Phishing HTML Attachment as Voicemail Audio Transcription
I have been seeing this form of phishing in Microsoft Office 365 for several weeks. The email comes in as an attachment like this with a phone icon preceding it:
I saved a copy of the file to examine its content in CyberChef which decoded the top part of the HTML file showing the target email address (I replaced it) with the URL the HTML will open to:
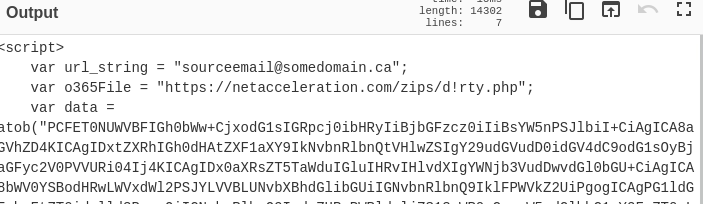
The URL actually has an error where d!irty (where the exclamation mark is an i) is actually dirty. I moved the code up in the Input to decode the base64 content and the decoded text has error checking for empty or to short password: "Your account password cannot be empty. If you don't remember your password reset it now"
Analysis of the file if opened would look like this:
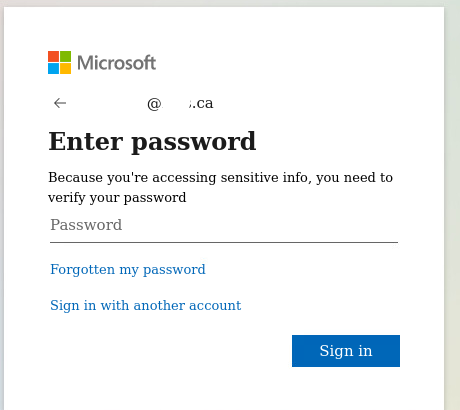
Indicator
netaccelaration[.]com/zips/dirty.php
netaccelaration[.]com/zips/d!rty.php
[1] https://gchq.github.io/CyberChef/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu



Comments