Example of Cleartext Cobalt Strike Traffic (Thanks Brad)
Brad has a large collection of malware traffic (thanks Brad :-) ).
I've been searching his collection for a particular sample, and I found one:
2019-07-25 - HANCITOR-STYLE AMADEY MALSPAM PUSHES PONY & COBALT STRIKE
What is special about this sample? Let me show you.
Open Brad's pcap file with Wireshark, go to File / Export Objects / HTTP ..., and sort the table by size, descending:
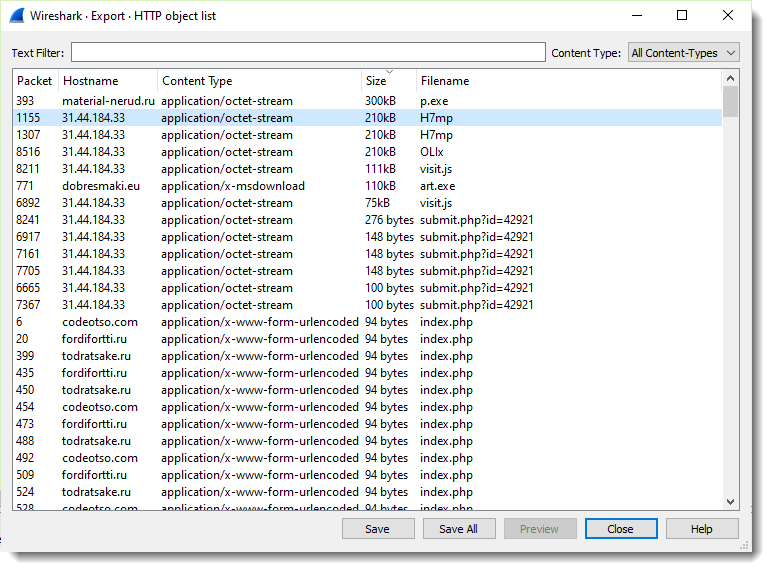
You see 3 filenames (H7mp, H7mp, OLIx). These are the Cobalt Strike beacons with a "checksum8 URL":
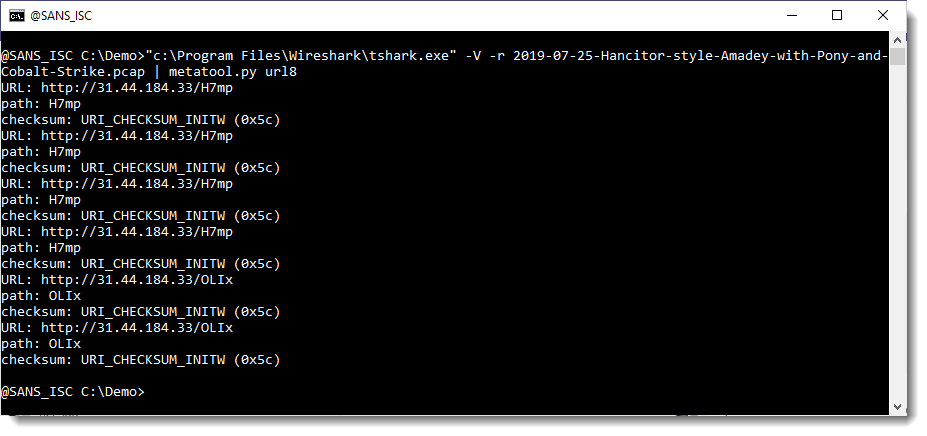
See my diary entry "Finding Metasploit & Cobalt Strike URLs" for more information.
Save one of the files to disk (the 3 files are identical) and analyze it with my tool 1768.py:
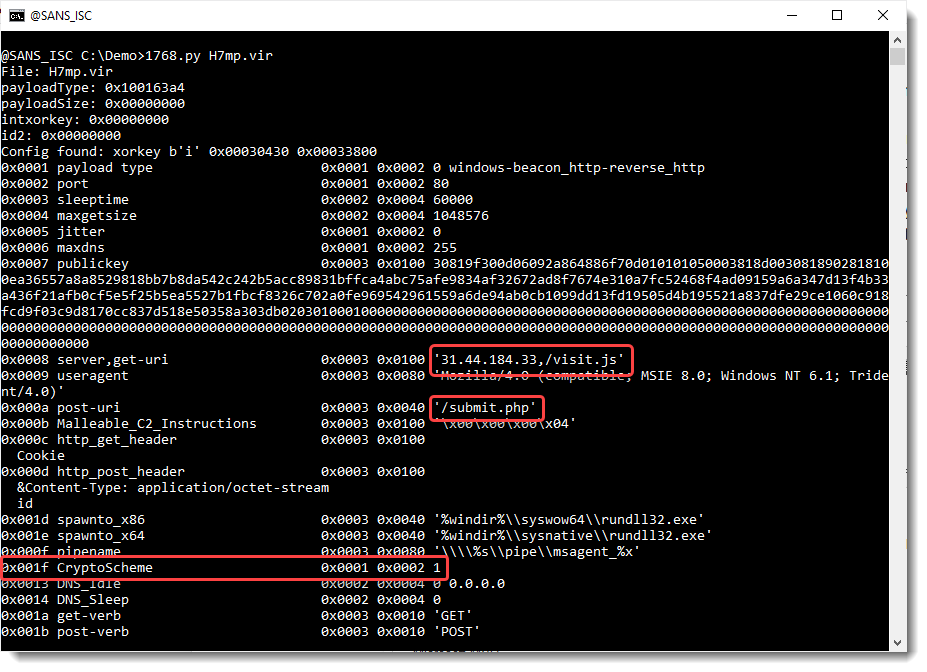
Notice that the value of CryptoScheme is 1: this means that this beacon (and the C2) will not encrypt their transmitted data with AES. Because encryption is disabled for trial versions.
And since the beacon communicates over HTTP, we can see cleartext traffic directly with Wireshark. For example, filter on "submit.php" requests:
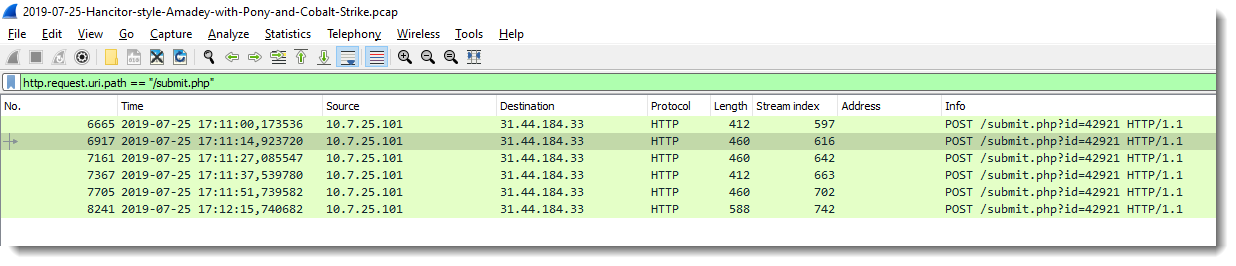
And follow the HTTP stream of the first request:
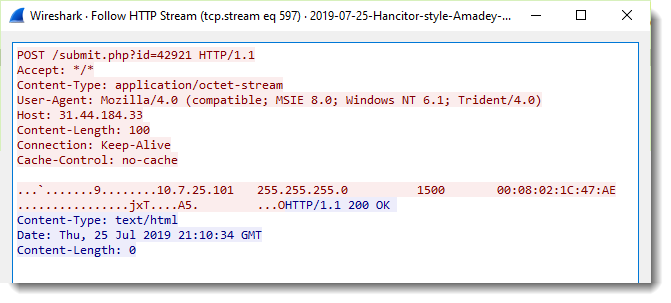
We can see strings that look like IPv4 config information: internal IPv4 address (10.7.25.101), network mask (255.255.255.0), MTU (1500) and MAC address (00:08:02:1C:47:AE).
Isn't that nice? :-)
If you like looking through pcap files, like we handlers do, I invite you to find more unencrypted Cobalt Strike traffic in Brad's pcap file, and share your comments here.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments