Fake Adobe Flash Update OS X Malware
Yesterday, while investigating some Facebook click-bait, I came across a fake Flash update that is targeting OS X users. Fake flash updates have been very common to infect OS X. They do not rely on a vulnerability in the operating system. Instead, the user is asked to willingly install them, by making them look like genuine Adobe Flash warnings (and we keep telling users to make sure Flash is up to date, so they are likely going to obey the warning and install the update).
The "Installer" for the fake Flash update will install various scare ware (I observed a couple different varieties when re-running the installer), and it actually installs an up to date genuine version of Flash as well.
While I wasn't able to capture the exact trigger for the popup advertising the update, I suspect it was injected by one of the many ads on the page:
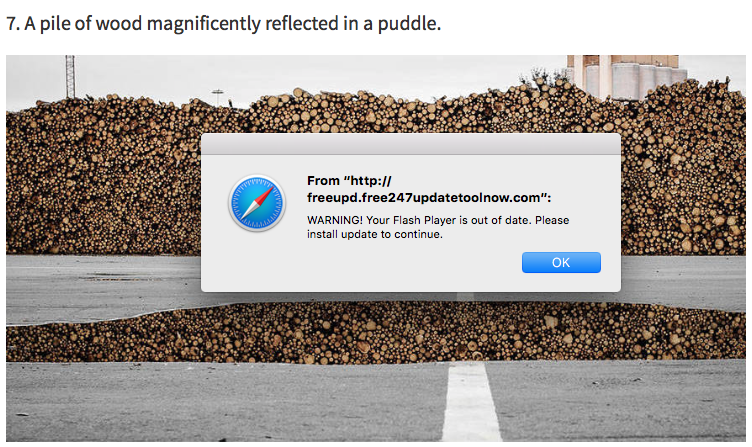
Once the user clicks on the popup, the following page offers the Flash Player update for download:
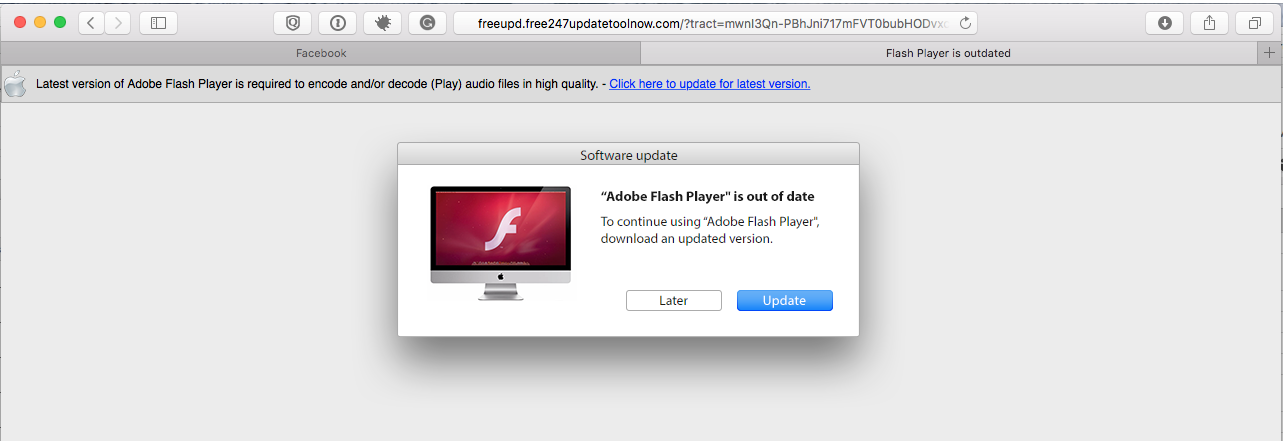
Antivirus coverage was pretty bad yesterday when I came across this (4 out of 51 on Virustotal). On a brand new OS X 10.11 install, the "Installer" appears to install a genuine copy of Adobe Flash in addition to Scareware that asks for money after informing you of various system problems.
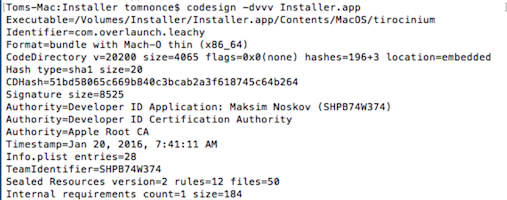
The installer is signed with a valid Apple developer certificate issued to a Maksim Noskov:
I recorded a small video showing what happens when you install the "update" on a clean OS X 10.11 system:
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
Feb 4th 2016
1 decade ago
Anonymous
Feb 5th 2016
1 decade ago
Anonymous
Feb 5th 2016
1 decade ago
Anonymous
Feb 5th 2016
1 decade ago
Anonymous
Feb 6th 2016
1 decade ago
The application was signed by “Apple Root CA”, “Developer ID Application: Maksim Noskov (SHPB74W374)”.
Both the verified timestamp and the signing-time are: Jan 20, 2016, 5:41:11 AM.
The object code format is “app bundle with Mach-O thin (x86_64)”.
The signature contains the Team ID “SHPB74W374”.
Both bundle and signing identifiers are “com.overlaunch.leachy”.
The signature specifies implicit requirements. 
The requirements specify the Team ID “SHPB74W374”.
This matches the Team ID contained in the signature.
The signature specifies resource rules (v1). 
The signature specifies resource rules (v2). 
Gatekeeper assessment: FAIL (damaged).  
damaged = "/Volumes/Installer/Installer.app/: CSSMERR_TP_CERT_REVOKED"
Anonymous
Feb 8th 2016
1 decade ago
https://objective-see.com/blog/blog_0x0C.html
Anonymous
Feb 12th 2016
1 decade ago