Adwind: another payload for botnet-based malspam
Updated 2015-08-18 to include information on AlienSpy transitioning to JSocket v1.0.
Introduction
Since mid-July 2015, I've noticed an increase in malicious spam (malspam) caught by my employer's spam filters with java archive (.jar file) attachments. These .jar files are most often identified as Adwind. Adwind is a Java-based remote access tool (RAT) used by malware authors to infect computers with backdoor access. There's no vulnerability involved. To infect a Windows computer, the user has to execute the malware by double-clicking on the .jar file. Of course, you have to have the Java Runtime Environment installed, which many people do.
I previously associated Adwind with targeted phishing attempts in limited amounts. I had found very few examples of non-targeted malspam using this RAT.
However, we're currently seeing enough Adwind-based malspam to ask: Is Adwind now another payload for botnet-based malspam?
Background
Adwind originated from the Frutas RAT [1]. Frutas was a Java-based RAT discovered by Symantec from underground forums in early 2013 [2]. By the summer of 2013, the name had changed to Adwind, and signatures for Adwind-based malware were implemented by anti-virus companies [3]. In November of 2013, Adwind was rebranded and sold under a new name: UNRECOM (UNiversal REmote COntrol Multi-platform) [1].
Throughout 2013, we noticed a few occasions of Adwind used in phishing attempts. 2014 saw an increase of Adwind/UNRECOM malware used in phishing campaigns targeting "U.S. state and local government, technology, advisory services, health, and financial sectors" [4].
By April 2015, a new Adwind/UNCRECOM variant called AlienSpy was widely reported, and this new variant included Transport Layer Security (TLS) encryption for command-and-control communications. These TLS communications involve certificates. EmergingThreats posted a signature for Adwind-based certificates in March of 2015 [5], and Fidelis CyberSecurity Solutions published an in-depth report on AlienSpy the following month [6].
Recent updates
- 2015-04-10: AlienSpy domain suspended by Godaddy shortly after a report on this RAT was published by Fidelis [7].
- 2015-04-19: JSocket.org registered through eNom.
- 2015-06-23: JSocket.org's first blog entry stating the project started on 2015-06-23 [8].
- 2015-07-10: Another entry (now removed) states AlienSpy would stop on 2015-07-11, telling AlienSpy users to update to JSocket.
- As recently as 2015-08-18, a site called Rekings currently shows its AlienSpy entry tagged as JSocket v1.0 [9].
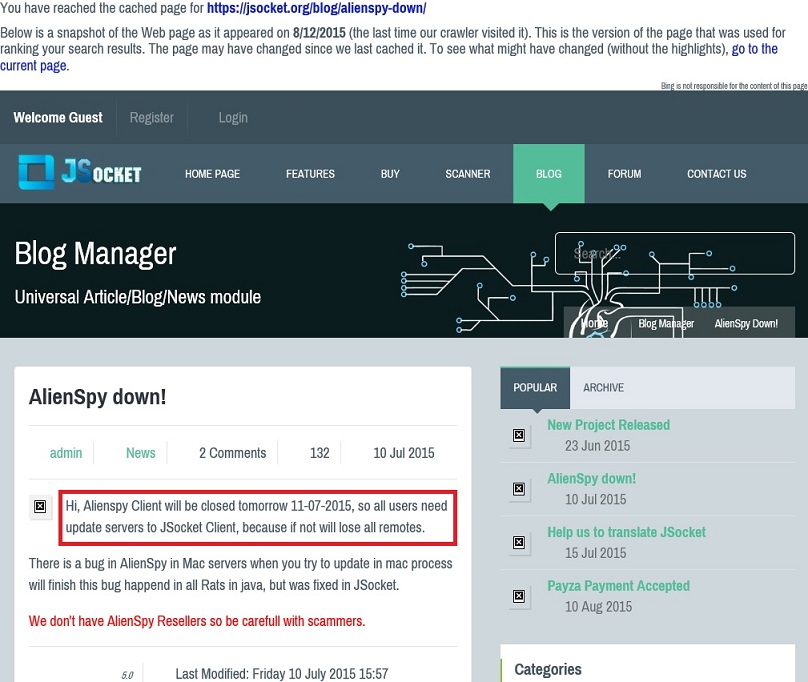
Shown above: Blog entry showing AlienSpy transitioned to JSocket on 2015-07-11.
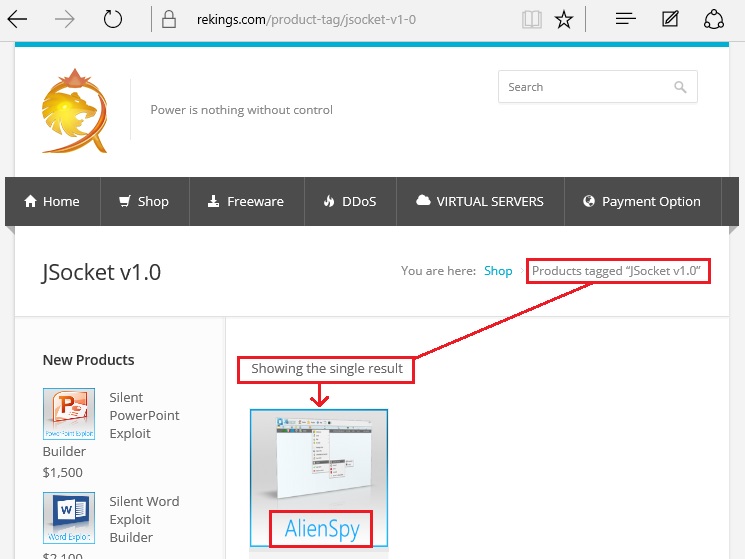
Shown above: At least one reseller has tagged AlienSpy as JSocket v1.0.
The naming progression appears to be: Frutas -> Adwind -> UNRECOM -> AlienSpy -> JSocket. From what I can tell, it's all been Java-based malware sent as .jar file attachments in phishing emails. Many people still refer to it as Adwind, which is how I see it identified most often.
Not counting targeted attempts, I've found Adwind-based malspam maybe once every month or two. That changed in mid-July 2015. After that, the amount of malspam with Adwind increased dramatically. Currently, I see at least one Adwind-based malspam every day on average. The frequency of this malspam along with the variety of subject lines, attachment names, and senders indicate Adwind is no longer limited to targeted attacks. Frutas/Adwind/UNRECOM/AlienSpy/JSocket (whatever you want to call it) appears to be another payload for botnet-based malspam.
The emails
Here's a sample of the different senders, subjects, and attachment names I've seen for Adwind-based malspam since mid-July 2015:
Read: Date -- Sender (most often spoofed) -- Subject -- Attachment name(s)
- 2015-07-14 -- Credit Control [creditcontrol@bwfllc.co] -- Chaps Payement -- Chaps Payment Copy.jar
- 2015-07-17 -- Kathryn Harriman [williamhui@bgf.com.hk] -- Re: New Order -- product list.jar
- 2015-07-25 -- Karianne Maltun [geral@eimigrante.pt] -- RE :Payment Preparation=0590-PI/Invoice -- payment_Order .jar
- 2015-07-27 -- Vivian Joe [noreply@googlemail.com] -- Purchasing order -- PURCHASING Order.jar
- 2015-07-29 -- NAB Customer Service [trusplus@sify.com] -- PAYMENT ADVICE -- PAYMENT SWIFT MT103 NAB BANK PDF.jar
- 2015-07-30 -- sales.qnijewels@gmail.com -- Fwd: Outstanding Invoices -- SOA AS OF JUly.jar
- 2015-07-30 -- Karianne Maltun [a.macesic@inspectorate-croatia.hr] -- Scanned DUC-Invoice -- Invoice.jar
- 2015-07-31 -- [Andrea@intl.westernunion.com] -- Wupos Update -- Wupos_update_0940002TT12212.jar
- 2015-07-31 -- [office@regcon-asia.kz] -- Find the swift copy for the balance payment !! -- payment.invoice.1.jar
- 2015-08-03 -- Juliet Helix [noreply@googlemail.com] -- Purchasing Order -- Purchasing Order..jar
- 2015-08-03 -- Wilborax Trading Company Ltd. [top@jviincentthailand.com] -- Re: PO 6785435 30-08-2015 -- PO 6785435 30-08-2015 PDF.jar
- 2015-08-06 -- Eduardo A. Iguina [info@al-rddadi.com.sa] -- Re: Payment Processed. -- PI-Invoice-0972-DUC.jar
- 2015-08-06 -- Sales!!! UST-TRADE Co,. Ltd [sales11@laurence-chocolate.gr] -- Re: Enquiry -- P.O_001_UST-TRADE.jar
- 2015-08-06 -- Lynnea Trade Co,. LTD [vinita.sharma@frrforex.in] -- Re: P.0 18003. -- P.O_18003.jar
- 2015-08-09 -- Eduardo A. Iguina [d.pavic@inspectorate-croatia.hr] -- Re: Payment Processed -- Invoice-Processed.jar
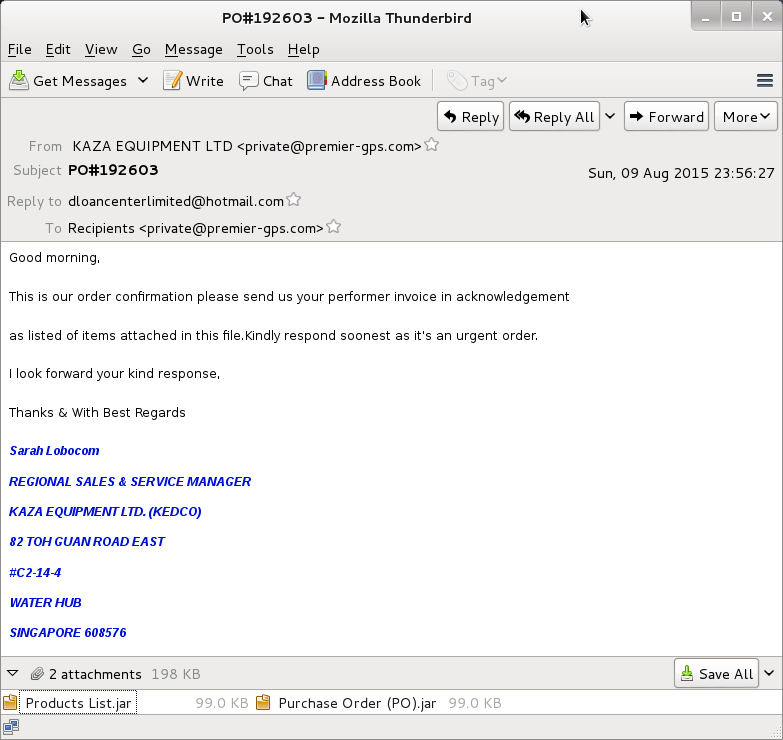
- 2015-08-09 -- KAZA EQUIPMENT LTD [private@premier-gps.com] -- PO#192603 -- Products List.jar , Purchase Order (PO).jar
- 2015-08-10 -- [info@fulplanet.com] -- Invoice order -- Invoice.jar
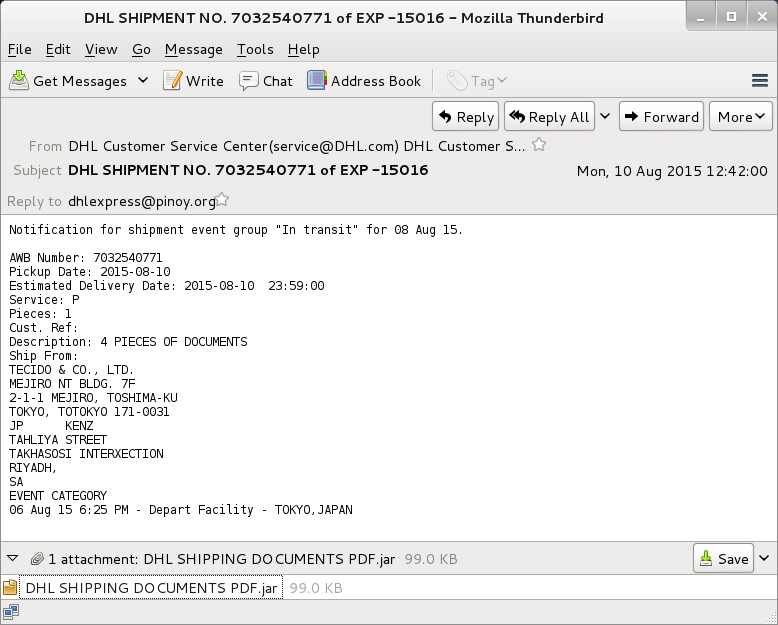
- 2015-08-10 -- DHL Customer Service [trusplus@sify.com] -- DHL SHIPMENT NO. 7032540771 of EXP -15016 -- DHL SHIPPING DOCUMENTS PDF.jar
- 2015-08-10 -- Ditana Amir Cohen [Elvgncl@gmail.com] -- Request Quotation for Listed Item -- Request Quotation Item.jar
- 2015-08-11 -- Florence Walton [fax@chartered.co.th] -- Winter Order to Brazil. -- Price Check.jar
- 2015-08-12 -- [info@fulplanet.com] -- Re: Invoices payable -- Invoice.jar
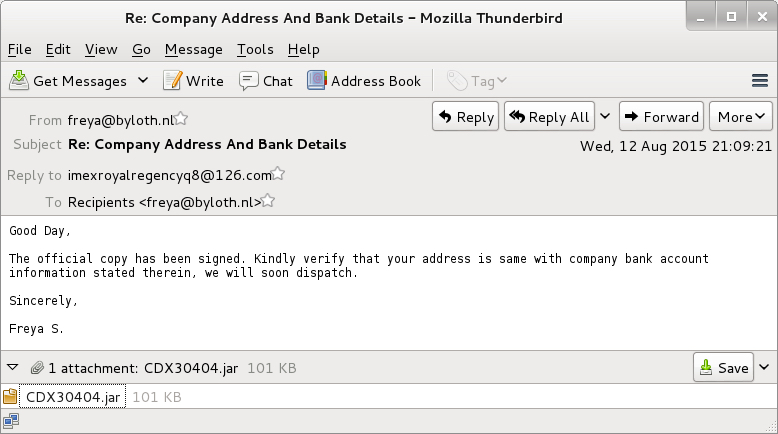
- 2015-08-12 -- [freya@byloth.nl] -- Re: Company Address And Bank Detail -- CDX30404.jar
- 2015-08-13 -- Sandy [private@premier-gps.com] -- PO#192603 -- PO#192603.jar
Prior to that, I saw Adwind-based malware maybe once every month or two. I never paid much attention to it until I noticed the recent increase. Some screenshots are shown below:
The malware
I collected some samples during the past week and examined them. With the appropriate software packages installed, I could use the command jar tf [filename] to list the contents of the Java archive. Most (but not all) of the .jar files had this internal file structure:
- META-INF/MANIFEST.MF
- b.txt
- a.txt
- a/dewmhGAv5r0QGW5ll9yAZViufg7Kw96lY5dWkbn4Eq8ZBiNW8azEnBVN7TqbhwMvgiKJW1D3lw9muhhJ2jxGQYjlwiiIiiIIIii.class
- b/dewmhGAv5r0QGW5ll9yAZViufg7Kw96lY5dWkbn4Eq8ZBiNW8azEnBVN7TqbhwMvgiKJW1D3lw9muhhJ2jxGQYjlwiiIiiIIIii.class
- c/dewmhGAv5r0QGW5ll9yAZViufg7Kw96lY5dWkbn4Eq8ZBiNW8azEnBVN7TqbhwMvgiKJW1D3lw9muhhJ2jxGQYjlwiiIiiIIIii.class
- dewmhGAv5r0QGW5ll9yAZViufg7Kw96lY5dWkbn4Eq8ZBiNW8azEnBVN7TqbhwMvgiKJW1D3lw9muhhJ2jxGQYjlwiiIiiIIIii.class
- Main.class
- dewmhGAv5r0QGW5ll9yAZViufg7Kw96lY5dWkbn4Eq8ZBiNW8azEnBVN7TqbhwMvgiKJW1D3lw9muhhJ2jxGQYjlwIiiiiiIiII.class
- dewmhGAv5r0QGW5ll9yAZViufg7Kw96lY5dWkbn4Eq8ZBiNW8azEnBVN7TqbhwMvgiKJW1D3lw9muhhJ2jxGQYjlwIIiiIiiiII.class
- dewmhGAv5r0QGW5ll9yAZViufg7Kw96lY5dWkbn4Eq8ZBiNW8azEnBVN7TqbhwMvgiKJW1D3lw9muhhJ2jxGQYjlwIiiiiIiIII.class
- dewmhGAv5r0QGW5ll9yAZViufg7Kw96lY5dWkbn4Eq8ZBiNW8azEnBVN7TqbhwMvgiKJW1D3lw9muhhJ2jxGQYjlwIIIiIiIiIi.class
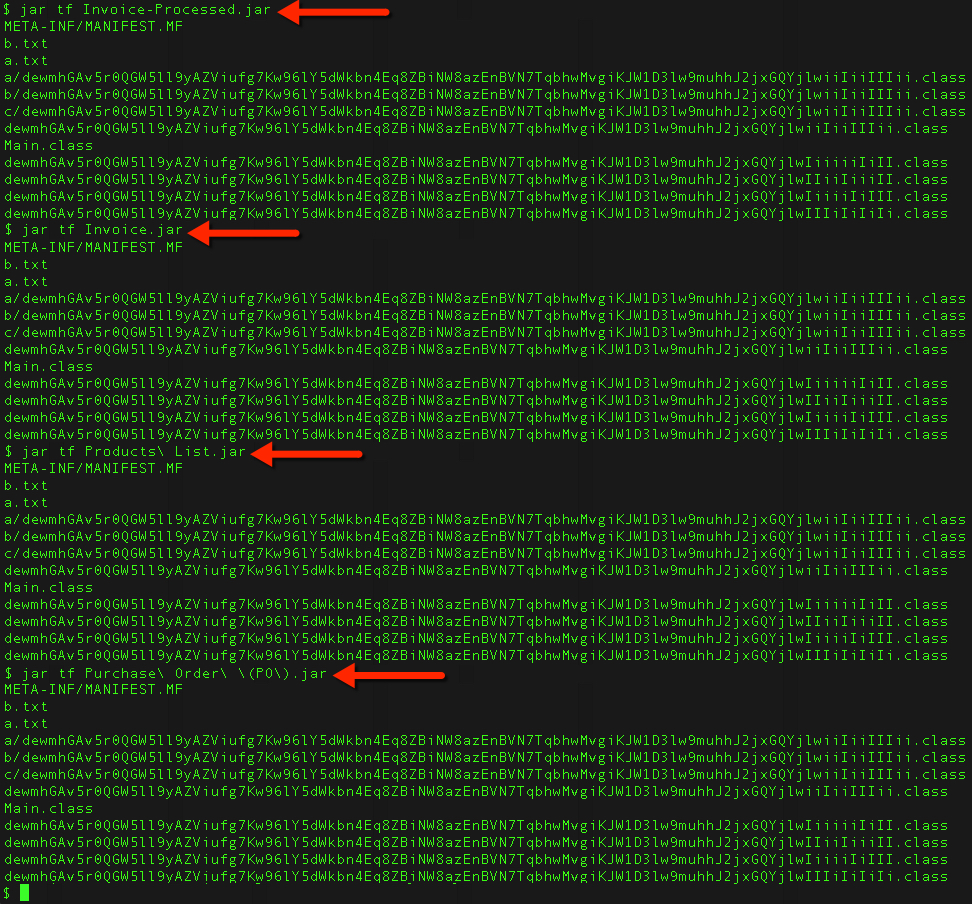
Shown above: Listing some of the Adwind .jar files' contents
Command and control communications
Samples collected during the past week show the following TLS-encrypted SSL traffic after the infection:
Read: host name - IP address - port
- p0.corotext.com - 91.236.116.185 - TCP port 588
- pauloo1.corotext.com - 91.236.116.185 - TCP Port 8001
- trusplus111.gotdns.ch - 197.255.170.191 - TCP port 10000
- selkrom.ddns.net - 111.118.183.211 - TCP port 9887
- serialcheck55.serveblog.net - 185.19.85.172 TCP port 1818
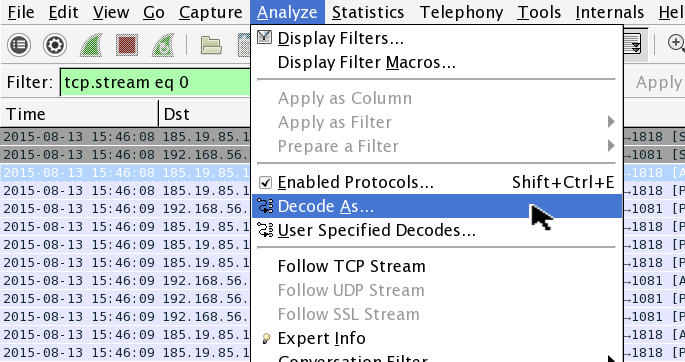
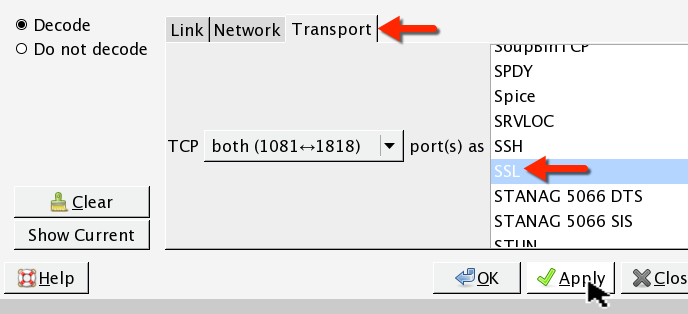
I examined a pcap from the last malware sample above, with command-and-control traffic on TCP port 1818. You can find the certificate associated with Adwind in Wireshark. First, follow a TCP stream with the traffic on port 1818. From the Wireshark menu, select: Analyze -> Decode As.
In the window that pops up, select the Transport tab and scroll down to SSL, then apply.
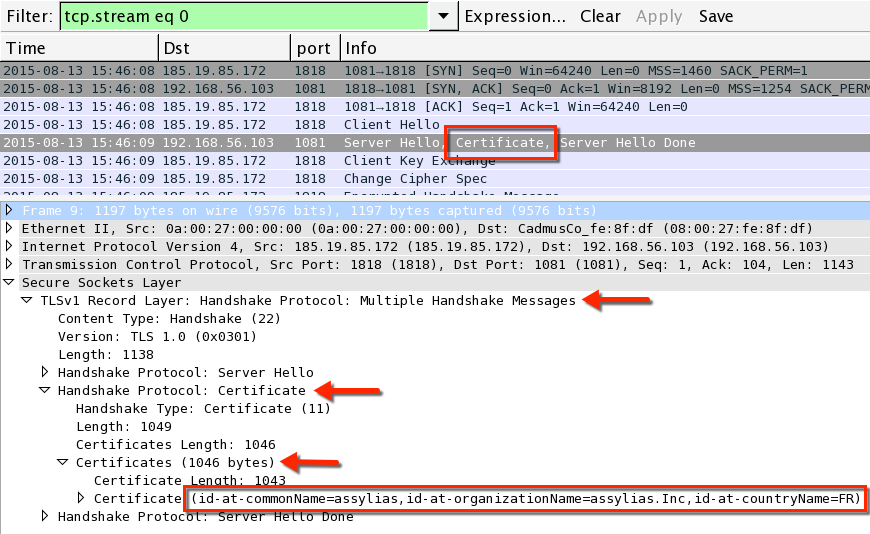
Wireshark will now parse this TCP stream as SSL. You can find the certificate information as shown in the image below:
This still shows the same certificate information used since EmergingThreats tagged it in their snort signature from March 2015 [5]. I saw the same certificate information used last week [10], and it continues this week.
- commonName = assylias
- organizationName = assylias.Inc
- countryName = FR
Currently, this may be the best way to identify Adwind-based post-infection traffic. Look for SSL traffic on a non-standard TCP port using that particular certificate.
Malware samples
Below, I've included information on examples for Adwind malware found during the past week:
File name: Invoice-Processed.jar
- File size 96.5 KB ( 98,866 bytes )
- MD5 hash: d93dd17a9adf84ca2839708d603d3bd6
- SHA1 hash: ddca2db7b7ac42d8a4a23c2e8ed85de5e91dbf29
- SHA256 hash: d5d3d46881d8061bb3679aee67715f38bebefb6251eb3fdfa4a58596db8f5b16
- Detection ratio: 8 / 50
- First submission: 2015-08-09 08:27:37 UTC
- Virus Total link - Malwr link - Hybrid-Analysis link
- Command and control: p0.corotext.com - 91.236.116.185 - TCP port 588
File name: Products List.jar
- File size: 99.0 KB ( 101,349 bytes )
- MD5 hash: 201fd695feba07408569f608cd639465
- SHA1 hash: b11857de46ba3365af5f46171bbe126f19483fee
- SHA256 hash: 0e198e6e1b9cfa5be0d9829e10717093487548b5c0d6fbbeaae6be1d53691098
- Detection ratio: 8 / 56
- First submission: 2015-08-10 19:42:56 UTC
- Virus Total link - Malwr link - Hybrid-Analysis link
File name: Purchase Order (PO).jar
- File size: 99.0 KB ( 101,344 bytes )
- MD5 hash: 78990750a764dce7a7a539fb797298a1
- SHA1 hash: af35dc7c1e4a32d53fe41e2debc73a82cc1f52bd
- SHA256 hash: 9eeeb3b6be01ad321c5036e6c2c8c78244b016bf7900b6fd3251139149dae059
- Detection ratio: 8 / 56
- First submission: 2015-08-10 19:43:20 UTC
- Virus Total link - Malwr link - Hybrid-Analysis link
File name: Invoice.jar
- File size: 96.6 KB ( 98,903 bytes )
- MD5 hash: da9f9b69950a64527329887f8168f0b4
- SHA1 hash: 752fab5861093e7171463b0b945e534e1ff66253
- SHA256 hash: 70290f0ffffcb4f8d90bce59f16105fd5ff61866e3dda5545b122b3c4098051b
- Detection ratio: 10 / 56
- First submission: 2015-08-10 06:40:09 UTC
- VirusTotal link - Malwr link - Hybrid-Analysis link
- Command and control: pauloo1.corotext.com - 91.236.116.185 - TCP Port 8001
File name: DHL SHIPPING DOCUMENTS PDF.jar
- File size: 99.0 KB ( 101,342 bytes )
- MD5 hash: 1fb2b0742e448124c000c34912765634
- SHA1 hash: 29d5d03dab95cd5d38bd691d5559202816d36417
- SHA256 hash: ff2b35d58d2e1ade904187eeffba709c84a9a998c6323b22fc5b7cac74cd1293
- Detection ratio: 25 / 56
- First submission: 2015-08-10 10:12:16 UTC
- VirusTotal Link - Malwr link - Hybrid-Analysis link
- Command and control: trusplus111.gotdns.ch - 197.255.170.191 - TCP port 10000
File name: Request Quotation Item.jar
- File size: 99.0 KB ( 101,370 bytes )
- MD5 hash: e08b81fd1b1b409096e65011e96ac62b
- SHA1 hash: 0fa5ce77ba5df13c596824681402c3ece7b5c1e8
- SHA256 hash: 771bb9fe6db1453e3de20ba7c39b8502c1249c6fcfd0022031ab767636136e7a
- Detection ratio: 26 / 56
- First submission: 2015-08-10 19:09:04 UTC
- VirusTotal link - Malwr link - Hybrid-Analysis link
- Command and control: selkrom.ddns.net - 111.118.183.211 - TCP port 9887
File name: Price Check.jar
- File size: 99.0 KB ( 101,359 bytes )
- MD5 hash: 5190bde4532248eb133f4dae044c492a
- SHA1 hash: 54484c3a466fb8efb982520a714045d218c83dcf
- SHA256 hash: d54e97bc1204f3674572d60e17db04c11bbe018ba9ab0250bd881cbcc5a9622e
- Detection ratio: 25 / 56
- First submission: 2015-08-11 15:57:22 UTC
- VirusTotal link - Malwr link - Hybrid-Analysis link
File name: Invoice.jar
- File size: 93.2 KB ( 95,455 bytes )
- MD5 hash: 0df04436cce61f791ec7da24ab34d71b
- SHA1 hash: 75fa848e0048e040aed231f9db45b14bf1a903d7
- SHA256 hash: f2188d223305092fe0a9c8be89c69e149c33c3ea4b1c0843fda00771ac72272d
- Detection ratio: 10 / 55
- First submission: 2015-08-12 19:53:46 UTC
- VirusTotal link - Malwr link - Hybrid-Analysis link
File name: CDX30404.jar
- File size: 100.6 KB ( 102,970 bytes )
- MD5 hash: 5ab9653be58e63bf8df7fb9bd74fa636
- SHA1 hash: 3af9157dffde41f673cdacc295f2887b5c56e357
- SHA256 hash: f8f99b405c932adb0f8eb147233bfef1cf3547988be4d27efd1d6b05a8817d46
- Detection ratio: 22 / 49
- First submission: 2015-08-09 20:57:26 UTC
- VirusTotal link - Malwr link - Hybrid-Analysis link
- Command and control: serialcheck55.serveblog.net - 185.19.85.172 TCP port 1818
File name: PO#192603.jar
- File size: 95.6 KB ( 97,918 bytes )
- MD5 hash: c5cdbf91ebd4bab736504415806a96b7
- SHA1 hash: ceb29d24f0dc96d867c9a99306d155a31c5eb807
- SHA256 hash: 48a0859478fb2b659e527ed06abf44ef40d84c37a5117d49ca2312feed1b1b7d
- Detection ratio: 13 / 56
- First submission: 2015-08-13 17:21:33 UTC
- VirusTotal link - Malwr link - Hybrid-Analysis link
Final words
I collected some emails from the past few days, sanitized them, and saved them to a zip archive. That archive is available at:
The zip archive is password-protected with the standard password. If you don't know it, email admin@malware-traffic-analysis.net and ask.
This malspam might all be from the same botnet, but I haven't had time to dig through the malware samples to confirm. Furthermore, my view is limited to whatever I collect from the spam filters at my current employer. I suspect other organizations with access to more data have better insight.
If any of you have encountered examples of this malspam, feel free to share in the comments.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://blog.crowdstrike.com/adwind-rat-rebranding/
[2] http://www.symantec.com/connect/blogs/cross-platform-frutas-rat-builder-and-back-door
[3] https://www.symantec.com/security_response/writeup.jsp?docid=2013-070113-1904-99
[4] http://www.fidelissecurity.com/sites/default/files/FTA_1013_RAT_in_a_jar.pdf
[5] http://doc.emergingthreats.net/bin/view/Main/2020728
[6] http://www.fidelissecurity.com/sites/default/files/FTA_1015_Alienspy_FINAL.pdf
[7] http://www.threatgeek.com/2015/04/tango-down-alienspy-is-offline-as-of-this-morning.html
[8] https://jsocket.org/blog/new-project/
[9] https://www.rekings.com/product-tag/jsocket-v1-0/
[10] http://malware-traffic-analysis.net/2015/08/06/index.html

Comments
| malware by double-clicking on the .jar file.
Really?
Standard installations of Windows dont have an association for .JAR files!
Anonymous
Aug 14th 2015
8 years ago
Anonymous
Aug 14th 2015
8 years ago
If not then (consider to) enable Software Restriction Policies a.k.a. SAFER to deny execution in %USERPROFILE% and add .JAR as "executable" extension, or restrict the JRE to run only (properly) signed .JAR files.
Anonymous
Aug 15th 2015
8 years ago
Running it on a test machine using Java 1.8 gives a pop up warning saying 1.8 found, needs 1.7
Provided a user has the latest Version of Java installed the current risk form these is vastly lessened.
We have been seeing these create an Image File Execution Options to block most common anti-virus products form running
Anonymous
Aug 19th 2015
8 years ago