TShark & jq
TShark (Wireshark's command-line version) can output JSON data, as shown in diary entry "Quicktip: TShark's Options -e and -T".
jq is a JSON processor, that I've shown before in diary entries like "Retrieving and processing JSON data (BTC example)".
In this diary entry, I will show how to use tshark and jq to produce a list of unique IPv4 addresses.
This tshark command reads a capture file and produces JSON output for the ip.src field:
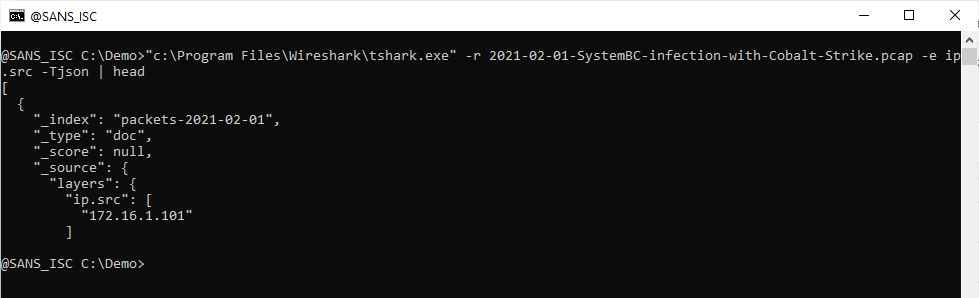
This JSON data is an array of dictionaries. To read and start processing this JSON data, I pipe the output to jq and use a filter to iterate over the array: .[]
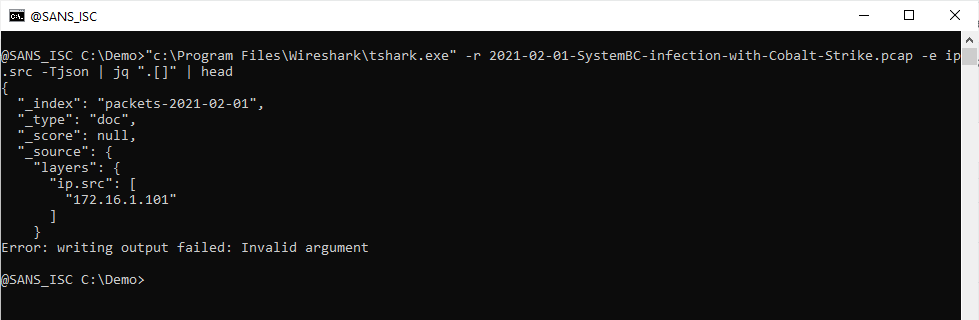
Next I pipe this iteration output into ._source to select values for key _source:
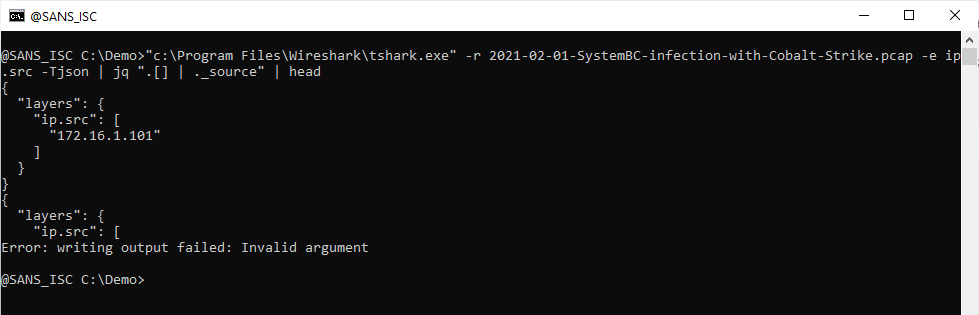
And I do the same for keys layers and ip.src:
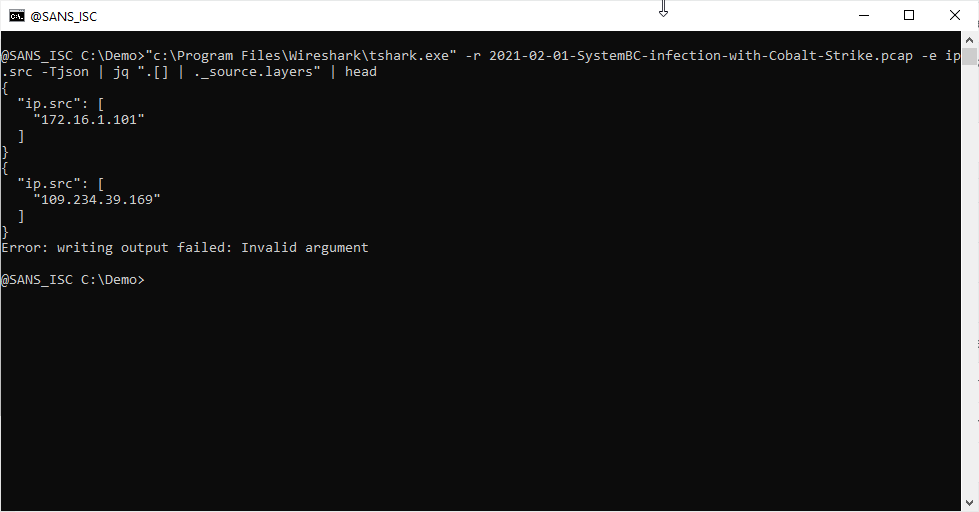
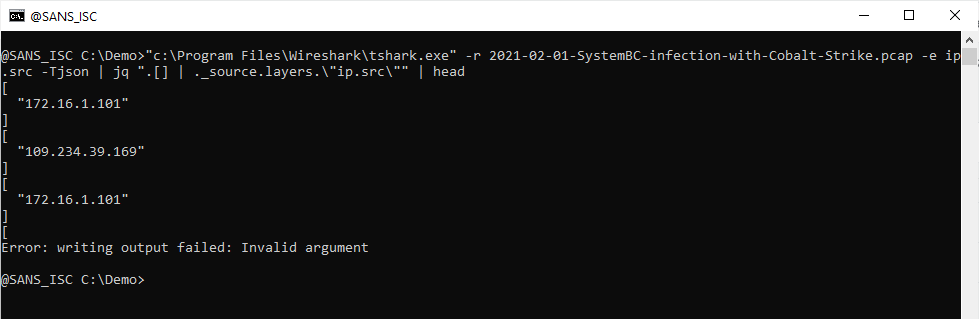
For ip.src, remark that this key contains a dot (.), and a dot has special meaning in jq filters: it's an operator. Thus, I need to escape it, like this: \"ip.src\".
Now I have an iteration of arrays, each one containing an IPv4 address. I index this array to select the first IPv4 address:
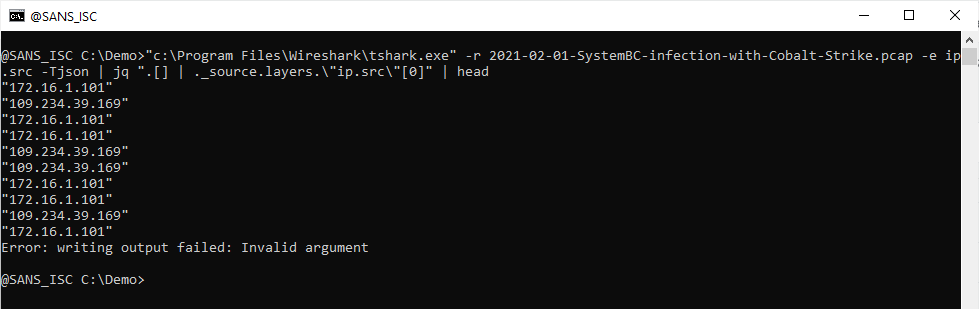
Remark that there can be more than on ip.src address inside a single packet, I will discuss this in an upcoming diary entry.
Next, I put this iteration of IPv4 addresses (strings, actually) into an array:
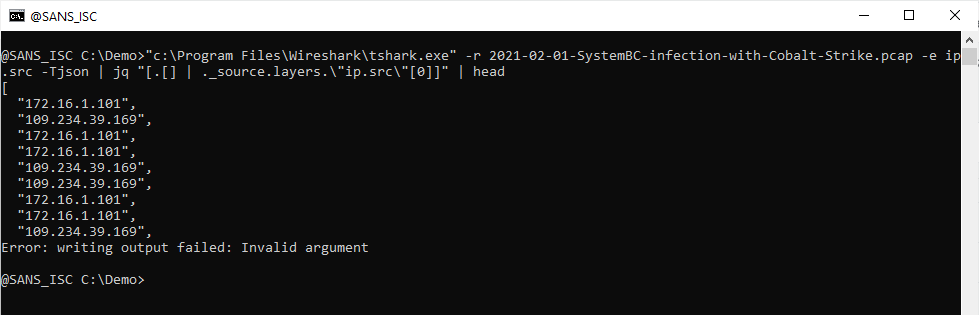
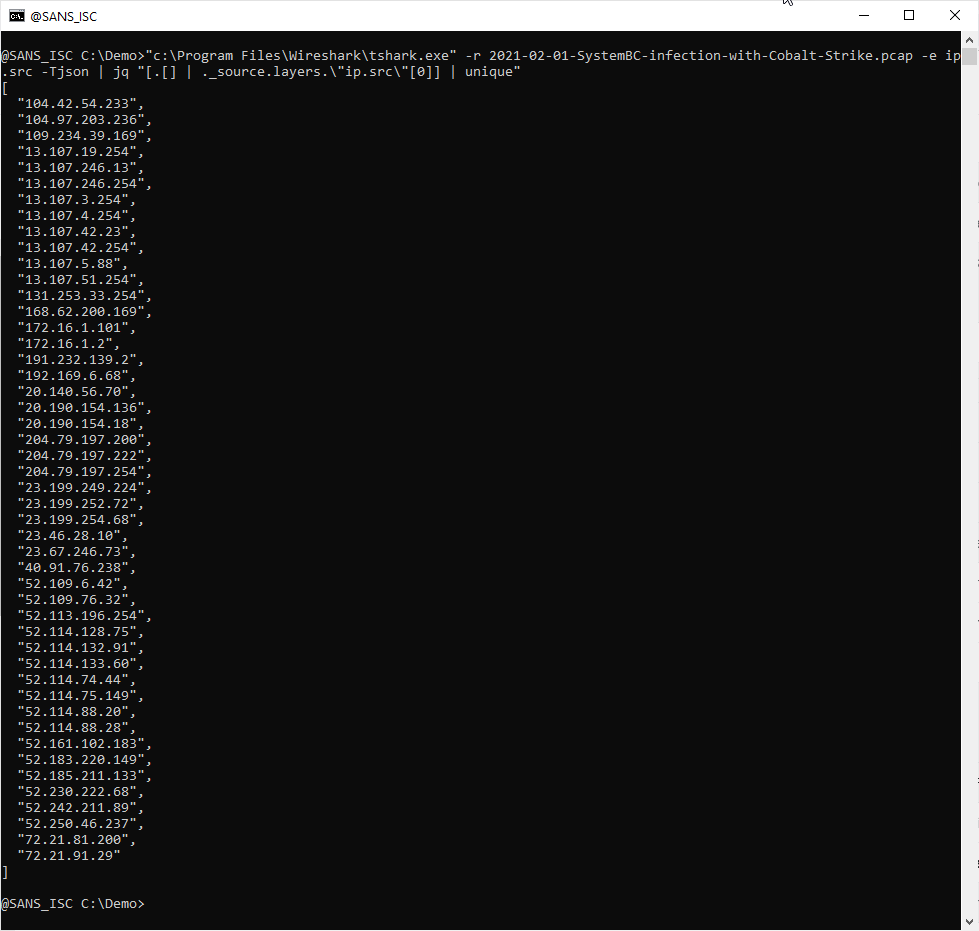
And now that I have an array of IPv4 addresses, I can pipe it into function unique to produce an array where each IPv4 address is unique (e.g., appears only once):
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments