New variant of CryptoWall - Is it right to call it 4.0?
Introduction
Earlier this week, I saw the most recent variant of CryptoWall as a payload delivered by the Angler exploit kit (EK) [1]. Many people, including me, have been calling this new variant "CryptoWall 4.0." However, version 4.0 is not the most accurate term for this ransomware. So why are we calling it that?
Background
On 2015-11-03, BleepingComputer published an article about this new CryptoWall variant, calling it CryptoWall 4.0 [2]. It had some notable changes from the previous variant. The next day on 2015-11-04, someone else pointed out this new variant didn't refer to itself as version 4.0. Instead, it appeared to be 3.0.1b034 build 0078 [3].
However, many security sites followed BleepingComputer's lead, calling the malware "CryptoWall 4.0" [4, 5, 6, 7, 8 to name a few]. I even called it 4.0 in my previous ISC diary, back when I saw this new variant appear in Nuclear EK traffic [9].
A few sites haven't called it 4.0, though. Instead, they have merely noted this is a new variant [10, 11]. However, the vast majority of people have reported the new CryptoWall variant as 4.0.
The case against 4.0
Until now, CryptoWall has been specific in its version numbers. Since the original CryptoWall moved to version 2.0, the group behind CryptoWall has always stated the version number in the decryption instructions. We noticed this from CryptoWall to CryptoWall 2.0. We also saw it when 2.0 went to 3.0. If they haven't indicated so, the people behind CryptoWall apparently don't believe their recent changes are enough to warrant the version 4.0 moniker.
The case for 4.0
Even though CryptoWall's authors are not calling it 4.0, the changes in this new variant are quite noticeable. From a network traffic standpoint, we don't see the malware check an external site for the infected host's IP address. Other changes are also notable--the notification text has changed, the names of the notification files are different, and the file names of your encrypted files are also encrypted. This is a significant change in CryptoWall.
So what's the best way to let people know about the new CryptoWall? How can you get someone's attention? You can give it a new name, or perhaps a new spin on the same name. The 4.0 designation may be inaccurate from the malware authors' view; however, it's a good way for us as defenders to identify the new variant. For example, Bitdefender explained to SecurityWeek.com that it assigned the 4.0 designation to signal a new version of the CryptoWall threat [12].
The changes from 3.0 to "4.0"
Below are the major changes in the newest variant of CryptoWall:
- "4.0" has no more IP address check to ip-addr.es like there was in CryptoWall 3.0.
- Decryption instructions in "4.0" state it's "CryptoWall" instead of "CryptoWall 3.0"
- CryptoWall 3.0 files for decrypt instructions are named HELP_DECRYPT (.TXT, .PNG, etc.)
- CryptoWall "4.0" files for decrypt instructions are named HELP_YOUR_FILES (.TXT, .PNG, etc.)
- CryptoWall "4.0" also encrypts the file names of the files it encrypts. CryptoWall 3.0 doesn't change the file names.
The images below illustrate some of the changes.
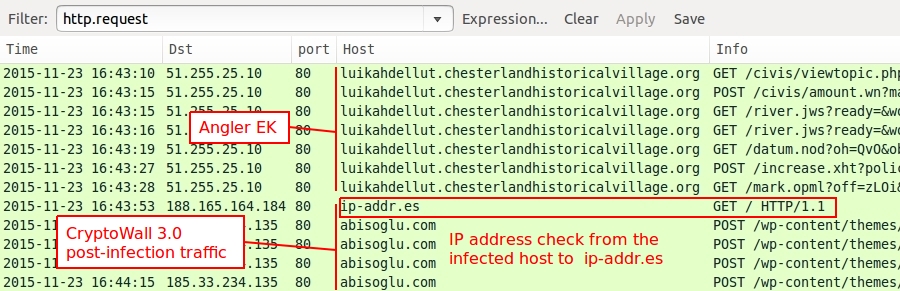
Shown above: CryptoWall 3.0 traffic, filtered in Wireshark, with an IP address check to ip-addr.es.
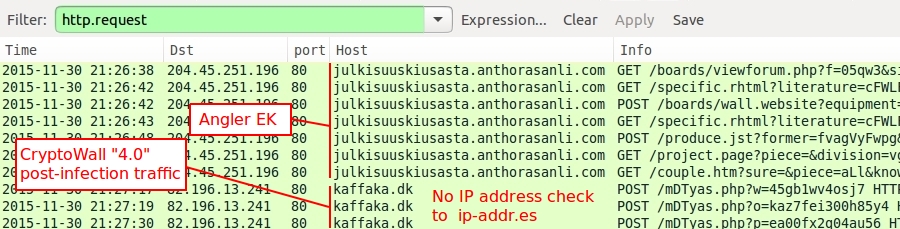
Shown above: CryptoWall "4.0" traffic, filtered in Wireshark, without the IP address check to ip-addr.es.
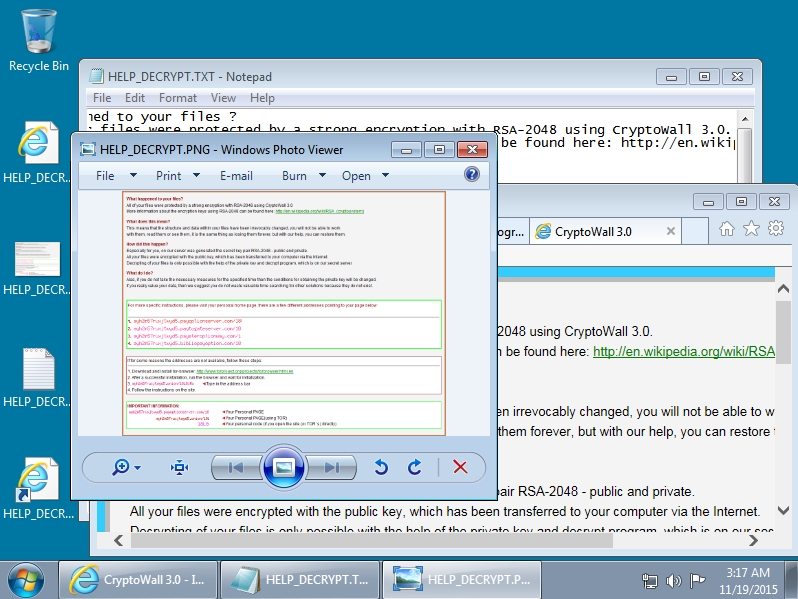
Shown above: Windows desktop after a CryptoWall 3.0 infection.
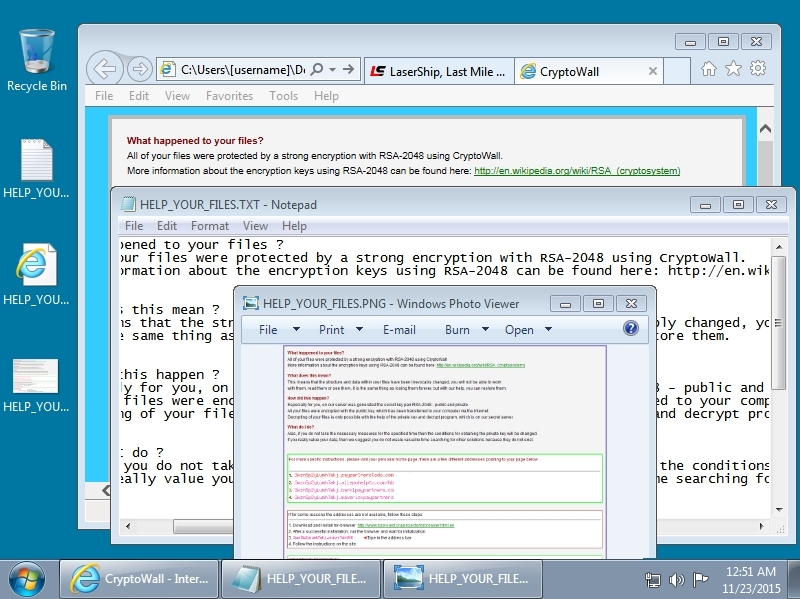
Shown above: Windows desktop after a CryptoWall "4.0" infection (malware from BizCN gate actor using Nuclear EK).

Shown above: Windows desktop after a CryptoWall "4.0" infection (malware from another actor using Angler EK).
Final words
I've discussed this CryptoWall version issue with other security professionals. Most have told me CryptoWall 4.0 is a good way to refer to this new variant, at least for now.
However, I like to be precise. Calling this a new CryptoWall variant is okay. In fact, we should probably forget version numbers when referring to CryptoWall, at least for now.
My most recent sample of this new variant of CryptoWall, delivered by Angler EK, can be found here.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://www.malware-traffic-analysis.net/2015/11/30/index.html
[2] http://www.bleepingcomputer.com/news/security/cryptowall-4-0-released-with-new-features-such-as-encrypted-file-names/
[3] https://twitter.com/ydklijnsma/status/662041531185012736
[4] http://www.theregister.co.uk/2015/11/09/cryptowall_40/
[5] https://heimdalsecurity.com/blog/security-alert-cryptowall-4-0-new-enhanced-and-more-difficult-to-detect/
[6] https://threatpost.com/updated-cryptowall-encrypts-file-names-mocks-victims/115285/
[7] http://labs.bitdefender.com/2015/11/russian-hackers-are-behind-cryptowall-4-0-bitdefender-creates-vaccine/
[8] http://www.scmagazine.com/version-40-of-ransomware-cryptowall-released-now-encrypts-file-names/article/452036/
[9] https://isc.sans.edu/forums/diary/BizCN+gate+actor+sends+CryptoWall+40/20409/
[10] https://nakedsecurity.sophos.com/2015/11/06/cryptowall-ransomware-new-strains-demands-money-and-mocks-you/
[11] http://countuponsecurity.com/2015/11/07/cryptowall-strikes-back/
[12] http://www.securityweek.com/cryptowall-40-released-filename-encryption-feature


Comments
https://malwr.com/analysis/MjczNDcwYWUzYWI5NDk5YTlmMzAxN2FmNmNkY2U2YzU/
https://malwr.com/analysis/YTdmYWJkY2E5ZDI0NGExMWJmNTgzOGM4OWY2NTMzOGI/
every answer will be appreciated.
Regards
Anonymous
Dec 3rd 2015
1 decade ago
https://malwr.com/analysis/MjczNDcwYWUzYWI5NDk5YTlmMzAxN2FmNmNkY2U2YzU/
https://malwr.com/analysis/YTdmYWJkY2E5ZDI0NGExMWJmNTgzOGM4OWY2NTMzOGI/
every answer will be appreciated.
Regards[/quote]
Those files submitted to malwr.com are .js files designed to download the CryptoWall executable. If you get a copy of the CryptoWall executable, it works just fine on Cuckoo sandbox. Here's what I got from my latest sample of CryptoWall "4.0":
https://malwr.com/analysis/ODM4MjAyZjIyYzRmNDVmNDlhZTE0NWJmMzU2NDQyZWM/
Anonymous
Dec 3rd 2015
1 decade ago
01 Dec 2015 - "... first time we’ve seen tech support scams running in tandem with the Nuclear exploit kit to deliver ransomware and if this proves to be an effective combination, we are likely to see more of this in the future..."
:-(
Anonymous
Dec 3rd 2015
1 decade ago