Attacking NoSQL applications (part 2)
Last week I was lucky enough to attend SANSFIRE, which is one of the biggest SANS events (I attended the SEC660 course by Tim Medin – and just as my personal opinion: this is probably the best course I have ever attended).
I also held a presentation about attacking NoSQL applications, which was based partially on some previous research I did and the diary I posted in December (you can find it here).
As I demonstrated previously, depending on how developers handle user input, certain attacks are possible against NoSQL databases.
The attack from the previous diary included modification of a parameter that allowed us to retrieve arbitrary data from the database: in order to do this we used the $regex operator so we did not have to brute force the GUID’s but instead simply guess characters one by one. The search operator we used was this:
{ friendly: { $regex: "^a" } }
This will return the first document from a collection where the friendly key matches the $regex operator that we have entered. Going further is easy, here is our next try:
{ friendly: { $regex: "^ab" } }
This way we can retrieve documents one by one and slowly guess their GUID. Additionally, we don’t have to guess the whole sequence. For example, if the $regex operator /a9577050-31cf-11e6-957b-43a/ and /a9577050-31cf-11e6-957b-43a5/ return the same document, we know this is the “last” one with that particular sequence.
Now the question is on how to expand the attack to retrieve additional documents? Once we know a GUID that belongs to the document we retrieved, we can (again) use NoSQL’s powerful operators to simply exclude that document, as in the example below:
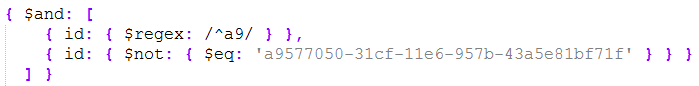
Here we have an $and operator that simply retrieves another document whose GUID starts with /^a9/ but excludes the one that we just retrieved. This allows us to “blocklist” retrieved documents and continue enumeration of the collection.
This again shows that the default mantra with any application should be: never trust and always sanitize any user input you get, no matter what you use in the background.
We will also publish all handler presentations from SANSFIRE soon, so stay tuned.
| Web App Penetration Testing and Ethical Hacking | London | Mar 2nd - Mar 7th 2026 |


Comments