Searching Through the VirusTotal Database
Now that my overview of Sysinternals tools with VirusTotal support is complete (Process Explorer, Autoruns and Sigcheck), let's address a couple of remarks I received (BTW, if I missed a Sysinternals tools, let me know with a comment).
1) Upload of files. Some people are worried that the Sysinternals tools will upload (confidential) files to VirusTotal. That is a valid concern, but for each tool I described, I showed how to enable hash searching first. Configured like this, the Sysinternals tools will only submit hashes to VirusTotal, and not upload files. The Sysinternals tools can upload files, but this has to be done manually (Process Explorer) or configured explicitly (Autoruns and Sigcheck).
2) Internet access. It is obvious that these tools require Internet access to connect to VirusTotal (BTW, if you have a proxy, read the comments for Process Explorer). But that is not always possible or desirable. Several years ago, I needed a tool to search through the VirusTotal database for a list of MD5 hashes. At that time, I found no programs or scripts that searched the VirusTotal database via the API (though there were scripts to submit files, but not search). Thus I wrote my own tool: virustotal-search.py. You need to obtain a VirusTotal API key to use with virustotal-search.py (create a free VirusTotal account and you'll get one). And then you let virustotal-search.py run with a list of search terms (MD5, SHA1 or SHA256 hashes) and it will produce a CSV file with the results. This will take some time, as virustotal-search.py respects VirusTotal's quota for free accounts: 4 requests per minute and maximum 4 search terms per request. I won't go into al the features of virustotal-search, if you are interested, visit my virustotal-search page. Here is an example of a CSV file produced by virustotal-search.py:
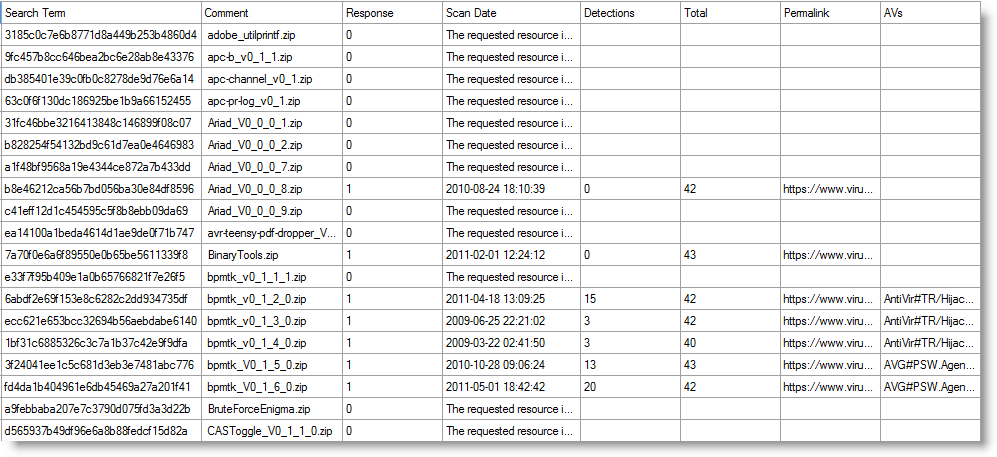
In an upcoming diary entry, I'll give some pointers to produce lists of hashes (tip: some Sysinternals tools can calculate hashes).
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments
Anonymous
Jul 21st 2015
1 decade ago
A database of good software.
Anonymous
Jul 21st 2015
1 decade ago