlier in the day on 2019-12-23.
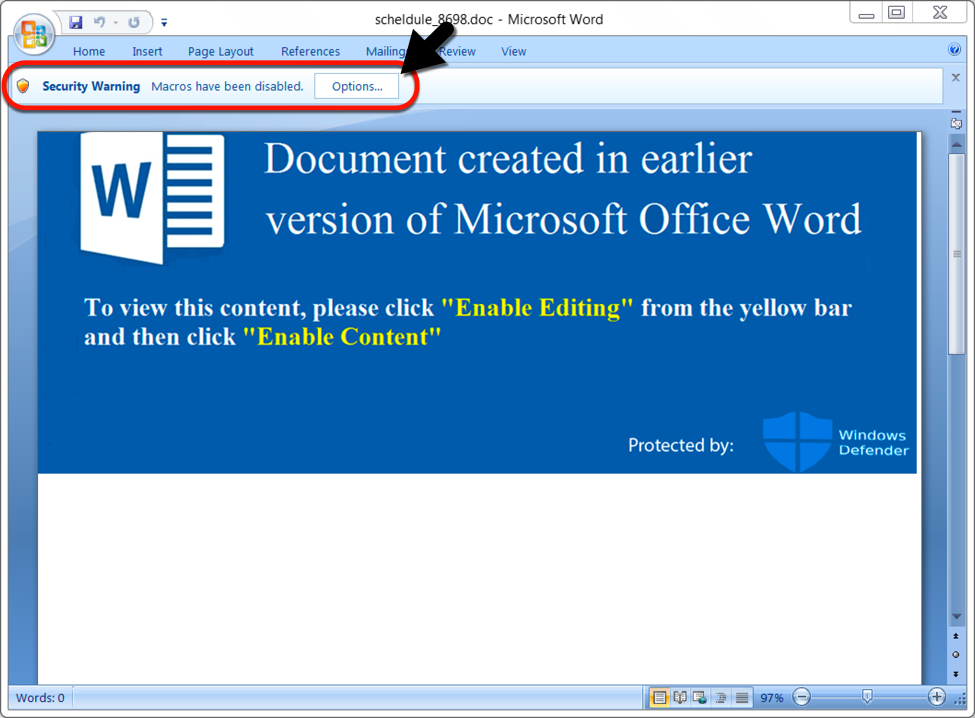
Shown above: The type of Word document when I tried these links later in the day on 2019-12-23.
The infection traffic
Infection traffic was typical for IcedID activity. In previous IcedID infections, I've seen Trickbot, such as in this previous diary from March 2019. However, no Trickbot was noted during the two infections I ran in my lab on 2019-12-23.

Shown above: Infection traffic filtered in Wireshark from my 1st run with a URL for IcedID.
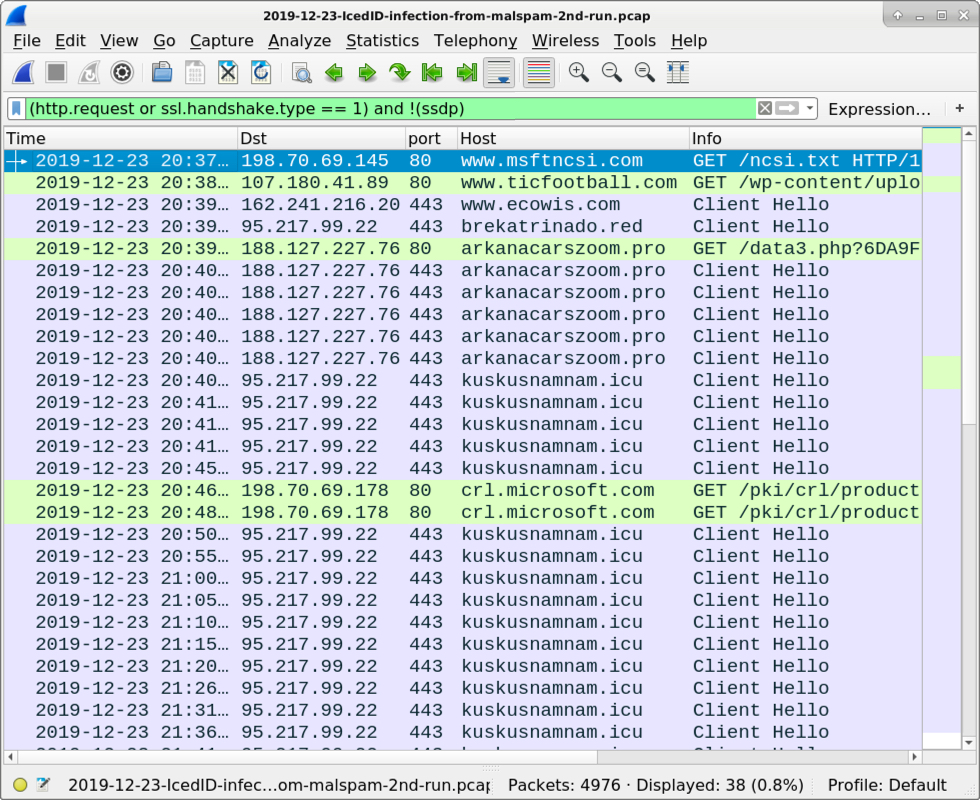
Shown above: Infection traffic filtered in Wireshark from my 2nd run with a URL for IcedID.
Forensics on an infected Windows host
My infected Windows hosts showed the same type of artifacts and behavior associated with IcedID in recent months. See the images below for examples of malware and artifacts from my 1st infection.
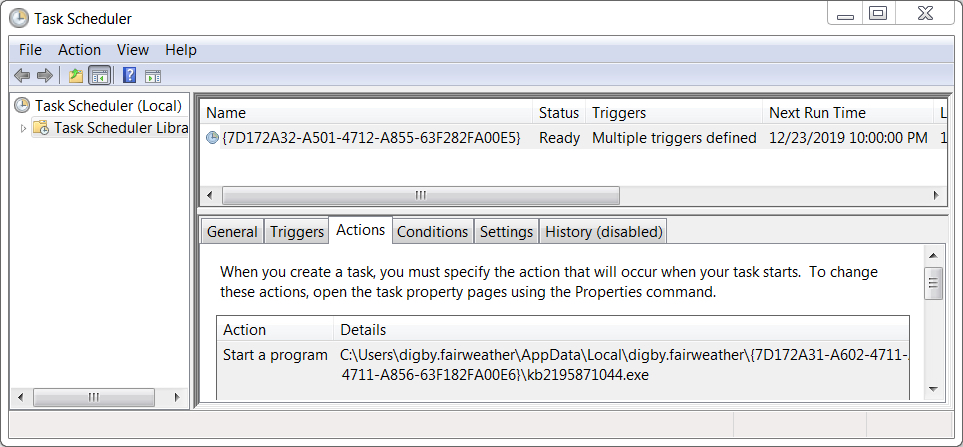
Shown above: Scheduled task to keep IcedID persistent from my 1st infection run.

Shown above: From the 1st infection run, IcedID persistent on my infected lab host.
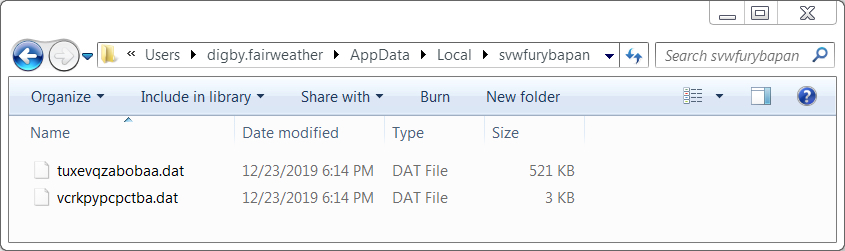
Shown above: Some data files created during the IcedID infection from my 1st run. These are random file and directory names each infection.
Indicators of Compromise (IoCs)
Infection traffic, 1st run:
- 193.36.60[.]3 port 80 - hanserefelektrik[.]com - GET /wp-includes/js/mediaelement/renderers/1223/payment_receipt_1574.doc
- 162.241.173[.]131 port 443 - fmjstorage[.]com - GET /LTCOB.KET (HTTPS traffic)
- 95.217.99[.]22 port 80 - exceptionalsanta[.]pro - GET /data3.php?0123456789ABCDEF (random hex characters)
- 188.127.227[.]76 port 443 - malayanfoodinmiami[.]pro - HTTPS/SSL/TLS traffic
- 188.127.227[.]76 port 80 - mexicanfoodinmiami[.]pro - GET /data3.php?0123456789ABCDEF (random hex characters)
- 188.127.227[.]76 port 443 - mexicanfoodinmiami[.]pro - HTTPS/SSL/TLS traffic
- 188.127.227[.]76 port 80 - russianfoodinmiami[.]pro - GET /data3.php?0123456789ABCDEF (random hex characters)
- 188.127.227[.]76 port 443 - russianfoodinmiami[.]pro - HTTPS/SSL/TLS traffic
Infection traffic, 2nd run:
- 107.180.41[.]89 port 80 - www.ticfootball[.]com - GET /wp-content/uploads/2019/09/1223/scheldule_8698.doc
- 162.241.216[.]20 port 443 - www.ecowis[.]com - GET /liteprjpohereo.exe (HTTPS traffic)
- 95.217.99[.]22 port 443 - brekatrinado[.]red - HTTPS/SSL/TLS traffic
- 188.127.227[.]76 port 80 - arkanacarszoom[.]pro - GET /data3.php?0123456789ABCDEF (random hex characters)
- 188.127.227[.]76 port 443 - arkanacarszoom[.]pro - HTTPS/SSL/TLS traffic
- 95.217.99[.]22 port 443 - kuskusnamnam[.]icu - HTTPS/SSL/TLS traffic
SHA256 hash: 240f62792a5874857d4f9d1663a97deb1eefd38f90c87eef76220d33c8440697
- File size: 146,681 bytes
- File location: hxxp://hanserefelektrik[.]com/wp-includes/js/mediaelement/renderers/1223/payment_receipt_1574.doc
- File name: payment_receipt_1574.doc
- File description: Word doc with macro for IcedID, 1st run
SHA256 hash: dcadc8a97beba4bee4608739d8efc68da37c9b7035302585eb24890a5b826755
- File size: 89,541 bytes
- File location: hxxp://www.ticfootball[.]com/wp-content/uploads/2019/09/1223/scheldule_8698.doc
- File name: scheldule_8698.doc
- File description: Word doc with macro for IcedID, 2nd run
SHA256 hash: 79723cbc2234e26aae3111b8c7b6711da68a46d01e5808598a1492e49c331f60
- File size: 102,400 bytes
- File location: hxxps://fmjstorage[.]com/LTCOB.KET
- File location: C:\Scene1\SceneWar.exe
- File location: C:\Users\digby.fairweather\AppData\Local\digby.fairweather\{7D172A31-A602-4711-A856-63F182FA00E6}\kb2195871044.exe
- File description: IcedID malware binary retrieved by Word macro, 1st run
SHA256 hash: b0430c4b64948d1fbb05ecbd7e5fc9afb068463e98718ddf01a13ddf4b4f4891
- File size: 102,400 bytes
- File location: hxxps//www.ecowis[.]com/liteprjpohereo.exe
- File location: C:\Users\suellen.covington\AppData\Local\Temp\4v75i0n9c.exe
- File location: C:\ProgramData\ñûâôÛÖÉôÎÃøíÀÌñÂ.exe
- File location: C:\Users\suellen.covington\AppData\Local\suellen.covington\{92508AEB-DC02-46CB-B469-C32B6DA9A09C}\kb1839855098.exe
- File description: IcedID malware binary retrieved by Word macro, 2nd run
Final words
Pcaps and malware samples used for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments