PacketSifter as Network Parsing and Telemetry Tool
I saw PacketSifter[1], a new package on Github and figure I would give it a try to test its functionality. It is described as "PacketSifter is a tool/script that is designed to aid analysts in sifting through a packet capture (pcap) to find noteworthy traffic. Packetsifter accepts a pcap as an argument and outputs several files." It is less than a month old, initial release 31 Dec 2020 and last update 22 days ago.
What I found interesting about this tool is the fact that is uses various tshark filters to parse the information into various types of statistics (conversations & endpoints) such as IP, TCP, HTTP presenting the data in a way that can easily understood and easily search the data using various regex tools. I use Elasticsearch to collect, parse and analyze my logs but I also see PacketSifte as an alternative to quickly summarize packet data.
The result of the dns.pcap was a list of malformed DNS packets and the http.pcap was all the web traffic saved into a single file.
One of the requirements for this tool is you need to have tshark installed. My test was done with the latest version of CentOS 7.
Download the Tool from Github which also contains the VirusTotal Setup File. Ensure the system meets the following requirements:
$ git clone https://github.com/packetsifter/packetsifterTool.git
$ cd packetsifterTool
$ chmod 555 packetsifter.sh
$ sh VTInitial.sh
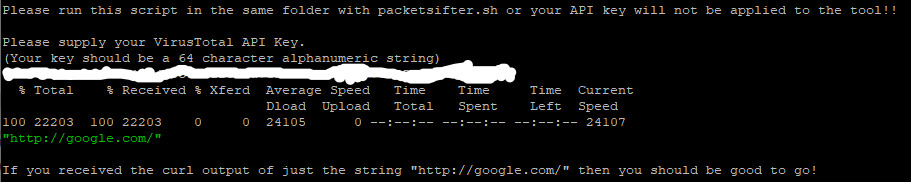
Note: This file only contains web and DNS traffic
$./packetsifter.sh ../honeypot-2021-Jan-29-19-25-42.pcap
- Would you like to resolve host names observed in pcap? This may take a long time depending on the pcap!!
<<Warning>> This can result in DNS queries for attacker infrastructure. Proceed with caution!!
(Please supply Y for yes or N for no) N
http.pcap contains all conversations containing port 80,8080,8000
Running as user "root" and group "root". This could be dangerous.
- Would you like to export HTTP objects? The objects will be outputted to a tarball in the current directory titled: httpObjects.tar.gz
<<Warning>> There could be a lot of HTTP objects and you can potentially extract malicious http objects depending on the pcap. Use with caution!!
(Please supply Y for yes or N for no) Y
- Would you like to lookup exported HTTP objects using VirusTotal?
**Warning** You must have ran the VTinitial.sh script to initialize PacketSifter with your VirusTotal API Key.
(Please supply Y for yes or N for no) Y
################# SMB SIFTING #################
Stats on commands ran using smb or smb2 has been generated and is available in: SMBstatistics.txt
No SMB traffic found. Deleting arbitrary SMBstatistics.txt
smb.pcap contains all conversations categorized by tshark dissectors as NBSS, SMB, or SMB2
Running as user "root" and group "root". This could be dangerous.
No SMB traffic found. Deleting arbitrary smb.pcap.
- Would you like to export SMB objects? The objects will be outputted to a tarball in the current directory titled: smbObjects.tar.gz
<<Warning>> There could be a lot of SMB objects and you can potentially extract malicious SMB objects depending on the pcap. Use with caution!!
(Please supply Y for yes or N for no) N
################# DNS SIFTING #################
dns.pcap contains all conversations categorized by tshark dissectors as DNS
Running as user "root" and group "root". This could be dangerous.
DNS A query/responses have been outputted to dnsARecords.txt
No DNS A records found. Deleting arbitrary dnsARecords.txt
DNS TXT query/responses have been outputted to dnsTXTRecords.txt. DNS TXT records can be used for nefarious reasons and should be glanced over for any abnormalities.
No DNS TXT records found. Deleting arbitrary dnsTXTRecords.txt
################# FTP SIFTING #################
ftp.pcap contains all conversations categorized by tshark dissectors as FTP
Running as user "root" and group "root". This could be dangerous.
No FTP traffic found. Deleting arbitrary ftp.pcap
Packet sifting complete! Thanks for using the tool.
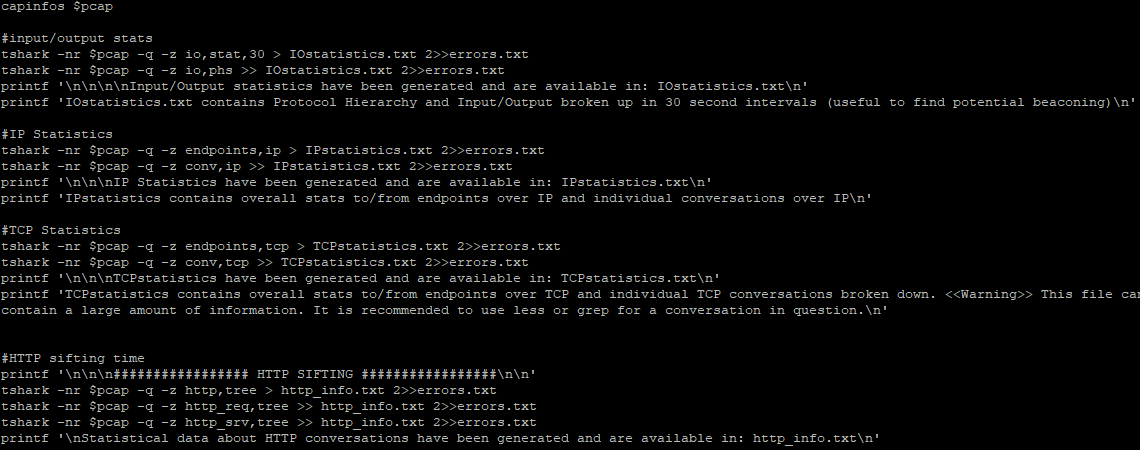
After the tool completed its analysis, a total of 7 files are generated by the script: 2 pcap and 5 text
[guy@moonbase packetsifterTool]$ ls -1 *.txt && ls -1 *.pcap
- errors.txt
- http_info.txt
- IOstatistics.txt
- IPstatistics.txt
- TCPstatistics.txt
- dns.pcap
- http.pcap
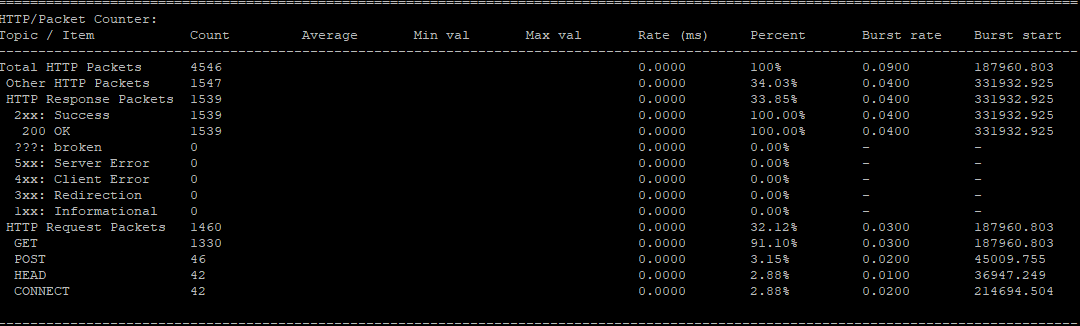
The script is using tshark to provide various statistics such as:
- HTTP/Packet Counter
- HTTP/Requests
- HTTP/Load Distribution
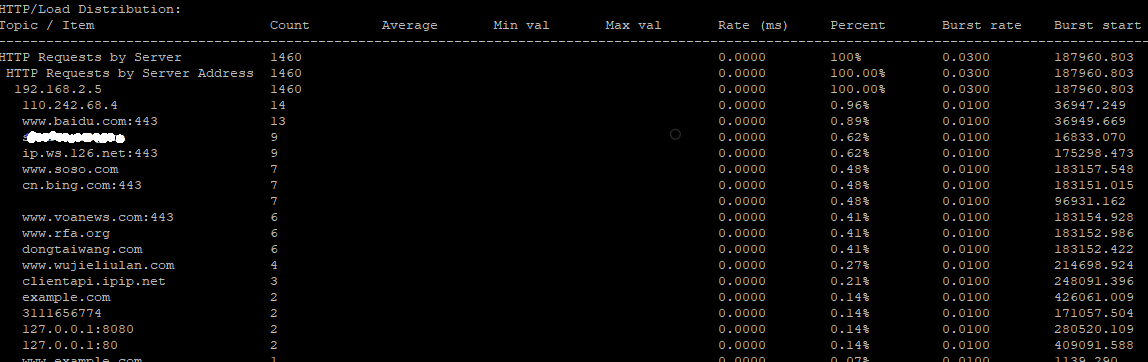
- HTTP Responses by Server Address
- TCP Endpoint Statistics
- IP Endpoint Statistics
It extract all the web object into this file: httpObjects.tar.gz
$ tar zxvf httpObjects.tar.gz
$ cd httpObjects
This script is fast going through the pcap file, however, there is a warning for "Would you like to resolve host names observed in pcap?". The first time I said yes and that basically stopped the script while it was trying to resolve hostnames and eventually cancelled the script and re-ran without it.
Overall, this script is easy to use and another tool that can easily be used for analysis of pcap traffic for web, DNS and SMB objects which I didn't have in this file.
Happy hunting!
[1] https://github.com/packetsifter/packetsifterTool.git
[2] https://www.wireshark.org
[3] https://tshark.dev/setup/install/
[4] https://www.virustotal.com/gui//
[5] https://www.elastic.co
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu



Comments