Gift Card Scams on the rise
Most people are very helpful and try to be good neighbors and citizens. This is even more prevalent with the holiday season. There are those who take advantage of the season and people's helpfulness in order to scam them out of money. One that is hitting right now, with a very targeted approach, are gift card scams. These have not just occurred during the holidays, but there are more reports of them occurring during the season of giving. The flow of the scam is generally the same for most of these that are being reported. An individual is targeted by someone purporting to be their management from higher up in the chain of command. The request is usually via email with a urgent demand for the purchase of gift cards to give to clients. The attacker has done their research to learn the personnel that work in the particular office. Here is an example of one of the scams that was submitted to us by Keegan Mills. The names have been changed/obfuscated in the incident.
Background information: "Spoofed_Pres" is the president/CEO of the company. Her contact information is widely distributed. The initial target, "Target_One", was very new to the company in a junior position. According to Keegan: "We were a bit surprised the actors even found her as a contact." Due to the number of emails exchanged (over 30) in the attempt to fulfil this request, I am only showing a few of the key one's here in the thread.
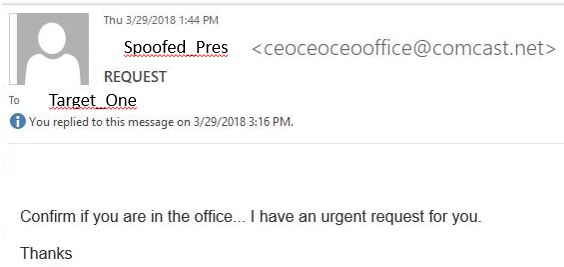
The first contact came as an urgent request from the CEO to see if "Target_One" was in the office. The name that appeared was the correct name of the CEO, but it was not the correct email address:
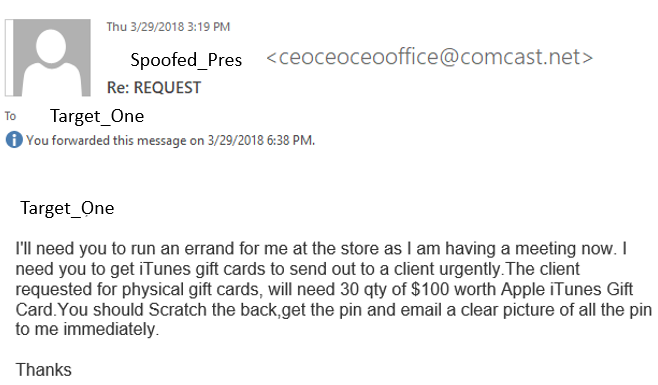
Once Target_One responded that they were in the office, the directions followed:
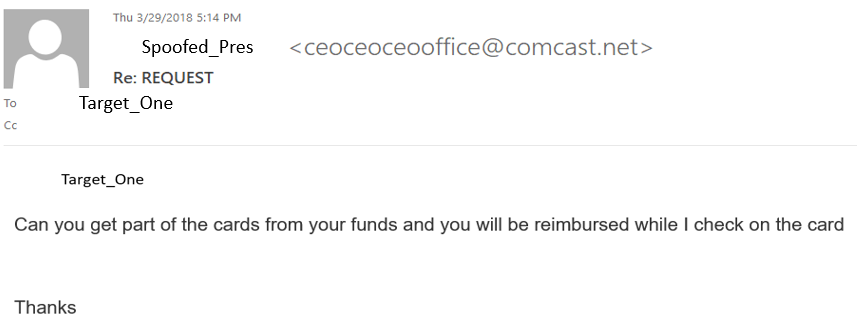
Target_One contacted the correct POC at the company to get the company card and help was enlisted from two other people (at one point three others) in order to fulfil the request for the urgent gift cards. However, there was an issue with the credit card not working at the store. At this point, Target_One is instructed to use their own funds to buy the cards and they will be reimbursed.
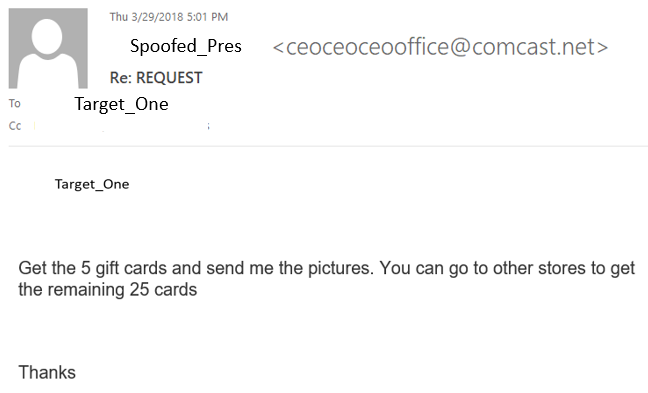
Also, as soon as they were able to get the gift cards, they should send a picture of the PIN immendiately. This was a reoccuring theme through the email exchange. They could not get that many cards from a single location, so they were attempting multiple stores. Also, commute to get to stores factors into the time this scenario plays out.
This entire effort last for about five hours when it was finally realized that it was not a legitmate email from the CEO/President. I don't know if any gift cards were actually purchased, however, think about the time lost and cost salary wise: five hours of salary for three people at a minimum! Then there is the time to work the incident and do any mitigation afterwards.
We received several examples of these and the verbiage is not verbatim between them. Here is another example of one (Thank you Brad Theodore):
I am including this exchange for you read on your own if you wish. Its another example of the gift card attempts (thank you Chris Rovers) and a user who had a conversation with the scammer, before questioning if they should really be doing this: https://isc.sans.edu/diaryimages/files/GiftCardPhish_Anonymized.txt
Before you think this could never happen in your company, be careful! This was a targeted attack, not just a phishing attempt. A new employee gets an urgent email from a superior that asks them for help immediately. They will jump through hoops to help!! Especially if the superior is in a meeting and needs it ASAP. The attackers are taking the time to do their research and change their tactics. We need to make sure we are taking the time to really train our employees as well.




Comments
Anonymous
Jan 4th 2019
6 years ago