MacDefender ups the ante with removing the password need for installation
MacDefender, malware posing as security software that targets Mac OS X, and to which only days ago Apple had responded with instructions and a promise of an OS X update to eradicate the threat, has upped the ante with a new version according to Intego that does not need to ask the user's password any longer.
No, it's not using an exploit to avoid asking the right to write in the /Applications directory, it simply installs the software and activates it for the current user only. Since most macs are using only a single user that changes little for the malware. But it removes the pop-up for your password. Anybody in the admin group can write to the /Applications directory:
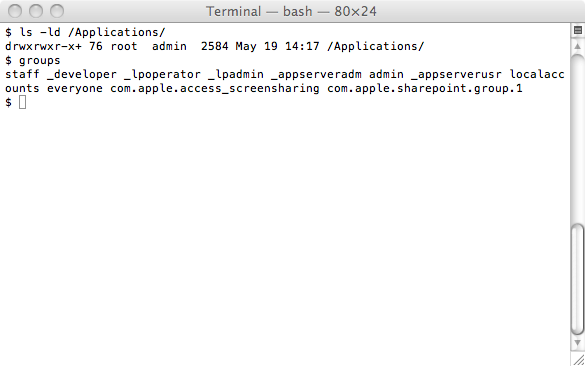
So they do not need to use the graphical sudo functionality as long as you're in the admin group (something administrator accounts are).
Not typing your password when you did not ask for software to be installed was one of those simple rules to explain to the users, guess we're now down to those much harder to explain instructions for our users.
--
Swa Frantzen -- Section 66


Comments
If the Mac O/S has diverted that far from its roots (pun unintended) that a normal user requires sudo for normal every day acitvities then its security model is as broken as windows ever was - That is everyone ends up running as an administrator because "otherwise it doesn't work".
djsmiley2k
May 26th 2011
1 decade ago
<UserName>ADMIN- Administrator
<UserName> regular user.
if you are in the admin group on the mac you will need to sudo +passwd for certain root level task. If you are a regular user, again certain root level task. What is more interesting about this is that the criminals are using methods similar to past PC attacks.
The installer, which is very small and portable can be moved around, IP changed etc. by someone very easy without need to alter the major application. Which we know the download file is about 1.8 megs give of take after avRunner does its thing. So they commoditize the criminal activity and may it more module.
Again, seems criminals are better at code re-use, since their motivation, dollars is not far removed.
Again, thanks for this write up. Better to get facts then chase stories. We think the risk is still low. However this is a very effective scam due to the user base skill set and mis guided marketing, namely trust your computer at all cost without any verification.
drStrangeP0rk
May 26th 2011
1 decade ago
Even with the removal of the password prompt, you still have to go through the install process, which requires several clicks to complete. If you are seriously that lame, and blindly click through an installation of something you did not purposely download, then you get what you deserve.
As an avid Mac/Unix guy...I still feel this amounts to jumping through hoops to get the badware installed. They are going to still have to do better if they want to trick me.
TTFN
HackDefendr
May 26th 2011
1 decade ago
This can largely be avoided with user education, but I guess the criminals are already hard at work figuring out how to do drive-by downloads on OS X.
tw
May 30th 2011
1 decade ago