Who is Probing the Internet for Research Purposes?
Shodan[1] is one of the most familiar site for research on what is on the internet. In Oct 2020 I did a diary on Censys [2][3], another site collecting similar information like Shodan. The next two sites are regularly scanning the internet for data which isn't shared with the security community at large.
Net Systems Research [4] probe the internet for research, but none of the data is accesible or published on the site. This is part of the message About Us: "Net Systems Research was founded in 2015 by a group of security data researchers who wanted to utilize a global view of the internet to study these difficult and emerging internet security challenges and understand the resulting implications."
Security IPIP [5] has no information beside a banner: "Our company engaged in the researching and data collecting of IP location, internet infrastructure and network security, we need to detect the internet (Ping/ Traceoute Mainly); For network security research, we need to obtain the IP location Banner and fingerprint information, we detecting the common port openly or not by ZMap, and collecting opened Banner data by our own code. Any questions please do not hesitate to contact with us: [email protected]."
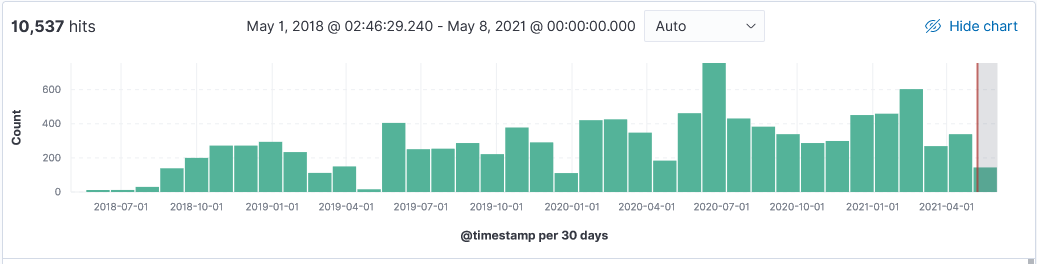
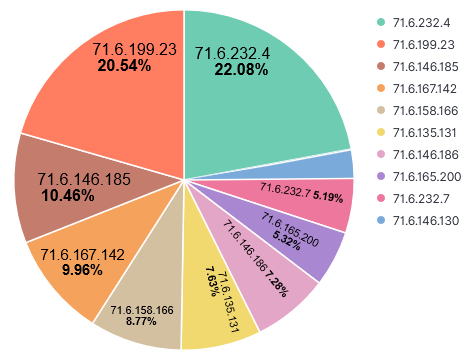
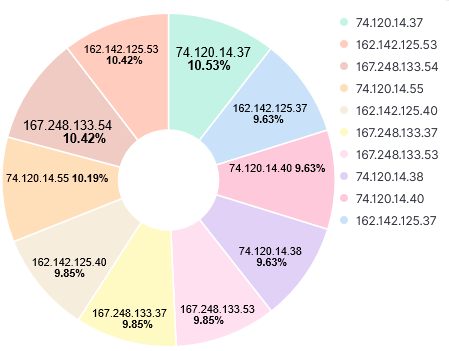
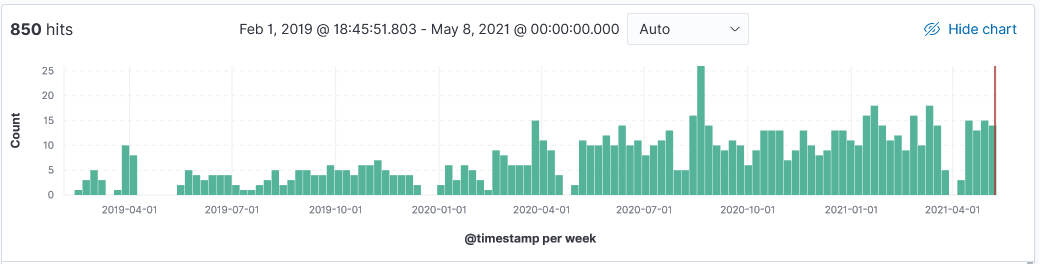
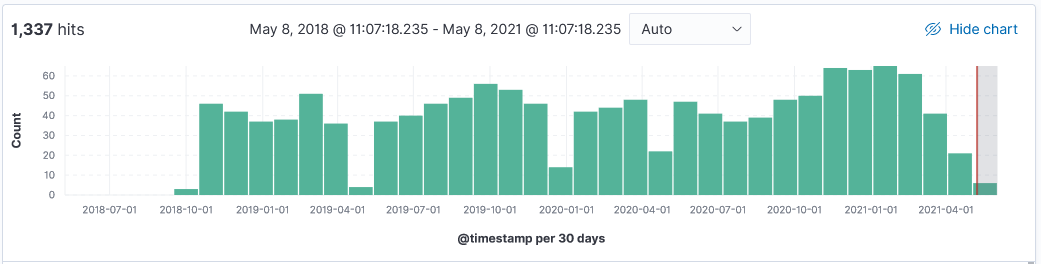
Over the past 3 years, my honeypot has logged information at various point in times from these 4 different research organizations. Here are some typical logs and their top 10 IPs. Shodan uses IP range 71.6.128.0-71.6.255.255 to run its scans but unlike other scanners, it doesn't include a banner in the captured logs.
Activity first noticed 4 June 2018. This is a sample log:
20210507-171447: 192.168.25.9:80-71.6.158.166:34476 data
GET / HTTP/1.1
Accept-Encoding: identity
Host: xxxxxx.xxx.ca
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.36
Activity first noticed 19 Aug 2020. This is a sample log:
20210506-011443: 192.168.25.9:80-162.142.125.38:46726 data
GET / HTTP/1.1
Host: 70.55.XX.XXX:8080
User-Agent: Mozilla/5.0 (compatible; CensysInspect/1.1; +https://about.censys.io/)
Accept: */*
Accept-Encoding: gzip
Activity first noticed 15 Feb 2019. This is a sample log:
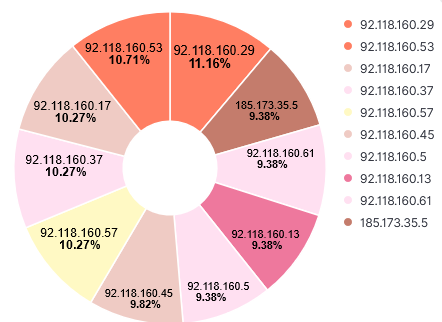
20210506-013155: 192.168.25.9:8443-92.118.160.5:47195 data
GET / HTTP/1.1
Host: 70.55.XX.XXX:8443
User-Agent: NetSystemsResearch studies the availability of various services across the internet. Our website is netsystemsresearch.com
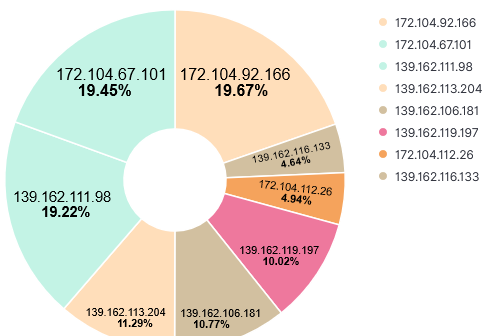
Activity first noticed 14 Oct 2018 data. This is a sample log:
20210506-082116: 192.168.25.9:81-172.104.67.101:42966
GET / HTTP/1.1
Host: 70.55.XX.XXX:81
User-Agent: HTTP Banner Detection (https://security.ipip.net)
Connection: close
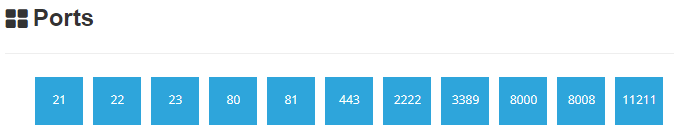
Since the data is already out there, why not use Shodan or Censys to explore what services a home router is sharing to the internet. Here is an example of list of services recorded and audited by Shodan which also includes SSL certificate information, banner version, etc.
[1] https://www.shodan.io
[2] https://censys.io/ipv4
[3] https://isc.sans.edu/forums/diary/An+Alternative+to+Shodan+Censys+with+UserAgent+CensysInspect11/26718
[4] http://www.netsystemsresearch.com
[5] https://security.ipip.net/
[6] https://isc.sans.edu/ipinfo.html?ip=71.6.158.166 (Shodan RESEARCHER: THIS IP IS USED FOR INTERNET WIDE RESEARCH SCANS)
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
.PNG)


Comments